Nicolas Caproni
@caproni.fr
Head of Sekoia Threat Detection & Research (TDR) team • Cyber Threat Intelligence • Detection Engineering • SOC Platform 🇫🇷 🇪🇺 • Hip-Hop • Basketball
Reposted by Nicolas Caproni
Key takeaways:
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable

October 2, 2025 at 1:56 PM
Key takeaways:
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
Reposted by Nicolas Caproni
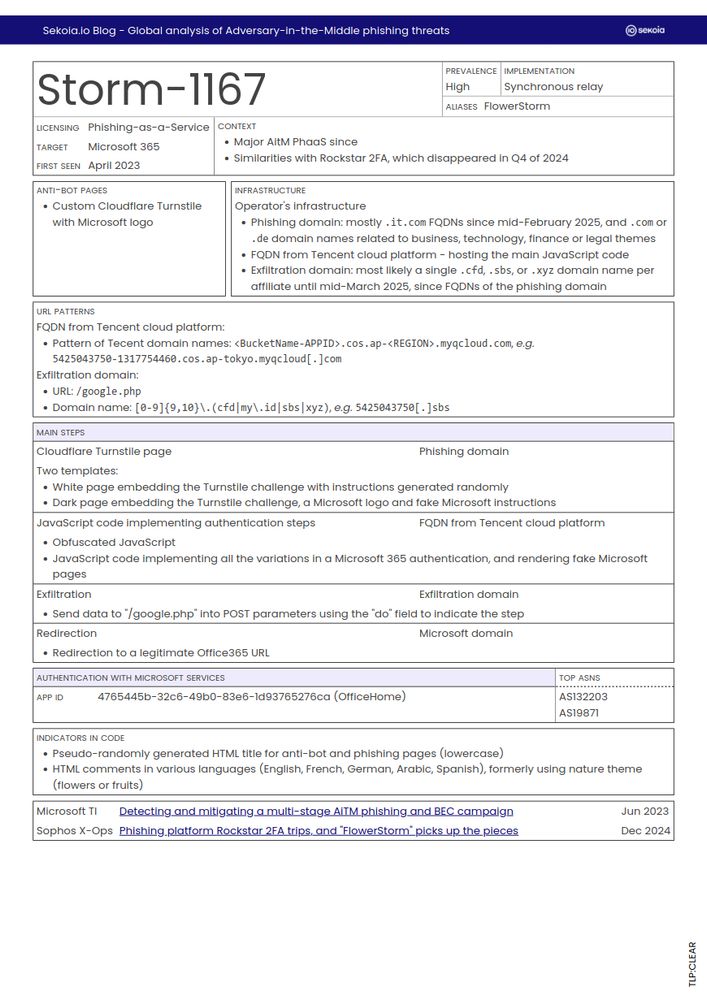
You can find the phishing kit sheets on our blog: blog.sekoia.io/global-analy...
And on our Community GitHub: github.com/SEKOIA-IO/Co...
And on our Community GitHub: github.com/SEKOIA-IO/Co...
July 8, 2025 at 7:53 AM
You can find the phishing kit sheets on our blog: blog.sekoia.io/global-analy...
And on our Community GitHub: github.com/SEKOIA-IO/Co...
And on our Community GitHub: github.com/SEKOIA-IO/Co...
Reposted by Nicolas Caproni