https://itnerd.blog/2025/04/15/guest-post-fake-pdf-converters-used-to-deploy-arechclient2-malware-warns-cloudsek/
#Commentary #CloudSEK
Event Attributes

https://itnerd.blog/2025/04/15/guest-post-fake-pdf-converters-used-to-deploy-arechclient2-malware-warns-cloudsek/
#Commentary #CloudSEK
Event Attributes
CloudSEK's security researchers have uncovered a sophisticated malware campaign using fake PDF-to-DOCX conversion tools to infect unsuspecting users with a powerful information stealer. This comes just weeks after…
CloudSEK's security researchers have uncovered a sophisticated malware campaign using fake PDF-to-DOCX conversion tools to infect unsuspecting users with a powerful information stealer. This comes just weeks after…

Campaign uses ClickFix social engineering to deliver GHOSTPULSE loader, which then deploys the ARECHCLIENT2 infostealer/RAT.
-
IOCs: 50. 57. 243. 90, 144. 172. 97. 2, 143. 110. 230. 167
-
#ARECHCLIENT2 #ClickFix #ThreatIntel
Campaign uses ClickFix social engineering to deliver GHOSTPULSE loader, which then deploys the ARECHCLIENT2 infostealer/RAT.
-
IOCs: 50. 57. 243. 90, 144. 172. 97. 2, 143. 110. 230. 167
-
#ARECHCLIENT2 #ClickFix #ThreatIntel
https://cyberpress.org/highly-obfuscated-net-sectoprat-mimic/
#Chrome #Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Cybersecurity #Cyber #Security #Cyber #security #news
Event Attributes

https://cyberpress.org/highly-obfuscated-net-sectoprat-mimic/
#Chrome #Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Cybersecurity #Cyber #Security #Cyber #security #news
Event Attributes
#ARECHCLIENT2 #INFOSTEALER #Lumma #Rhadamanthys #SHELLTER
www.matricedigitale.it/2025/07/08/s...

#ARECHCLIENT2 #INFOSTEALER #Lumma #Rhadamanthys #SHELLTER
www.matricedigitale.it/2025/07/08/s...
A complete analysis of HijackLoader is beyond the scope of this thread, but stay tuned for long-form content 👀
6/8🧵

A complete analysis of HijackLoader is beyond the scope of this thread, but stay tuned for long-form content 👀
6/8🧵
#adobeziptrojan #arechclient2 #candyxpdf #cybercrime #falsiconvertitoripdf #informationstealer #malware
www.matricedigitale.it/sicurezza-in...

#adobeziptrojan #arechclient2 #candyxpdf #cybercrime #falsiconvertitoripdf #informationstealer #malware
www.matricedigitale.it/sicurezza-in...
Discover the sneaky malware campaign mimicking PDFCandy.com to spread ArechClient2. Learn the tricks and dodge the traps with Hackread's expert insights!
thenimblenerd.com?p=1042849

Discover the sneaky malware campaign mimicking PDFCandy.com to spread ArechClient2. Learn the tricks and dodge the traps with Hackread's expert insights!
thenimblenerd.com?p=1042849
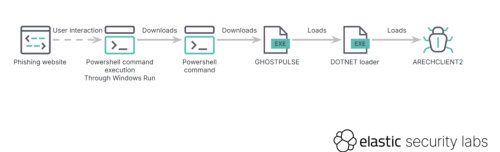

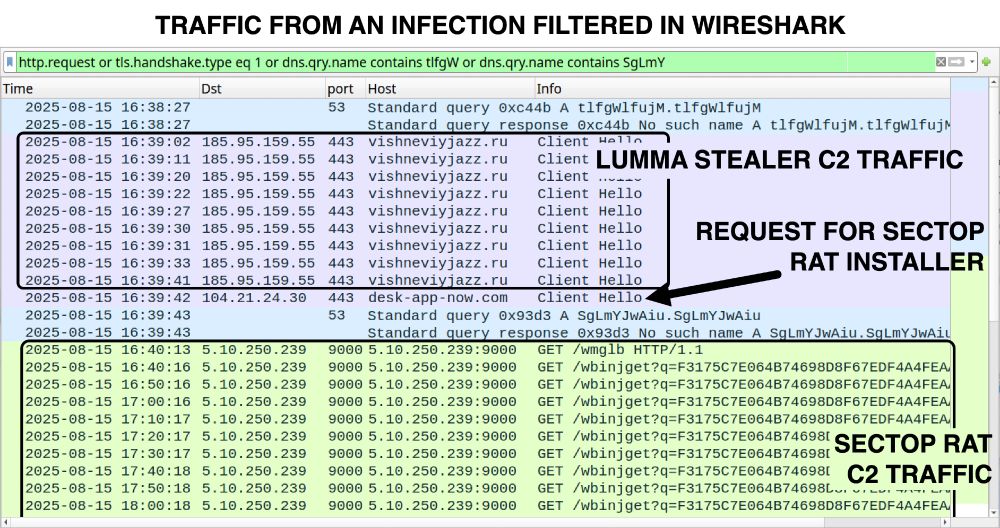
Introduction: The cybersecurity landscape faces yet another sophisticated attack chain, where Lumma Stealer infections escalate into full SectopRAT (ArechClient2) deployments. This malware campaign leverages deceptive…
Introduction: The cybersecurity landscape faces yet another sophisticated attack chain, where Lumma Stealer infections escalate into full SectopRAT (ArechClient2) deployments. This malware campaign leverages deceptive…
Threat actors are using the commercial evasion framework SHELLTER to deploy infostealers like LUMMA, ARECHCLIENT2, and RHADAMANTHYS.
-
IOCs: eaglekl. digital, 185. 156. 72. 80, 94. 141. 12. 182
-
#Infostealer #SHELLTER #ThreatIntel
Threat actors are using the commercial evasion framework SHELLTER to deploy infostealers like LUMMA, ARECHCLIENT2, and RHADAMANTHYS.
-
IOCs: eaglekl. digital, 185. 156. 72. 80, 94. 141. 12. 182
-
#Infostealer #SHELLTER #ThreatIntel
https://cyberpress.org/highly-obfuscated-net-sectoprat-mimic/
#Chrome #Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Cybersecurity #Cyber #Security #Cyber #security #news
Event Attributes

https://cyberpress.org/highly-obfuscated-net-sectoprat-mimic/
#Chrome #Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Cybersecurity #Cyber #Security #Cyber #security #news
Event Attributes



CloudSEK uncovers a sophisticated malware campaign where attackers impersonate PDFCandy.com to distribute the ArechClient2 information stealer. Learn how…
#hackernews #news
CloudSEK uncovers a sophisticated malware campaign where attackers impersonate PDFCandy.com to distribute the ArechClient2 information stealer. Learn how…
#hackernews #news

