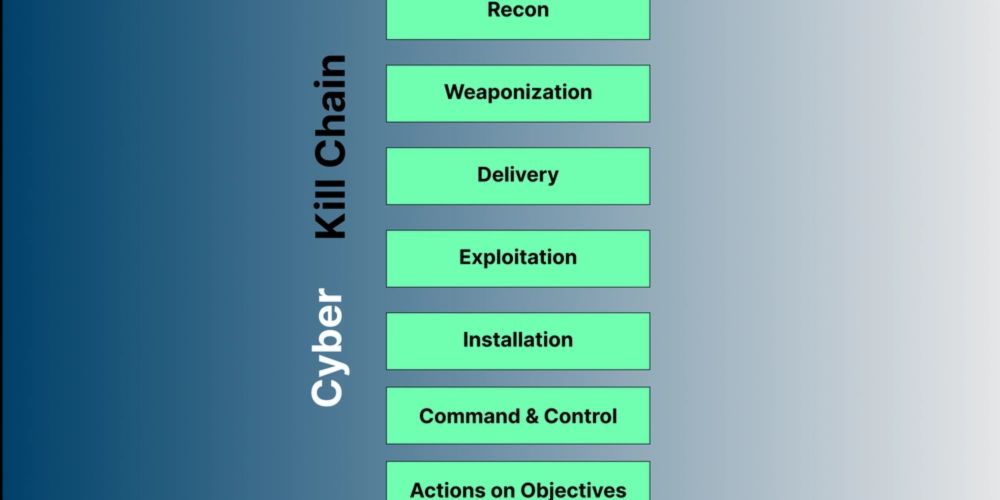
🔹Reconnaissance
🔹Weaponization
🔹Delivery
🔹Exploitation
🔹Installation
🔹Command and Control
🔹Actions at Objective

🔹Reconnaissance
🔹Weaponization
🔹Delivery
🔹Exploitation
🔹Installation
🔹Command and Control
🔹Actions at Objective
#tryhackme-walkthrough #cyber-kill-chain #tryhackme-writeup #cybersecurity #tryhackme
Origin | Interest | Match

#tryhackme-walkthrough #cyber-kill-chain #tryhackme-writeup #cybersecurity #tryhackme
Origin | Interest | Match
Kill Chain: The Cyber War on America's Elections is an American television documentary film produced by Ish Entertainment, Blumhouse Productions and HBO Films. The film examines the American election system and its vulnerabilities to foreign cyberwarfare operations and 2016
Kill Chain: The Cyber War on America's Elections is an American television documentary film produced by Ish Entertainment, Blumhouse Productions and HBO Films. The film examines the American election system and its vulnerabilities to foreign cyberwarfare operations and 2016





A gripping look at vulnerabilities in U.S. election systems.
Directed by Sarah Teale , Ardizzone & Michaels .
Now streaming on @streamonmax
#KillChainDoc #ElectionSecurity #NowStreaming #Max #DocumentaryFilm

A gripping look at vulnerabilities in U.S. election systems.
Directed by Sarah Teale , Ardizzone & Michaels .
Now streaming on @streamonmax
#KillChainDoc #ElectionSecurity #NowStreaming #Max #DocumentaryFilm
#StudyBullet-20 #Free #Courses #StudyBullet
Origin | Interest | Match

#StudyBullet-20 #Free #Courses #StudyBullet
Origin | Interest | Match

the public as well as state / local government all have an interest in Dominion / smartmatic
anyone remember things like this: "Kill Chain: The Cyber War on America's Elections"

the public as well as state / local government all have an interest in Dominion / smartmatic
anyone remember things like this: "Kill Chain: The Cyber War on America's Elections"

The current cyber landscape is alarming, with Mean Time To Attack (MTTA) decreasing dramatically to just 22 minutes. This rapid exploitation of new vulnerabilities is believed to be partially responsible for the rapid growth and a…
#hackernews #news
The current cyber landscape is alarming, with Mean Time To Attack (MTTA) decreasing dramatically to just 22 minutes. This rapid exploitation of new vulnerabilities is believed to be partially responsible for the rapid growth and a…
#hackernews #news




