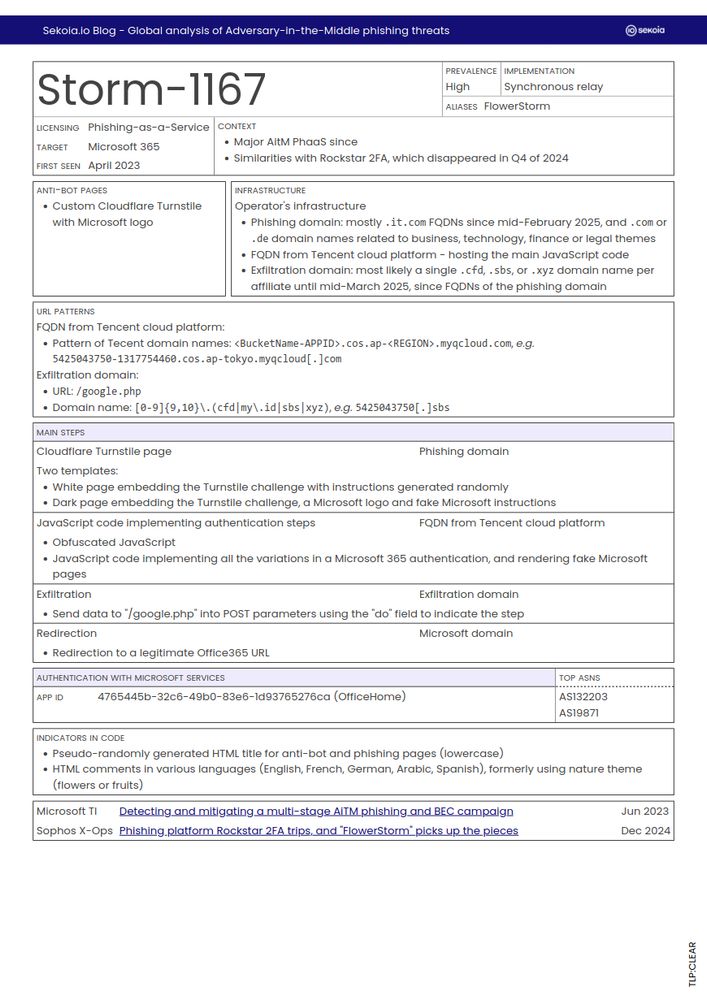
Sekoia #TDR analysed a recent #Calisto (aka #ColdRiver #Star Blizzard) spear-phishing campaign aimed at Reporters sans frontières and other #Ukraine-supporting organisations.
blog.sekoia.io/ngo-reporter...

Sekoia #TDR analysed a recent #Calisto (aka #ColdRiver #Star Blizzard) spear-phishing campaign aimed at Reporters sans frontières and other #Ukraine-supporting organisations.
blog.sekoia.io/ngo-reporter...
@uybhys.bsky.social




@uybhys.bsky.social
blog.sekoia.io/phishing-cam...

blog.sekoia.io/phishing-cam...
blog.sekoia.io/polaredge-ba...

blog.sekoia.io/polaredge-ba...
Vous aimez faire des règles #Sigma et #Yara ? Vous adorez pivoter et traquer les infrastructures (C2) d’attaques des cybercriminels ?
Alors cette offre d’emploi est faite pour vous !
www.welcometothejungle.com/en/companies...

Vous aimez faire des règles #Sigma et #Yara ? Vous adorez pivoter et traquer les infrastructures (C2) d’attaques des cybercriminels ?
Alors cette offre d’emploi est faite pour vous !
www.welcometothejungle.com/en/companies...
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable

✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...

Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...
blog.sekoia.io/apt28-operat...

blog.sekoia.io/apt28-operat...
➡️ blog.sekoia.io/predators-fo...
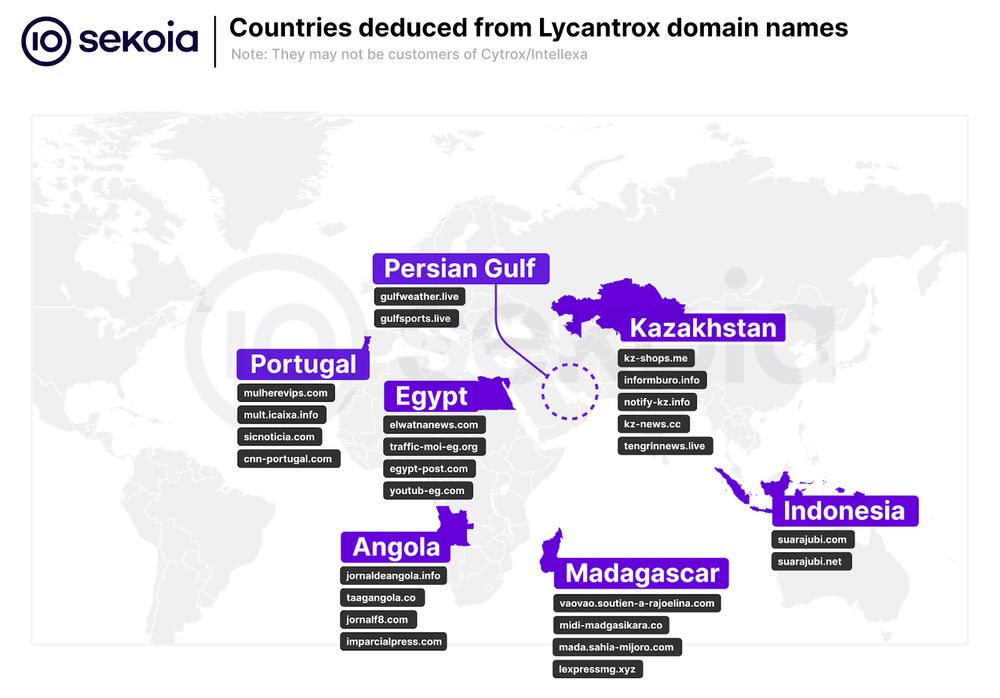
➡️ blog.sekoia.io/predators-fo...
Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.

Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.
And on our Community GitHub: github.com/SEKOIA-IO/Co...
And on our Community GitHub: github.com/SEKOIA-IO/Co...
blog.sekoia.io/the-sharp-ta...

blog.sekoia.io/the-sharp-ta...
blog.sekoia.io/vicioustrap-...

blog.sekoia.io/vicioustrap-...
blog.sekoia.io/detecting-mu...

blog.sekoia.io/detecting-mu...
blog.sekoia.io/interlock-ra...

blog.sekoia.io/interlock-ra...
www.sekoia.io/en/presse/se...

www.sekoia.io/en/presse/se...
blog.sekoia.io/clickfake-in...

blog.sekoia.io/clickfake-in...

cc @plebourhis.bsky.social @sekoia.io
1. ClearFake framework is injected on compromised WordPress and relies on EtherHiding
2. The #ClickFix lure uses a fake Cloudflare Turnstile with unusual web traffic
⬇️

cc @plebourhis.bsky.social @sekoia.io
1. ClearFake framework is injected on compromised WordPress and relies on EtherHiding
2. The #ClickFix lure uses a fake Cloudflare Turnstile with unusual web traffic
⬇️
https://buff.ly/4ibOEo8

https://buff.ly/4ibOEo8