
www.proofpoint.com/us/blog/thre...
In 2024 we released two blogs on cybercrime actors using ClickFix in their attack chains:
www.proofpoint.com/us/blog/thre...
www.proofpoint.com/us/blog/thre...
Stellar work by @nickattfield.bsky.social and @threatray.bsky.social's researchers
A two-part blog series in collaboration with
@threatray.bsky.social, which aims to substantiate the claim that #TA397 (Bitter) is an espionage-focused, state-backed threat actor with interests aligned to the Indian state.
Part 1: brnw.ch/21wT9A5
Part 2: brnw.ch/21wT9Ad.

Stellar work by @nickattfield.bsky.social and @threatray.bsky.social's researchers
We observed DPRK actor TA406 (overlaps w/ Opal Sleet/Konni) targeting government entities in Ukraine in early 2025:
www.proofpoint.com/us/blog/thre...

We observed DPRK actor TA406 (overlaps w/ Opal Sleet/Konni) targeting government entities in Ukraine in early 2025:
www.proofpoint.com/us/blog/thre...

www.proofpoint.com/us/blog/thre...
In 2024 we released two blogs on cybercrime actors using ClickFix in their attack chains:
www.proofpoint.com/us/blog/thre...
www.proofpoint.com/us/blog/thre...

www.proofpoint.com/us/blog/thre...
In 2024 we released two blogs on cybercrime actors using ClickFix in their attack chains:
www.proofpoint.com/us/blog/thre...
www.proofpoint.com/us/blog/thre...
- Targeted the Turkish defense sector in Fall 2024
- Uses Alternate Data Streams in RAR archives
www.proofpoint.com/us/blog/thre...
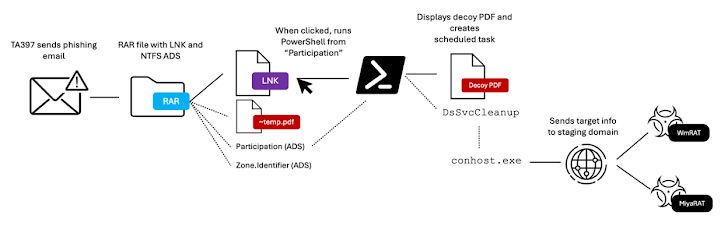
- Targeted the Turkish defense sector in Fall 2024
- Uses Alternate Data Streams in RAR archives
www.proofpoint.com/us/blog/thre...
The emails contained a password-protected RAR attachment with the malicious payload.
🧵⤵️
1) spoofing swisscom (note 'S', domain just reg'd)
2) leveraging encrypted rar + lnk + self signed pdf reader
3) BGP lure (fits with theme of email). BGP is the third leg in the outage triumvirate)
The emails contained a password-protected RAR attachment with the malicious payload.
@jacoblatonis.me and Tomas have gifted us with the YARA-X Macho module
the OG YARA macho parsing left a lot to be desired, and the new YARA-X ver has all sorts of goodies

@jacoblatonis.me and Tomas have gifted us with the YARA-X Macho module
the OG YARA macho parsing left a lot to be desired, and the new YARA-X ver has all sorts of goodies

