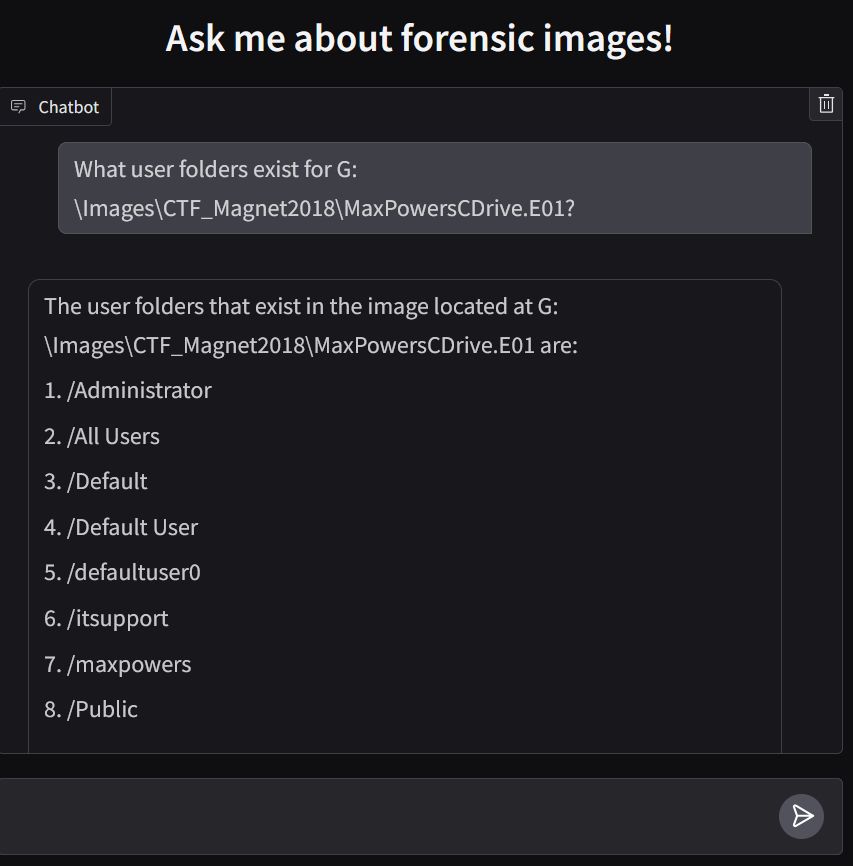
I use 4 levels of automation ranging from none to fully automated.
I think an ideal solution is to use full automation for low risk decisions. And recommendations for higher risk.
We use recommendations in Cyber Triage by scoring each artifact. You ultimately decide.

I use 4 levels of automation ranging from none to fully automated.
I think an ideal solution is to use full automation for low risk decisions. And recommendations for higher risk.
We use recommendations in Cyber Triage by scoring each artifact. You ultimately decide.
What to do after you find TeamViewer:
→ Log files to find activity details
→ Executables to find installation times
→ Domains to find download source
Learn how to corroborate timelines to investigate suspicious TeamViewer.
www.cybertriage.com/blog/dfir-ne...

What to do after you find TeamViewer:
→ Log files to find activity details
→ Executables to find installation times
→ Domains to find download source
Learn how to corroborate timelines to investigate suspicious TeamViewer.
www.cybertriage.com/blog/dfir-ne...
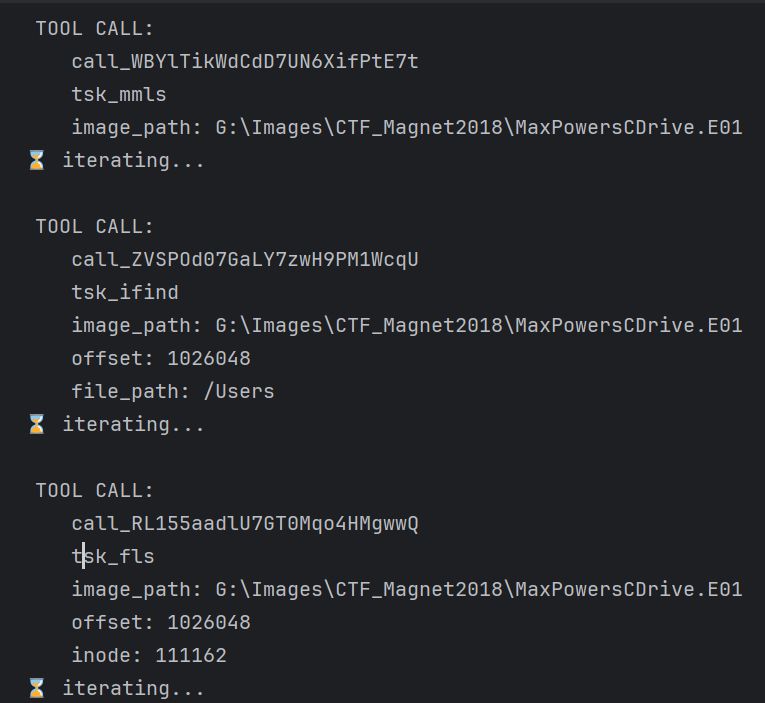
We'll also show Cyber Triage hooked up to an LLM so that you can query artifacts.
Join @carrier4n6.bsky.social and Sid Probstein as they discuss practical uses of AI and LLMs in digital investigations. Come learn from people who thought about these things for years before ChatGPT.
Aug 28 @ 11 AM
attendee.gotowebinar.com/register/243...
We'll also show Cyber Triage hooked up to an LLM so that you can query artifacts.
No one ever chose to manually parse FAT12 floppy drives with a hex editor when they could have a tool list out the file names.

No one ever chose to manually parse FAT12 floppy drives with a hex editor when they could have a tool list out the file names.
Here are my three thoughts on the most effective ways to add automation and which tools do them.
What are yours?
www.cybertriage.com/blog/3-ways-...

Here are my three thoughts on the most effective ways to add automation and which tools do them.
What are yours?
www.cybertriage.com/blog/3-ways-...
Perfect for security professionals at any level looking to enhance their endpoint investigation skills.
Register here: limacharlie.io/defender-fri...
#cybersecurity

Perfect for security professionals at any level looking to enhance their endpoint investigation skills.
Register here: limacharlie.io/defender-fri...
#cybersecurity
Myself, Sentinel1, and CompassMSP will talk about pros/cons of automating DFIR and SOC tasks.
Come tell us we're wrong!
May 8. 11AM Eastern.
register.gotowebinar.com/register/672...

Myself, Sentinel1, and CompassMSP will talk about pros/cons of automating DFIR and SOC tasks.
Come tell us we're wrong!
May 8. 11AM Eastern.
register.gotowebinar.com/register/672...
* New UIs to give you an overview of the endpoint
* Hyabusa integration
* Baseline
* Public key encryption on collector
* LOTS more....
Blog and Download Link: www.cybertriage.com/blog/3-14-re...
* New UIs to give you an overview of the endpoint
* Hyabusa integration
* Baseline
* Public key encryption on collector
* LOTS more....
Blog and Download Link: www.cybertriage.com/blog/3-14-re...
Data needs to get to the EDR server to be analyzed for attacks. Blocking techniques prevent data from getting to the server.
Example: Network filter to block packets destined to the server.
www.cybertriage.com/edr_evasion

Data needs to get to the EDR server to be analyzed for attacks. Blocking techniques prevent data from getting to the server.
Example: Network filter to block packets destined to the server.
www.cybertriage.com/edr_evasion
Types of Evasion Tactics
1) Blinding - prevent agent from seeing
2) Blocking - prevent data from analysis
3) Hiding - prevent detections
www.cybertriage.com/blog/how-edr...

Types of Evasion Tactics
1) Blinding - prevent agent from seeing
2) Blocking - prevent data from analysis
3) Hiding - prevent detections
www.cybertriage.com/blog/how-edr...
Endpoint Triage from 4 experts (I get to moderate)
- Harlan Carvey (Huntress)
- Kai Thomsen (Dragos)
- Quinnlan Varcoe (Blueberry Security)
- Mike Wilkinson (Sleuth Kit Labs)
Each presents their top 3!
Hope to see you there: register.gotowebinar.com/register/600...
Endpoint Triage from 4 experts (I get to moderate)
- Harlan Carvey (Huntress)
- Kai Thomsen (Dragos)
- Quinnlan Varcoe (Blueberry Security)
- Mike Wilkinson (Sleuth Kit Labs)
Each presents their top 3!
Hope to see you there: register.gotowebinar.com/register/600...
Apr 17.
I'll MC and you'll hear from @keydet89.bsky.social (Huntress), Kai Thomsen (Dragos), @dfirmike.bsky.social (Sleuth Kit Labs) and Quinnlan Varcoe (Blueberry Security).
See you there!
register.gotowebinar.com/register/600...

Apr 17.
I'll MC and you'll hear from @keydet89.bsky.social (Huntress), Kai Thomsen (Dragos), @dfirmike.bsky.social (Sleuth Kit Labs) and Quinnlan Varcoe (Blueberry Security).
See you there!
register.gotowebinar.com/register/600...
You should not miss webinar tmrw! 😀
Markus and I will talk about why EDR alerts could be days after an attack started.
We'll talk about how to do endpoint triage to see what else happened beyond the alert!
Mar 27 @ 11 Eastern
register.gotowebinar.com/register/916...
You should not miss webinar tmrw! 😀
Markus and I will talk about why EDR alerts could be days after an attack started.
We'll talk about how to do endpoint triage to see what else happened beyond the alert!
Mar 27 @ 11 Eastern
register.gotowebinar.com/register/916...
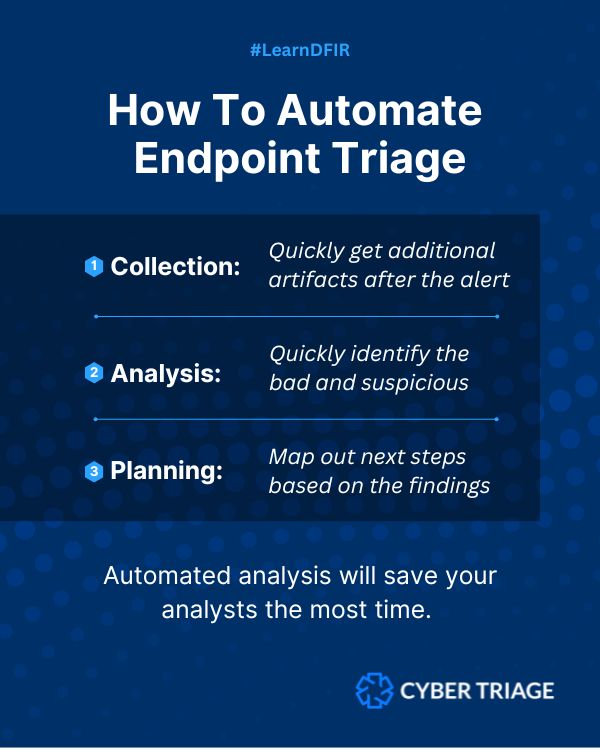
Blog post that is part of our Endpoint Triage series.
Alert triage focuses on validating and prioritizing the EDR/SIEM alert.
Endpoint triage focuses on prioritizing the host. How bad is it?
www.cybertriage.com/blog/alert-t...

Blog post that is part of our Endpoint Triage series.
Alert triage focuses on validating and prioritizing the EDR/SIEM alert.
Endpoint triage focuses on prioritizing the host. How bad is it?
www.cybertriage.com/blog/alert-t...
It's been a minute, but it's out. Notable features are BitLocker support and it can run side-by-side with Cyber Triage. Plus, a bunch of library updates.
Now Cyber Triage and Autopsy can be used on the same case at the same time!
www.autopsy.com/autopsy-4-22...

It's been a minute, but it's out. Notable features are BitLocker support and it can run side-by-side with Cyber Triage. Plus, a bunch of library updates.
Now Cyber Triage and Autopsy can be used on the same case at the same time!
www.autopsy.com/autopsy-4-22...
Endpoint Triage should be in any security team's process.
attendee.gotowebinar.com/register/281...
Endpoint Triage should be in any security team's process.
attendee.gotowebinar.com/register/281...
Webinar: Tomorrow at 11 - Vendor Agnostic
register.gotowebinar.com/register/142...

Webinar: Tomorrow at 11 - Vendor Agnostic
register.gotowebinar.com/register/142...
#DFIR Webinar Thu @ 11.
register.gotowebinar.com/register/142...

#DFIR Webinar Thu @ 11.
register.gotowebinar.com/register/142...
Cobalt Strike and a Pair of SOCKS Lead to LockBit Ransomware
Analysis & reporting completed by @r3nzsec, @MyDFIR & @MittenSec.
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/01/27/c...

Cobalt Strike and a Pair of SOCKS Lead to LockBit Ransomware
Analysis & reporting completed by @r3nzsec, @MyDFIR & @MittenSec.
Audio: Available on Spotify, Apple, YouTube and more!
thedfirreport.com/2025/01/27/c...
www.cybertriage.com/blog/informa...

www.cybertriage.com/blog/informa...