Former Senior RE @ FLARE.
www.binarydefense.com/resources/bl...

www.binarydefense.com/resources/bl...

The emails contained a password-protected RAR attachment with the malicious payload.
🧵⤵️
1) spoofing swisscom (note 'S', domain just reg'd)
2) leveraging encrypted rar + lnk + self signed pdf reader
3) BGP lure (fits with theme of email). BGP is the third leg in the outage triumvirate)
The emails contained a password-protected RAR attachment with the malicious payload.
@citizenlab.ca
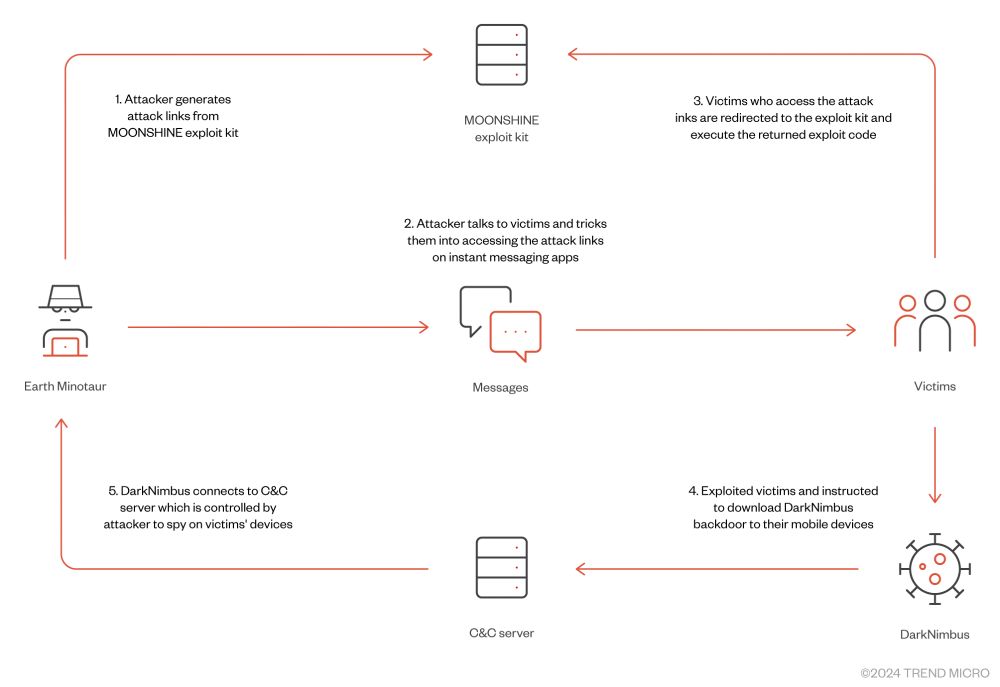
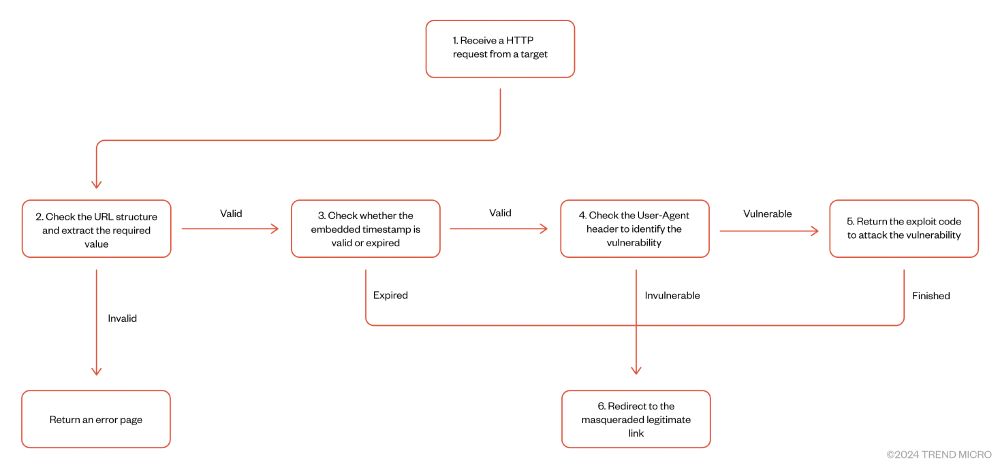
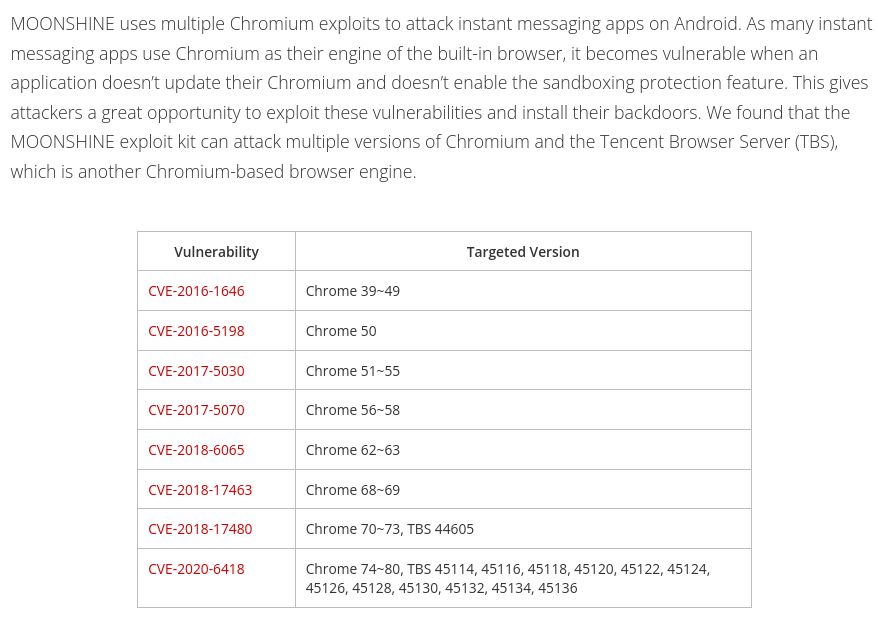
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
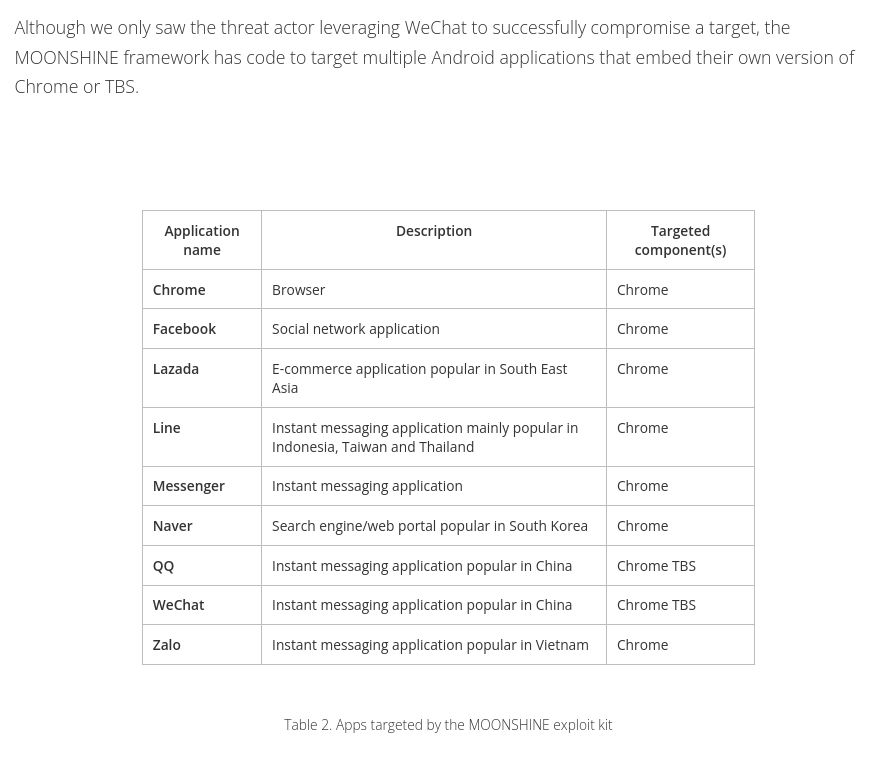
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
Read more here: www.volexity.com/blog/2024/11...

Read more here: www.volexity.com/blog/2024/11...