
👉 Find all of them here: bsky.app/search?q=fro...
👉 Find all of them here: bsky.app/search?q=fro...
🔍 Hunt for known SecureString decoding commands

🔍 Hunt for known SecureString decoding commands
Not just a joke - you can make vi/vim run arbitrary commands, not all methods to do so are well detected.
🔍 Hunt for child processes of vi(m), especially those that are rare in your environment.


Not just a joke - you can make vi/vim run arbitrary commands, not all methods to do so are well detected.
🔍 Hunt for child processes of vi(m), especially those that are rare in your environment.
🔵 lots-project.com + LOLBINs
🟠 hijacklibs.net + DLL write events
🟢 lolrmm.io + DNS requests



🔵 lots-project.com + LOLBINs
🟠 hijacklibs.net + DLL write events
🟢 lolrmm.io + DNS requests


🔴 Executing parent is usually explorer.exe, making detection harder
🔍 Hunt for reg changes to this key
👉 lolbas-project.github.io/lolbas/Binar...
🔴 Executing parent is usually explorer.exe, making detection harder
🔍 Hunt for reg changes to this key
👉 lolbas-project.github.io/lolbas/Binar...
🌩️ Cloud creds often linger in Environment Variables, especially on servers/dev machines
🟠 One compromised endpoint could thus lead to a full cloud breach
🔍 Hunt for exposed tokens - if you can see it, so could an attacker (well, kinda)


🌩️ Cloud creds often linger in Environment Variables, especially on servers/dev machines
🟠 One compromised endpoint could thus lead to a full cloud breach
🔍 Hunt for exposed tokens - if you can see it, so could an attacker (well, kinda)
Any activity concerning these registry keys should be consider suspicious.
Full story here: youtu.be/7MDHhavM5GM

Any activity concerning these registry keys should be consider suspicious.
Full story here: youtu.be/7MDHhavM5GM
⚡ By using a Launch Daemon, you can leverage all the app's TCC permissions
🔍 Hunt for processes with ELECTRON_RUN_AS_NODE env var and unusual command lines
⚡ By using a Launch Daemon, you can leverage all the app's TCC permissions
🔍 Hunt for processes with ELECTRON_RUN_AS_NODE env var and unusual command lines
Instead of exports, ordinals can be used too. You could hunt for known bad ones, but are ordinals used legitimately that often at all?
Look for rundll32 with # on the command line to find out

Instead of exports, ordinals can be used too. You could hunt for known bad ones, but are ordinals used legitimately that often at all?
Look for rundll32 with # on the command line to find out
🔴 Hard to delete/rename
🟠 Can hide (malicious) content when the same folder without trailing space exists
🟡 May enable UAC bypass (see next msg)
🔍 Hunt for paths with trailing spaces - highly sus
🔴 Hard to delete/rename
🟠 Can hide (malicious) content when the same folder without trailing space exists
🟡 May enable UAC bypass (see next msg)
🔍 Hunt for paths with trailing spaces - highly sus




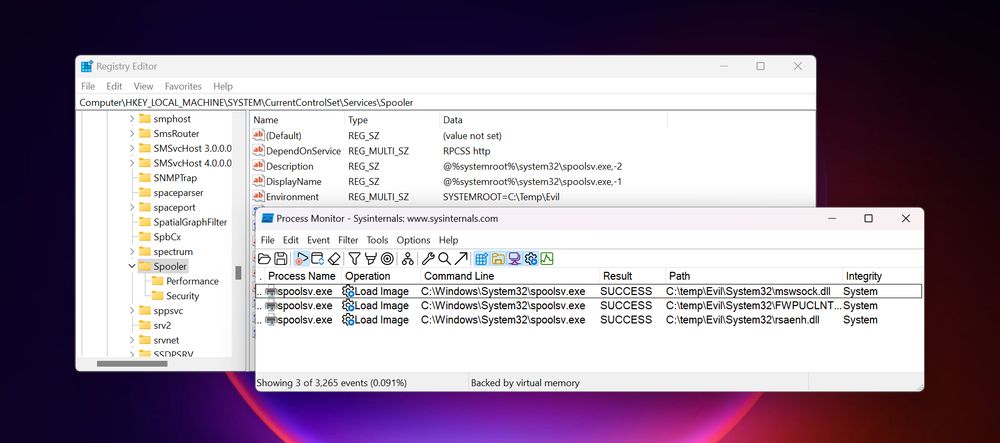









Check out individual entries, or use the API to integrate all data into your security pipeline: hijacklibs.net/api/
#cyberdefense #blueteam
Check out individual entries, or use the API to integrate all data into your security pipeline: hijacklibs.net/api/
#cyberdefense #blueteam
Huge thanks & congrats to the @attack.mitre.org team on this release 🎉

Huge thanks & congrats to the @attack.mitre.org team on this release 🎉
My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...

My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...

