Investigate a real intrusion where a compromised Confluence server led to rapid domain-wide access.
Step through the investigation and see how LockBit was deployed end-to-end.
👉 dfirlabs.thedfirreport.com/auth/login

Investigate a real intrusion where a compromised Confluence server led to rapid domain-wide access.
Step through the investigation and see how LockBit was deployed end-to-end.
👉 dfirlabs.thedfirreport.com/auth/login
✔ Buy now, redeem anytime over the next 3 months
⏰ Offer ends January 1
💳 Discount applied automatically at checkout
dfirlabs.thedfirreport.com

✔ Buy now, redeem anytime over the next 3 months
⏰ Offer ends January 1
💳 Discount applied automatically at checkout
dfirlabs.thedfirreport.com
✔ Buy now, redeem anytime over the next 3 months
⏰ Offer ends January 1
💳 Discount applied automatically at checkout
dfirlabs.thedfirreport.com

✔ Buy now, redeem anytime over the next 3 months
⏰ Offer ends January 1
💳 Discount applied automatically at checkout
dfirlabs.thedfirreport.com

We’re giving away 5 FREE DFIR Labs cases!
How to enter:
➡️Post your favorite DFIR Report
➡️Tell us why it's your favorite
That’s it! 🙌 We’ll select 5 winners before Christmas!
DFIR Labs - dfirlabs.thedfirreport.com/auth/login
Reports - thedfirreport.com

We’re giving away 5 FREE DFIR Labs cases!
How to enter:
➡️Post your favorite DFIR Report
➡️Tell us why it's your favorite
That’s it! 🙌 We’ll select 5 winners before Christmas!
DFIR Labs - dfirlabs.thedfirreport.com/auth/login
Reports - thedfirreport.com
All files involved in the initial access phase were signed with valid certificates.

All files involved in the initial access phase were signed with valid certificates.
Now until December 1st, all swag in our store is 50% OFF — shirts, hoodies, and stickers, while supplies last!
🎁 Bonus: Every order comes with 2 FREE DFIR Report stickers!
Don’t miss it — once it’s gone, it’s gone.
store.thedfirreport.com/collections/...

Now until December 1st, all swag in our store is 50% OFF — shirts, hoodies, and stickers, while supplies last!
🎁 Bonus: Every order comes with 2 FREE DFIR Report stickers!
Don’t miss it — once it’s gone, it’s gone.
store.thedfirreport.com/collections/...
Now until December 1st, all swag in our store is 50% OFF — shirts, hoodies, and stickers, while supplies last!
🎁 Bonus: Every order comes with 2 FREE DFIR Report stickers!
Don’t miss it — once it’s gone, it’s gone.
store.thedfirreport.com/collections/...

Now until December 1st, all swag in our store is 50% OFF — shirts, hoodies, and stickers, while supplies last!
🎁 Bonus: Every order comes with 2 FREE DFIR Report stickers!
Don’t miss it — once it’s gone, it’s gone.
store.thedfirreport.com/collections/...
🎉New report out by @Friffnz, Daniel Casenove & @MittenSec!🎉
Attackers used stolen creds to access RDP, quickly pivoted to a DC with a second compromised admin, created impersonation accounts, mapped the environment, and more.

🎉New report out by @Friffnz, Daniel Casenove & @MittenSec!🎉
Attackers used stolen creds to access RDP, quickly pivoted to a DC with a second compromised admin, created impersonation accounts, mapped the environment, and more.
"Artifacts of this SMB enumeration were left behind in the smb.db database stored by NetExec in C:\Users\%UserProfile%\nxc\workspaces\smb.db. This database confirms that a number of domains...
1/2

"Artifacts of this SMB enumeration were left behind in the smb.db database stored by NetExec in C:\Users\%UserProfile%\nxc\workspaces\smb.db. This database confirms that a number of domains...
1/2
"In this case, Netscan was run with domain administrator privileges, so all discovered shares were writable. As a result, NetScan was able to create and delete the delete[.]me file on each...
1/2

"In this case, Netscan was run with domain administrator privileges, so all discovered shares were writable. As a result, NetScan was able to create and delete the delete[.]me file on each...
1/2
"On the domain controller, they used the "Active Directory Users and Computers" snap-in (dsa.msc) to create three users for persistence. All of the newly created accounts have usernames that mimic...
1/2

"On the domain controller, they used the "Active Directory Users and Computers" snap-in (dsa.msc) to create three users for persistence. All of the newly created accounts have usernames that mimic...
1/2
"The first instance of unauthorized access by the threat actor was a successful RDP logon to the beachhead host, a publicly exposed RDP server. The logon was performed using valid credentials, and...
1/3

"The first instance of unauthorized access by the threat actor was a successful RDP logon to the beachhead host, a publicly exposed RDP server. The logon was performed using valid credentials, and...
1/3
All files involved in the initial access phase were signed with valid certificates.

All files involved in the initial access phase were signed with valid certificates.
The challenge is complete! A massive thank you to everyone who participated in our latest DFIR Challenge!
Big shoutout to the top finishers who untangled the whole thing:
🥇 Jason Phang Vern Onn
🥈 Marko Yavorskyi
🥉 Bohdan Hrondzal


The challenge is complete! A massive thank you to everyone who participated in our latest DFIR Challenge!
Big shoutout to the top finishers who untangled the whole thing:
🥇 Jason Phang Vern Onn
🥈 Marko Yavorskyi
🥉 Bohdan Hrondzal
From a Single Click: How Lunar Spider Enabled a Near Two-Month Intrusion
Analysis/reporting completed by @RussianPanda, Christos Fotopoulos, Salem Salem, reviewed by @svch0st.
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️

From a Single Click: How Lunar Spider Enabled a Near Two-Month Intrusion
Analysis/reporting completed by @RussianPanda, Christos Fotopoulos, Salem Salem, reviewed by @svch0st.
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️
Of note, the image 2.jpg that was alongside the payload in the .zip was not used by the malware. We assess that it was likely used to “pad” the..."
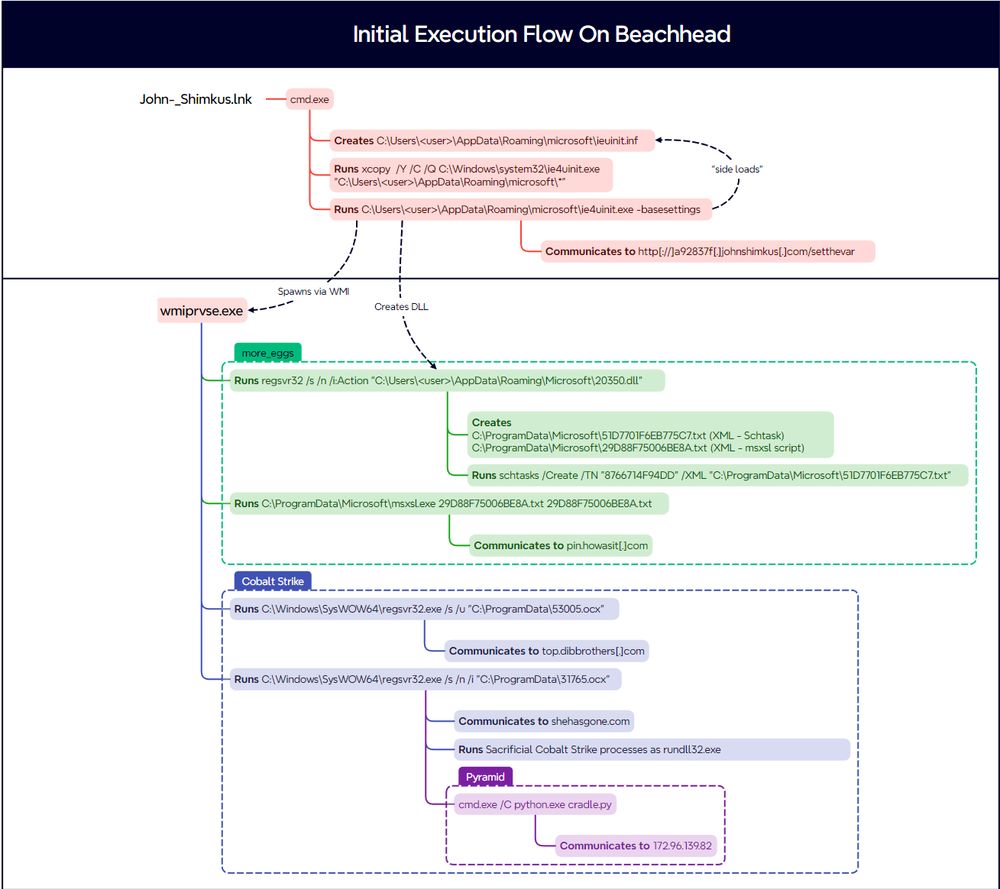
Of note, the image 2.jpg that was alongside the payload in the .zip was not used by the malware. We assess that it was likely used to “pad” the..."
The first binary, GT_NET.exe is associated with Grixba, a custom data-gathering tool used by the Play ransomware group. Its metadata was crafted to..."

The first binary, GT_NET.exe is associated with Grixba, a custom data-gathering tool used by the Play ransomware group. Its metadata was crafted to..."
The trojanized installer was a downloader, more publicly known as “d3f@ckloader”, and is..."

The trojanized installer was a downloader, more publicly known as “d3f@ckloader”, and is..."
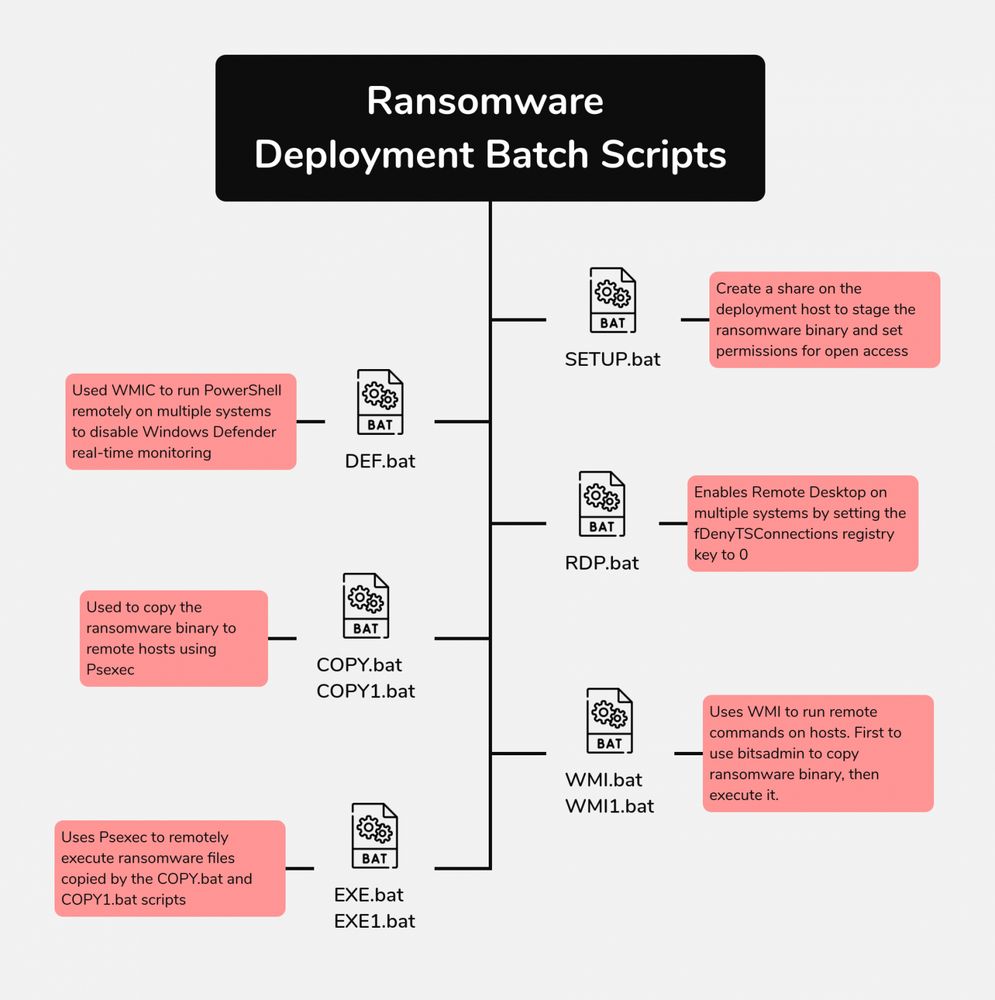

Blurring the Lines: Intrusion Shows Connection With Three Major Ransomware Gangs
Analysis and reporting completed by @r3nzsec, @EncapsulateJ, @rkonicekr, & Adam Rowe
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️

Blurring the Lines: Intrusion Shows Connection With Three Major Ransomware Gangs
Analysis and reporting completed by @r3nzsec, @EncapsulateJ, @rkonicekr, & Adam Rowe
Audio: Available on Spotify, Apple, YouTube and more!
Report:⬇️


