After a firmware downgrade, they found a debug shell via the access point used during setup, ultimately using this to gain EIP.
www.synacktiv.com/en/publicati...

After a firmware downgrade, they found a debug shell via the access point used during setup, ultimately using this to gain EIP.
www.synacktiv.com/en/publicati...
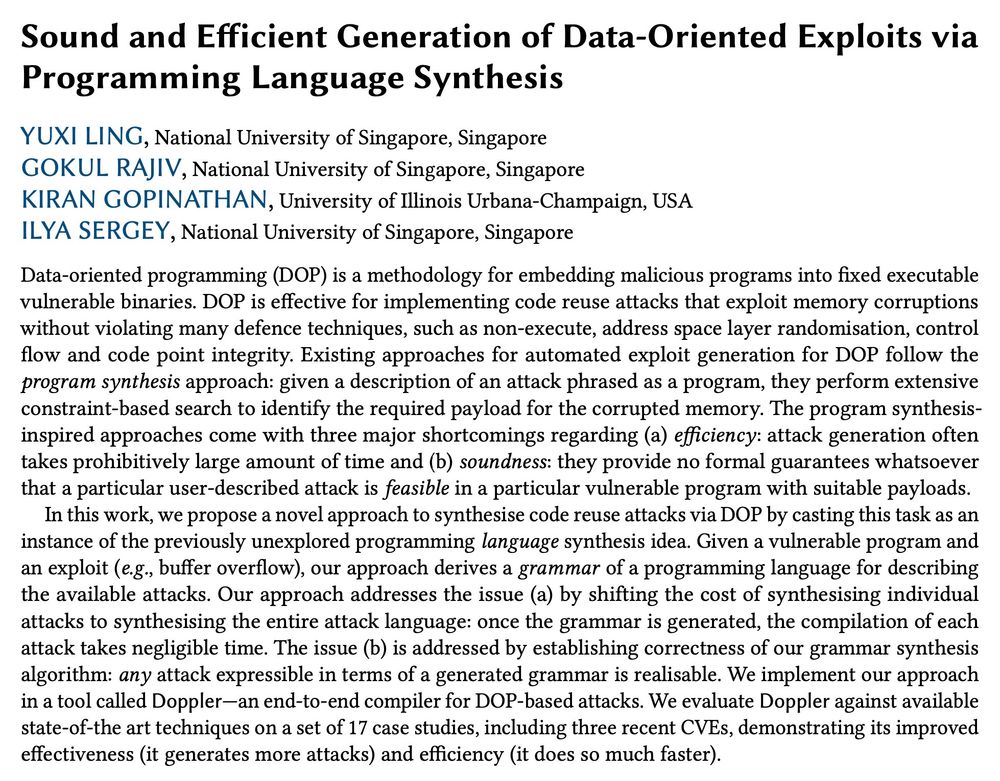
The gist: instead of generating individual attacks, we synthesise the whole *programming language* that expresses many exploits and guarantees their realisability.
Paper: ilyasergey.net/assets/pdf/p...
The gist: instead of generating individual attacks, we synthesise the whole *programming language* that expresses many exploits and guarantees their realisability.
Paper: ilyasergey.net/assets/pdf/p...
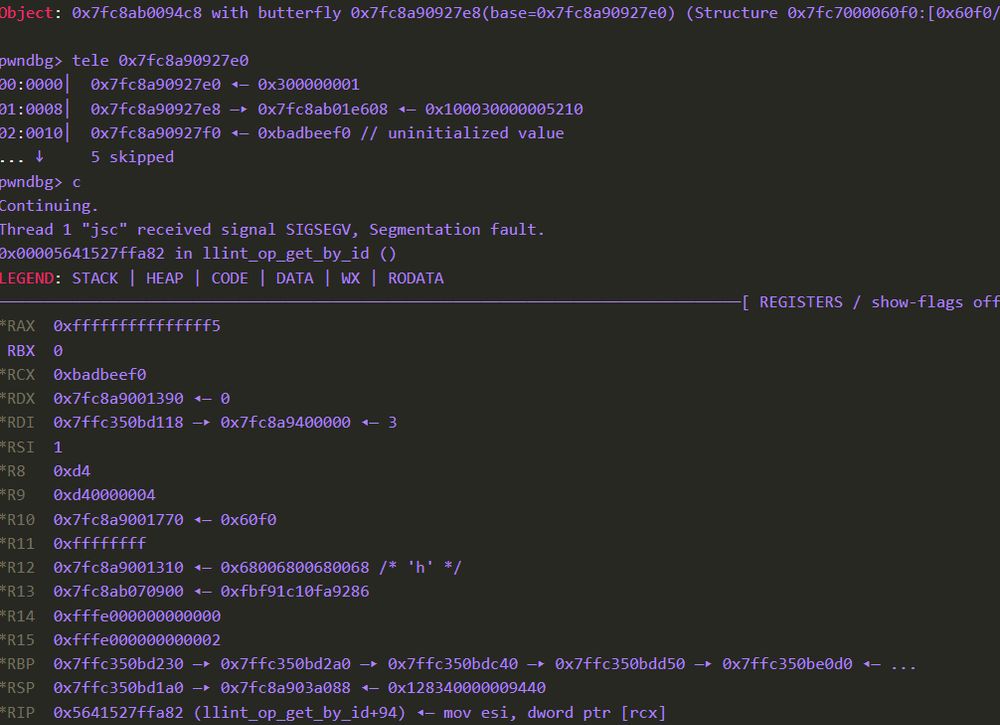
qriousec.github.io/post/jsc-uni...
#cybersecurity #informationsecurity #rce #javascript #vulnerability
qriousec.github.io/post/jsc-uni...
#cybersecurity #informationsecurity #rce #javascript #vulnerability
🥳📰 Very happy and proud that our paper on finding backdoors with fuzzing was accepted at the main track of @icseconf.bsky.social!
More details to follow soon 🙂
Congratulations and thank you to my students Dimitri Kokkonis and Emilien Decoux and co-supervisor Stefano Zacchiroli!
🥳📰 Very happy and proud that our paper on finding backdoors with fuzzing was accepted at the main track of @icseconf.bsky.social!
More details to follow soon 🙂
Congratulations and thank you to my students Dimitri Kokkonis and Emilien Decoux and co-supervisor Stefano Zacchiroli!
blog.exodusintel.com/2024/12/02/
Credits Luca Ginex
#windows #infosec
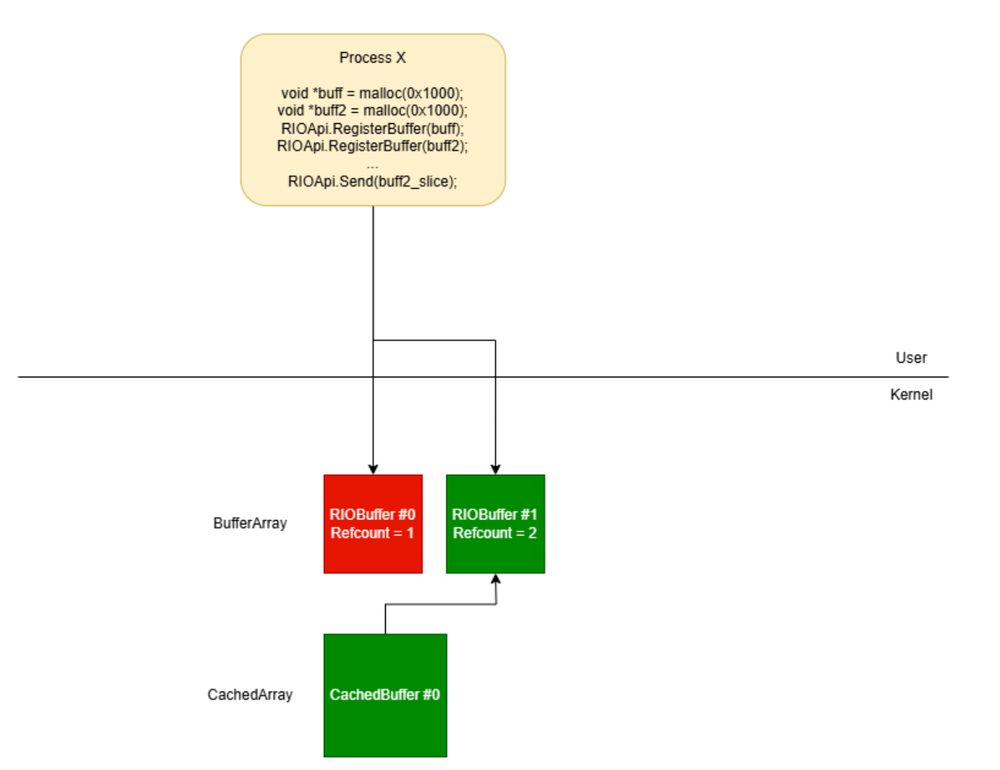
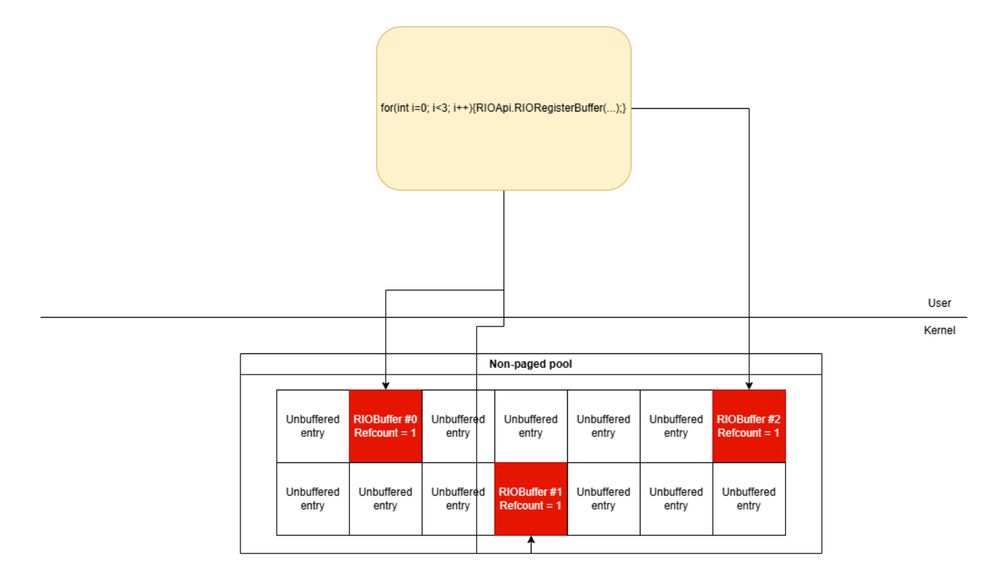
blog.exodusintel.com/2024/12/02/
Credits Luca Ginex
#windows #infosec