
Works at CEA List Institute from Université Paris-Saclay (France).
http://www.marcozzi.net
I make software safer by viciously torturing it to reveal its flaws.
I can be kind too.
See you there! 😀
Info and registration: gdr-gpl.cnrs.fr?cat=25

See you there! 😀
Info and registration: gdr-gpl.cnrs.fr?cat=25
🏠 secubic-ptcc.github.io
🧑🔬 Sébastien Bardin, Jean-Yves Marion, Stefano Zacchiroli
Thanks to the RESSI organizers who had even provided a pool to finish my #OOPSLA reviews! 😇




🏠 secubic-ptcc.github.io
🧑🔬 Sébastien Bardin, Jean-Yves Marion, Stefano Zacchiroli
Thanks to the RESSI organizers who had even provided a pool to finish my #OOPSLA reviews! 😇
▶️ It is a fuzzing benchmark (can fuzzers trigger backdoors reliably and fast?)
▶️ It is a backdoor detection benchmark (can code analyses find backdoors reliably?)
⬇️ github.com/binsec/rosarum

▶️ It is a fuzzing benchmark (can fuzzers trigger backdoors reliably and fast?)
▶️ It is a backdoor detection benchmark (can code analyses find backdoors reliably?)
⬇️ github.com/binsec/rosarum
🗣️ The slides of our #icse2025 presentation on "Finding Backdoors with Fuzzing" are now available at
⬇️ binsec.github.io/assets/publi...

🗣️ The slides of our #icse2025 presentation on "Finding Backdoors with Fuzzing" are now available at
⬇️ binsec.github.io/assets/publi...
👇
▶️ Backdoors were found in firmware & open-source code
▶️ Detection requires much manual reverse-engineering
▶️ Fuzzers cannot see backdoors
Our @icseconf.bsky.social preprint on finding backdoors with fuzzing is at binsec.github.io/nutshells/ic...
👇
Come and join the team here in Paris (or spread the word)! 🙂
Details and application: secubic-ptcc.github.io/jobs/open/20...

Come and join the team here in Paris (or spread the word)! 🙂
Details and application: secubic-ptcc.github.io/jobs/open/20...
Try it out: github.com/binsec/rosa
Huge thanks and congrats to my student Dimitri Kokkonis for his huge and great work! 👏👏👏

Try it out: github.com/binsec/rosa
Huge thanks and congrats to my student Dimitri Kokkonis for his huge and great work! 👏👏👏
──────
If you have not finished your #FUZZING paper yet, you are in luck! :) We decided to extend the deadline to March 26, 2025!
🔗 fuzzingworkshop.github.io
//cc @rohan.padhye.org, László Szekeres,
@ruijiemeng.bsky.social, @mboehme.bsky.social
──────
If you have not finished your #FUZZING paper yet, you are in luck! :) We decided to extend the deadline to March 26, 2025!
🔗 fuzzingworkshop.github.io
//cc @rohan.padhye.org, László Szekeres,
@ruijiemeng.bsky.social, @mboehme.bsky.social
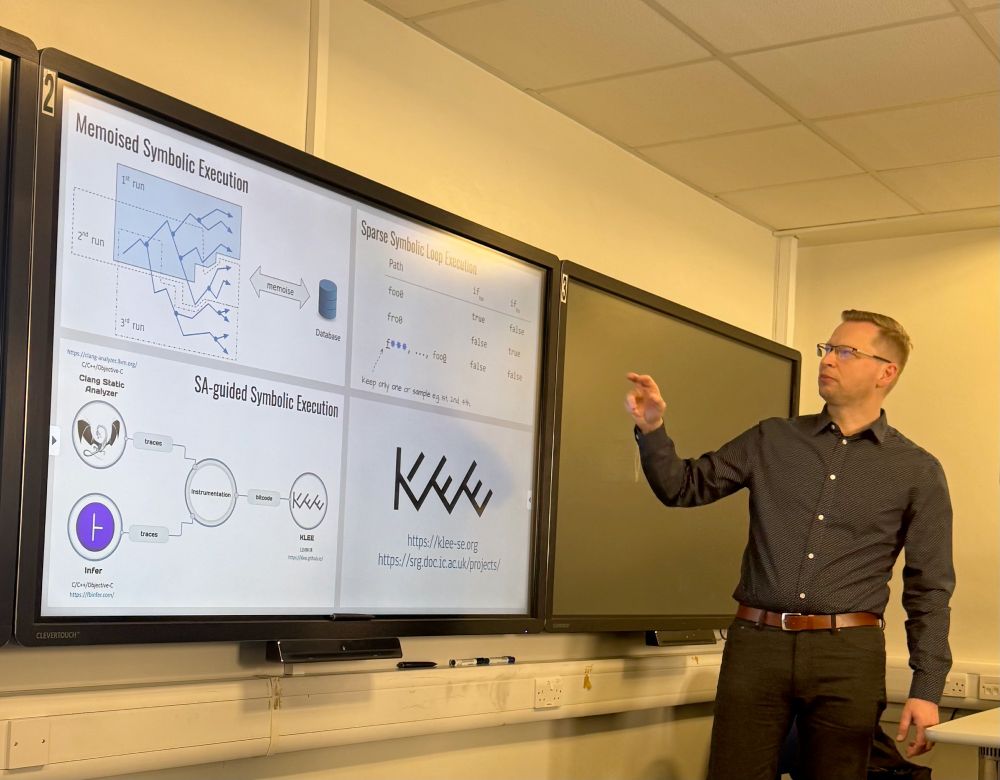

Try it out! 👇
Tool: github.com/binsec/rosa
Benchmark: github.com/binsec/rosarum
This work received both Available & Reusable badges at @icseconf.bsky.social 🥳

Try it out! 👇
Tool: github.com/binsec/rosa
Benchmark: github.com/binsec/rosarum
This work received both Available & Reusable badges at @icseconf.bsky.social 🥳
"ROSA Sets a New Standard for Backdoor Detection."
"If you work in cybersecurity, penetration testing, or software auditing, ROSA is a must-try in the fight against hidden threats."
medium.com/@itsissachar...

"ROSA Sets a New Standard for Backdoor Detection."
"If you work in cybersecurity, penetration testing, or software auditing, ROSA is a must-try in the fight against hidden threats."
medium.com/@itsissachar...
▶️ Backdoors were found in firmware & open-source code
▶️ Detection requires much manual reverse-engineering
▶️ Fuzzers cannot see backdoors
Our @icseconf.bsky.social preprint on finding backdoors with fuzzing is at binsec.github.io/nutshells/ic...
▶️ Backdoors were found in firmware & open-source code
▶️ Detection requires much manual reverse-engineering
▶️ Fuzzers cannot see backdoors
Our @icseconf.bsky.social preprint on finding backdoors with fuzzing is at binsec.github.io/nutshells/ic...
Looking forward to doing fun research together! 🥳
Details: binsec.github.io/people/zalcm...

Looking forward to doing fun research together! 🥳
Details: binsec.github.io/people/zalcm...
🥳📰 Very happy and proud that our paper on finding backdoors with fuzzing was accepted at the main track of @icseconf.bsky.social!
More details to follow soon 🙂
Congratulations and thank you to my students Dimitri Kokkonis and Emilien Decoux and co-supervisor Stefano Zacchiroli!
🥳📰 Very happy and proud that our paper on finding backdoors with fuzzing was accepted at the main track of @icseconf.bsky.social!
More details to follow soon 🙂
Congratulations and thank you to my students Dimitri Kokkonis and Emilien Decoux and co-supervisor Stefano Zacchiroli!
This was an enlighting talk and I recommend every fuzzing person to check out the corresponding paper (Distinguished Paper award at S&P'24)!
oaklandsok.github.io/papers/schlo...

This was an enlighting talk and I recommend every fuzzing person to check out the corresponding paper (Distinguished Paper award at S&P'24)!
oaklandsok.github.io/papers/schlo...

