
ECScape: a privilege escalation chain in Amazon ECS lets attackers hijack cloud environments. Learn how to protect your data with expert insights and mitigation tips.
thenimblenerd.com?p=1052425

ECScape: a privilege escalation chain in Amazon ECS lets attackers hijack cloud environments. Learn how to protect your data with expert insights and mitigation tips.
thenimblenerd.com?p=1052425


L: https://www.sweet.security/blog/ecscape-understanding-iam-privilege-boundaries-in-amazon-ecs
C: https://news.ycombinator.com/item?id=44818501
posted on 2025.08.06 at 18:16:00 (c=0, p=4)
L: https://www.sweet.security/blog/ecscape-understanding-iam-privilege-boundaries-in-amazon-ecs
C: https://news.ycombinator.com/item?id=44818501
posted on 2025.08.06 at 18:16:00 (c=0, p=4)

This post is Part 2 of our educational series on Amazon ECS security. In Part 1 – Under the Hood of Amazon ECS on EC2, we explored how the ECS agent, IAM roles and the ECS control plane provide credentials to tasks. Here we’ll…
This post is Part 2 of our educational series on Amazon ECS security. In Part 1 – Under the Hood of Amazon ECS on EC2, we explored how the ECS agent, IAM roles and the ECS control plane provide credentials to tasks. Here we’ll…
Cybersecurity researchers have demonstrated an "end-to-end privilege escalation chain" in Amazon Elastic Container Service (ECS) that could be exploited by an attacker to conduct lateral movement…
#hackernews #news

Cybersecurity researchers have demonstrated an "end-to-end privilege escalation chain" in Amazon Elastic Container Service (ECS) that could be exploited by an attacker to conduct lateral movement…
#hackernews #news
#Cyber #Security
Origin | Interest | Match

https://www.sweet.security/blog/ecscape-understanding-iam-privilege-boundaries-in-amazon-ecs
https://www.sweet.security/blog/ecscape-understanding-iam-privilege-boundaries-in-amazon-ecs


#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Vulnerabilities #Vulnerability […]
[Original post on cybersecuritynews.com]
#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Vulnerabilities #Vulnerability […]
[Original post on cybersecuritynews.com]
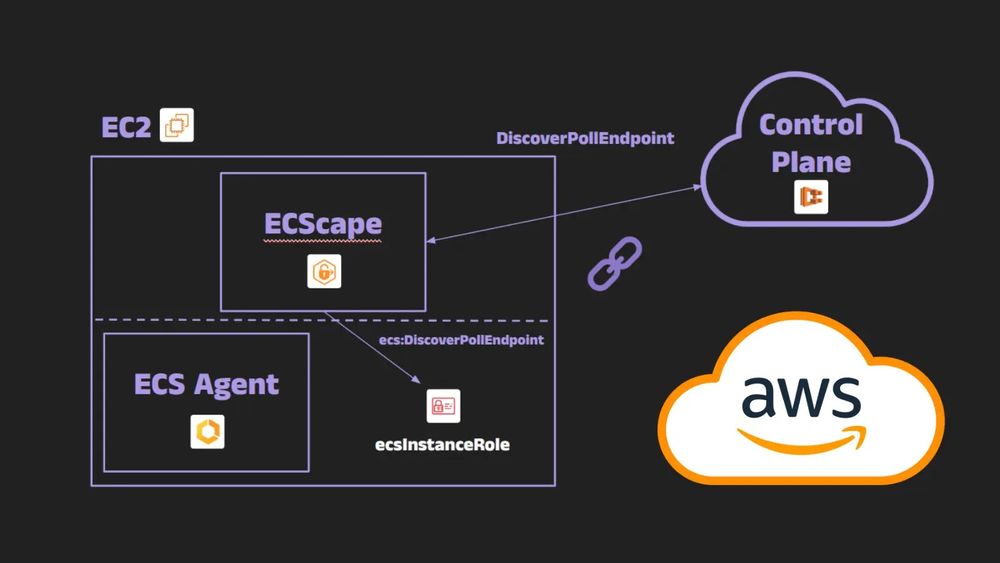
#Amazon #Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Cybersecurity #Cyber […]
[Original post on cyberpress.org]

#Amazon #Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Cybersecurity #Cyber […]
[Original post on cyberpress.org]

naorhaziz.com/posts/under-...
ECScape: Understanding IAM Privilege Boundaries in Amazon ECS naorhaziz.com/posts/ecscap...

naorhaziz.com/posts/under-...
ECScape: Understanding IAM Privilege Boundaries in Amazon ECS naorhaziz.com/posts/ecscap...



