
csprecon can do this for you 👉 https://github.com/edoardottt/csprecon
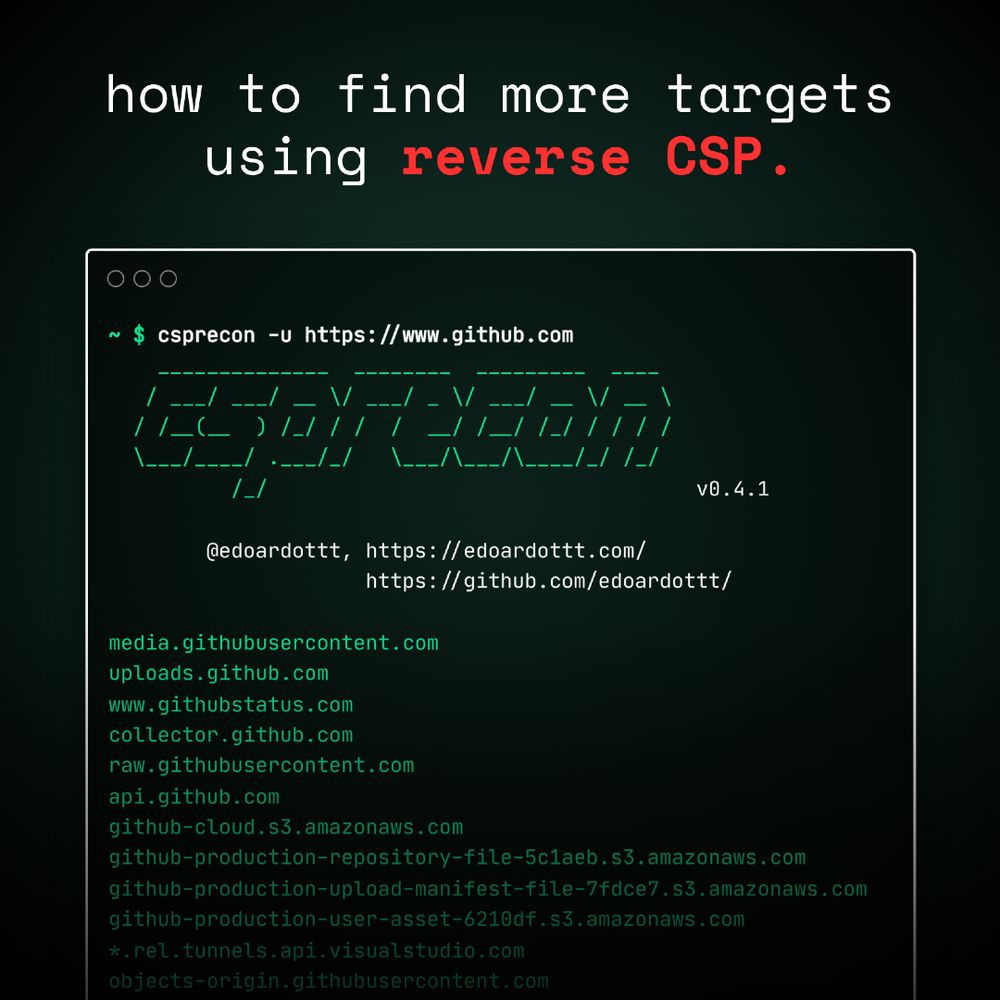
csprecon can do this for you 👉 https://github.com/edoardottt/csprecon

portswigger-labs.net/mxss/
portswigger-labs.net/mxss/
Luckily, I later worked with and for "the other side" and it changed my mind 🤯
I hope young people reading it will avoid taking years to understand the complexities of fixing bugs in a timely manner 🤞

Luckily, I later worked with and for "the other side" and it changed my mind 🤯
I hope young people reading it will avoid taking years to understand the complexities of fixing bugs in a timely manner 🤞
Must admit my timeline here is not as interesting, but I guess that's up to me to fix.
Must admit my timeline here is not as interesting, but I guess that's up to me to fix.
www.csoonline.com/ar...

www.csoonline.com/ar...
www.amazon.nl/-/en/Simone-...
Since I deleted my account, this is the tweet:
www.amazon.nl/-/en/Simone-...
Since I deleted my account, this is the tweet:
Got a problem? Not sure the right direction? Try anything at all! Worst case is you'll learn something, best case is you make something good.
Also: it's practice, so you get faster at trying new things, so you get faster at everything.
I'm absolutely a discovery everything.
Got a problem? Not sure the right direction? Try anything at all! Worst case is you'll learn something, best case is you make something good.
Also: it's practice, so you get faster at trying new things, so you get faster at everything.
Get the book here:
shehackspurple.ca/bo...
Contents of Chapter 2: Beginning
· Follow a Secure System Development Life Cycle (Part 3)

Get the book here:
shehackspurple.ca/bo...
Contents of Chapter 2: Beginning
· Follow a Secure System Development Life Cycle (Part 3)
Inconsistencies in the HTTP cookie specification and its implementations have caused a situation where countless websites (including Facebook, Netflix, Okta, WhatsApp, Apple, etc.) are one small mistake away from locking their users out.
grayduck.mn/2024/11/21/h...
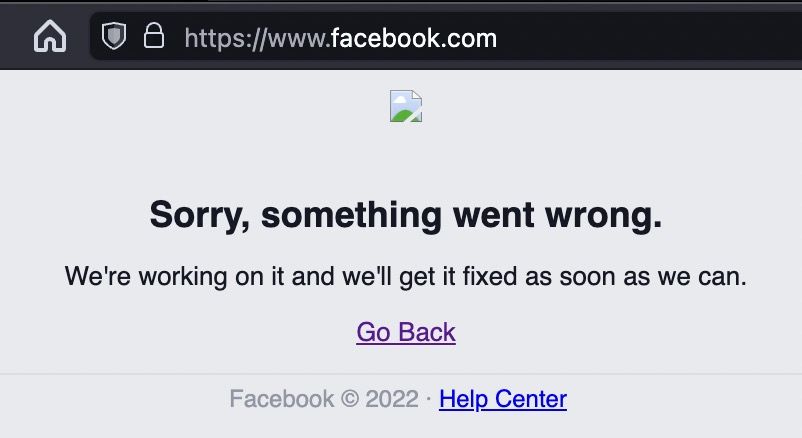
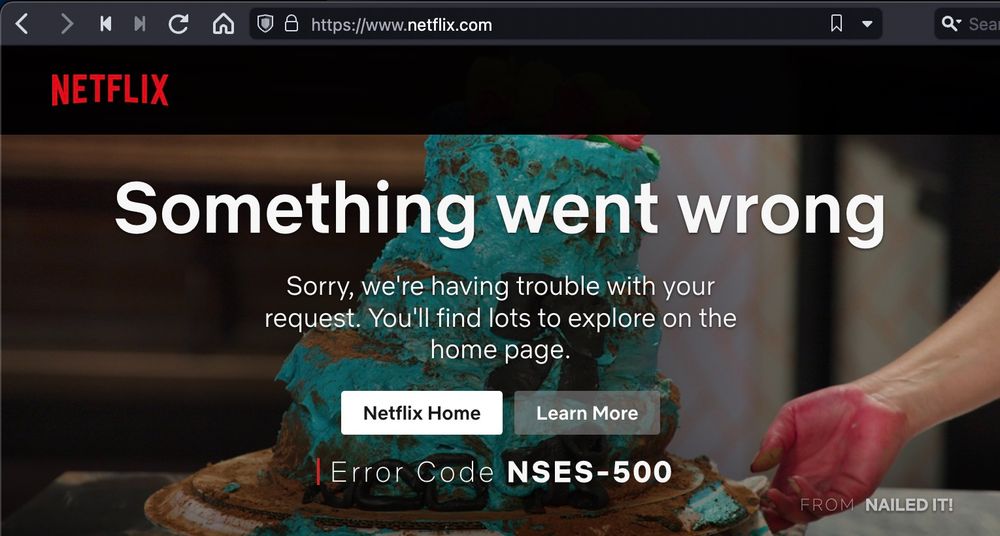
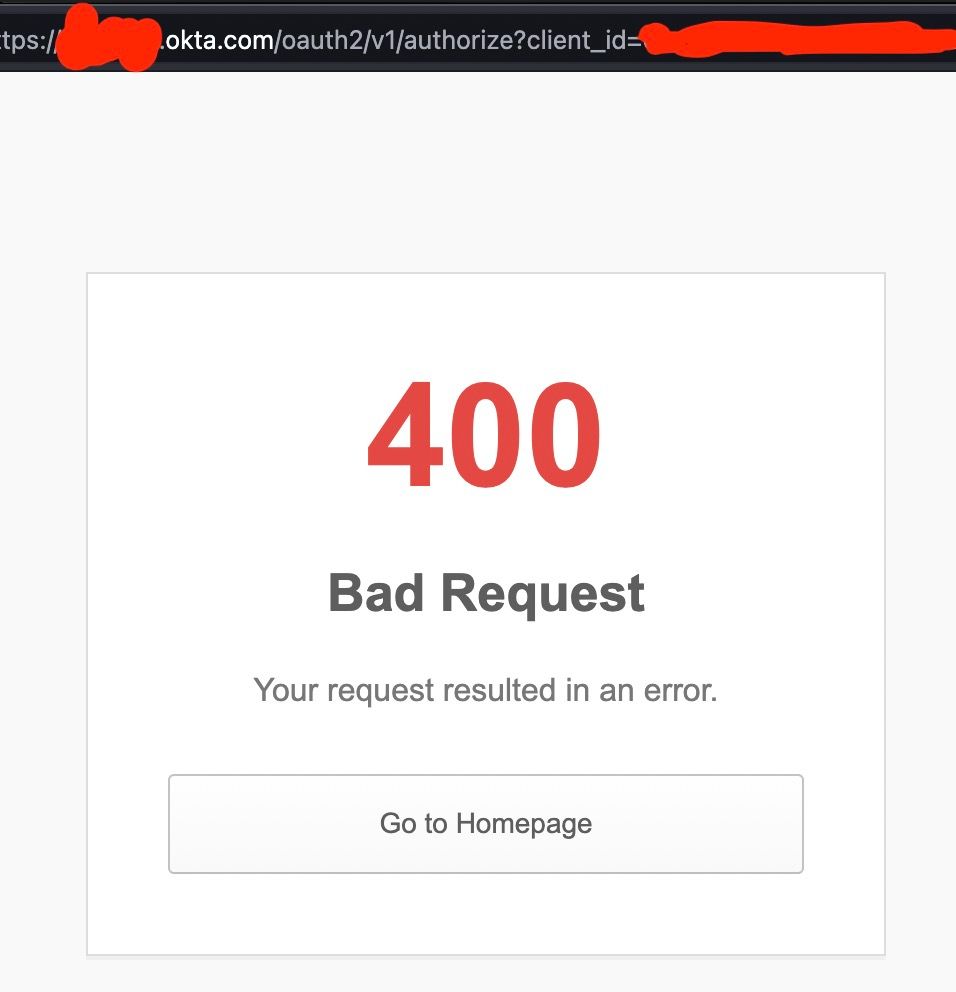
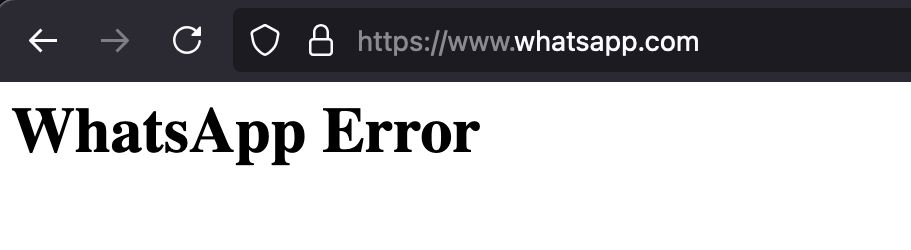
Inconsistencies in the HTTP cookie specification and its implementations have caused a situation where countless websites (including Facebook, Netflix, Okta, WhatsApp, Apple, etc.) are one small mistake away from locking their users out.
grayduck.mn/2024/11/21/h...
11 char XSS with mind-boggling race-conditions.
TL;DR the final payload is location=x (10 chars) and the longest is top.Z.x=x.d (11 char)
It's shorter than location=name !!
terjanq.me/solutions/jo...
11 char XSS with mind-boggling race-conditions.
TL;DR the final payload is location=x (10 chars) and the longest is top.Z.x=x.d (11 char)
It's shorter than location=name !!
terjanq.me/solutions/jo...
There is a CSP in a meta tag.
Goal: get the content from the file hack.js and have it inserted in the page. like in the image
joaxcar.com/xss/self.html

There is a CSP in a meta tag.
Goal: get the content from the file hack.js and have it inserted in the page. like in the image
joaxcar.com/xss/self.html

