
ThreatInsight
@threatinsight.proofpoint.com
Proofpoint's insights on targeted attacks and the cybersecurity threat landscape.
New research from @ThreatInsight 🚨 Deviations in typical activities by known Iranian-linked threat actors has resulted in Proofpoint threat researchers naming a new temporary threat actor cluster, UNK_SmudgedSerpent.
Blog: www.proofpoint.com/us/blog/thre...
Blog: www.proofpoint.com/us/blog/thre...

November 6, 2025 at 5:05 PM
New research from @ThreatInsight 🚨 Deviations in typical activities by known Iranian-linked threat actors has resulted in Proofpoint threat researchers naming a new temporary threat actor cluster, UNK_SmudgedSerpent.
Blog: www.proofpoint.com/us/blog/thre...
Blog: www.proofpoint.com/us/blog/thre...
Hackers compromise trucking/transport companies, then post fake "loads" for truckers & brokers to claim.
⬇️
Once the trucker replies, they infect them with malicious RMMs to overtake their company. They then try to bid on real loads to intercept and pick them up.
⬇️
The stolen physical goods are sold.
⬇️
Once the trucker replies, they infect them with malicious RMMs to overtake their company. They then try to bid on real loads to intercept and pick them up.
⬇️
The stolen physical goods are sold.

November 3, 2025 at 1:45 PM
Hackers compromise trucking/transport companies, then post fake "loads" for truckers & brokers to claim.
⬇️
Once the trucker replies, they infect them with malicious RMMs to overtake their company. They then try to bid on real loads to intercept and pick them up.
⬇️
The stolen physical goods are sold.
⬇️
Once the trucker replies, they infect them with malicious RMMs to overtake their company. They then try to bid on real loads to intercept and pick them up.
⬇️
The stolen physical goods are sold.
If the ClickFix instructions are followed, it will execute a remote PowerShell script that disables AMSI, loads a memory‑only .NET loader (included in the script) which injects an XWorm payload into RegSvcs.exe, clears the clipboard, and exits.


October 20, 2025 at 9:31 PM
If the ClickFix instructions are followed, it will execute a remote PowerShell script that disables AMSI, loads a memory‑only .NET loader (included in the script) which injects an XWorm payload into RegSvcs.exe, clears the clipboard, and exits.
The compromised websites redirect the user to the attacker-controlled domain, which performs IP filtering. If passed, the visitor is redirected to the LP which contains a matching themed page with a "Slide" CAPTCHA. If the CAPTCHA is resolved, a ClickFix page guides users to follow instructions.

October 20, 2025 at 9:31 PM
The compromised websites redirect the user to the attacker-controlled domain, which performs IP filtering. If passed, the visitor is redirected to the LP which contains a matching themed page with a "Slide" CAPTCHA. If the CAPTCHA is resolved, a ClickFix page guides users to follow instructions.
Since 14 October, we’ve tracked a high volume XWorm campaign targeting Germany. The activity is attributed to TA584, a sophisticated #cybercrime group tracked since 2020.
Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.
Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.

October 20, 2025 at 9:31 PM
Since 14 October, we’ve tracked a high volume XWorm campaign targeting Germany. The activity is attributed to TA584, a sophisticated #cybercrime group tracked since 2020.
Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.
Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.
Our blog also details TA585 campaigns. One interesting example was in August 2025, when it leveraged GitHub email notifications to deliver Rhadamanthys.

October 13, 2025 at 8:35 PM
Our blog also details TA585 campaigns. One interesting example was in August 2025, when it leveraged GitHub email notifications to deliver Rhadamanthys.
Researchers at Proofpoint have uncovered a recent brute force campaign, tracked as UNK_CustomCloak, targeting the first-party app, Windows Live Custom Domains.
Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.
Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.

October 10, 2025 at 3:40 PM
Researchers at Proofpoint have uncovered a recent brute force campaign, tracked as UNK_CustomCloak, targeting the first-party app, Windows Live Custom Domains.
Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.
Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.
Key finding 2️⃣: Instead of traditional #malware, the campaigns deployed Visual Studio Code Remote Tunnels.
This is likely a concerted effort from #TA415 to blend in with existing legitimate traffic to trusted services, including Google Sheets/Calendar, & VS Code Remote Tunnels.
This is likely a concerted effort from #TA415 to blend in with existing legitimate traffic to trusted services, including Google Sheets/Calendar, & VS Code Remote Tunnels.

September 18, 2025 at 5:11 PM
The group is impersonating trusted orgs and policymakers to target U.S. government, academic, and think tank targets.
Key finding 1️⃣: TA415 spoofed the U.S.-China Business Council and a senior congressional leader to deliver spearphishing lures tied to trade and sanctions policy.
Key finding 1️⃣: TA415 spoofed the U.S.-China Business Council and a senior congressional leader to deliver spearphishing lures tied to trade and sanctions policy.

September 18, 2025 at 5:11 PM
The group is impersonating trusted orgs and policymakers to target U.S. government, academic, and think tank targets.
Key finding 1️⃣: TA415 spoofed the U.S.-China Business Council and a senior congressional leader to deliver spearphishing lures tied to trade and sanctions policy.
Key finding 1️⃣: TA415 spoofed the U.S.-China Business Council and a senior congressional leader to deliver spearphishing lures tied to trade and sanctions policy.
The downloaded file is always named “fix.zip”, which contains “x86_64-w64-ranlib.exe” and “msvcp140.dll”. If the executable is run, it launches #Lumma via “msbuild.exe”.

September 3, 2025 at 6:32 PM
The downloaded file is always named “fix.zip”, which contains “x86_64-w64-ranlib.exe” and “msvcp140.dll”. If the executable is run, it launches #Lumma via “msbuild.exe”.
Threat actors continue to abuse GitHub to deliver malware, this time: #LummaStealer. We identified GitHub notification emails that kick off the attack chain. Messages are sent when the threat actor, using an actor-controlled account, comments on existing GitHub issues. 🧵

September 3, 2025 at 6:23 PM
Threat actors continue to abuse GitHub to deliver malware, this time: #LummaStealer. We identified GitHub notification emails that kick off the attack chain. Messages are sent when the threat actor, using an actor-controlled account, comments on existing GitHub issues. 🧵
Threat actors are exploiting #Microsoft365 Direct Send to make their phishing campaigns appear to originate from inside an organization.
On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5
On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5

August 29, 2025 at 8:09 PM
Threat actors are exploiting #Microsoft365 Direct Send to make their phishing campaigns appear to originate from inside an organization.
On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5
On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5
Something #spicy is coming to the next Only Malware in the Building podcast—dropping September 2. 🌶️
Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones
Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones

August 21, 2025 at 7:15 PM
Something #spicy is coming to the next Only Malware in the Building podcast—dropping September 2. 🌶️
Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones
Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones
We have flagged tens of thousands of Lovable URLs as threats each month in email and SMS data since Feb 2025.
Threat actors create or clone websites that impersonate prominent brands, use CAPTCHA for filtering, and then post credentials to Telegram.
Threat actors create or clone websites that impersonate prominent brands, use CAPTCHA for filtering, and then post credentials to Telegram.

August 20, 2025 at 3:40 PM
We have flagged tens of thousands of Lovable URLs as threats each month in email and SMS data since Feb 2025.
Threat actors create or clone websites that impersonate prominent brands, use CAPTCHA for filtering, and then post credentials to Telegram.
Threat actors create or clone websites that impersonate prominent brands, use CAPTCHA for filtering, and then post credentials to Telegram.
You asked, we answered. AI tools are significantly lowering the barrier to entry for cybercriminals.
We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo
We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo

August 20, 2025 at 3:40 PM
You asked, we answered. AI tools are significantly lowering the barrier to entry for cybercriminals.
We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo
We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo
The notifications contain shortened URLs that will lead to an actor-controlled website. The website will perform filtering functions, and if those checks are passed, the visitor will be redirected to a website that presents a fake GitHub-branded CAPTCHA instructing users to verify they are human.

August 18, 2025 at 6:31 PM
The notifications contain shortened URLs that will lead to an actor-controlled website. The website will perform filtering functions, and if those checks are passed, the visitor will be redirected to a website that presents a fake GitHub-branded CAPTCHA instructing users to verify they are human.
We identified GitHub notification emails that start the attack chain. The threat actor likely generates the emails by creating an issue in an actor-controlled repository with a fake security warning, and then tags legitimate accounts who receive notifications with the text from the issue.

August 18, 2025 at 6:31 PM
We identified GitHub notification emails that start the attack chain. The threat actor likely generates the emails by creating an issue in an actor-controlled repository with a fake security warning, and then tags legitimate accounts who receive notifications with the text from the issue.
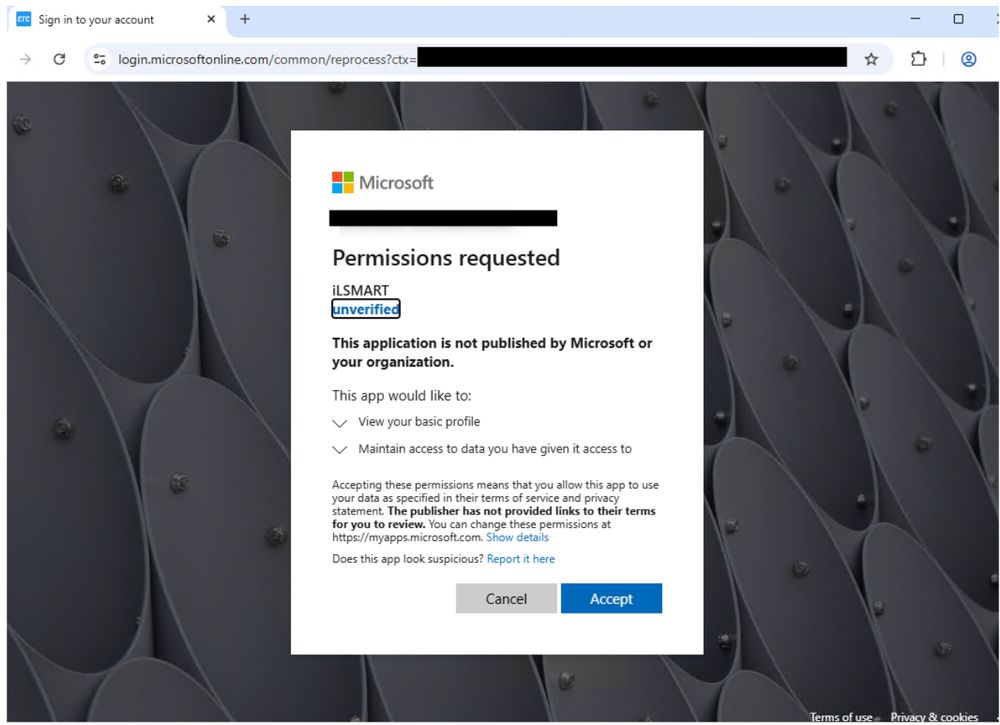
In the email campaigns tracked by Proofpoint, messages are often sent from compromised email accounts and include subjects related to request for quotes or business contract agreements. The campaigns typically include thousands of messages and impact hundreds of customers.
July 31, 2025 at 11:44 PM
In the email campaigns tracked by Proofpoint, messages are often sent from compromised email accounts and include subjects related to request for quotes or business contract agreements. The campaigns typically include thousands of messages and impact hundreds of customers.
Each threat actor has its own tactics, techniques, and procedures (TTPs).
On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L
On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L

July 29, 2025 at 6:46 PM
Each threat actor has its own tactics, techniques, and procedures (TTPs).
On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L
On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L
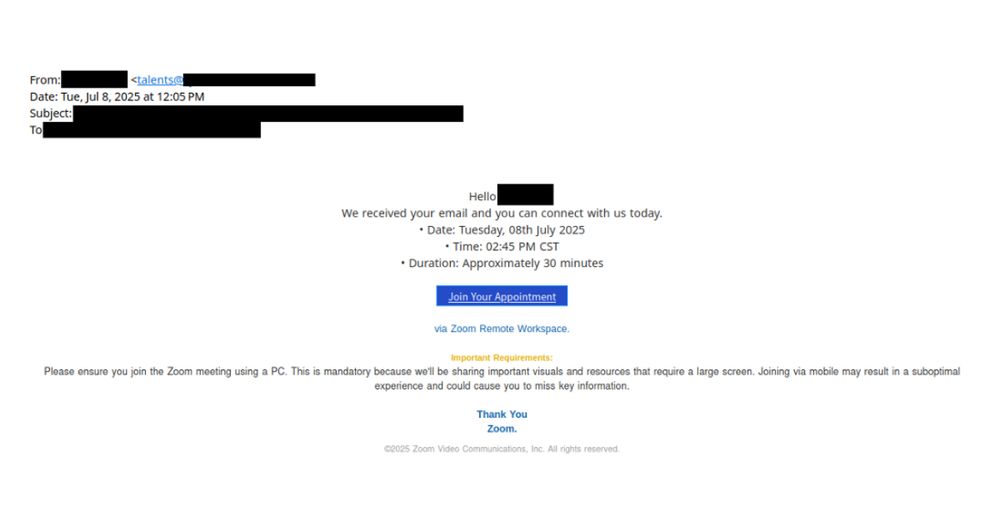
In recent campaigns, emails may be compromised or impersonate real firms. Senders have names associated w/ recruiters or company employees. Email bodies relate to job apps. We were able to identify multiple jobs named in the scam emails that were posted by the impersonated or compromised companies.
July 24, 2025 at 3:41 PM
In recent campaigns, emails may be compromised or impersonate real firms. Senders have names associated w/ recruiters or company employees. Email bodies relate to job apps. We were able to identify multiple jobs named in the scam emails that were posted by the impersonated or compromised companies.
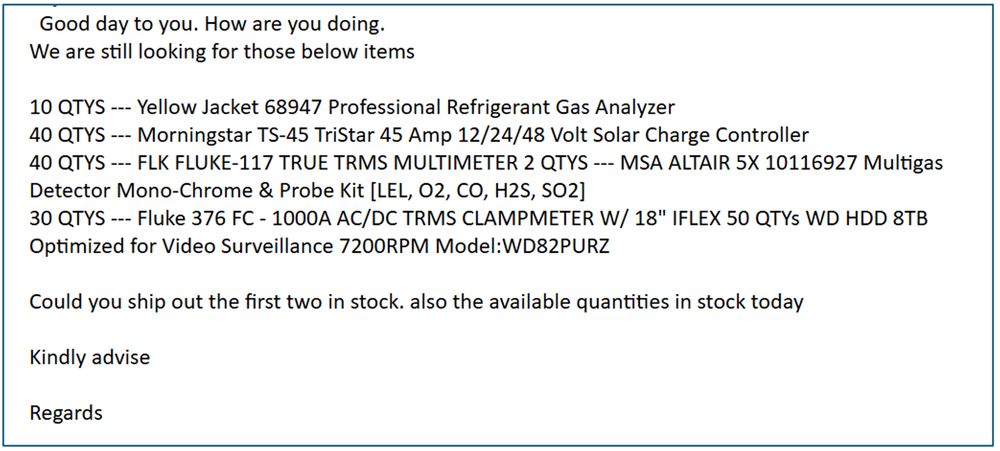
To understand how the scam works, we posed as suppliers with lax #finance departments and engaged directly w/ threat actors.
Many sent quote requests from #freemail accounts, but some used lookalike domains.
The emails typically requested highly specific items (example below).
Many sent quote requests from #freemail accounts, but some used lookalike domains.
The emails typically requested highly specific items (example below).
July 22, 2025 at 3:06 PM
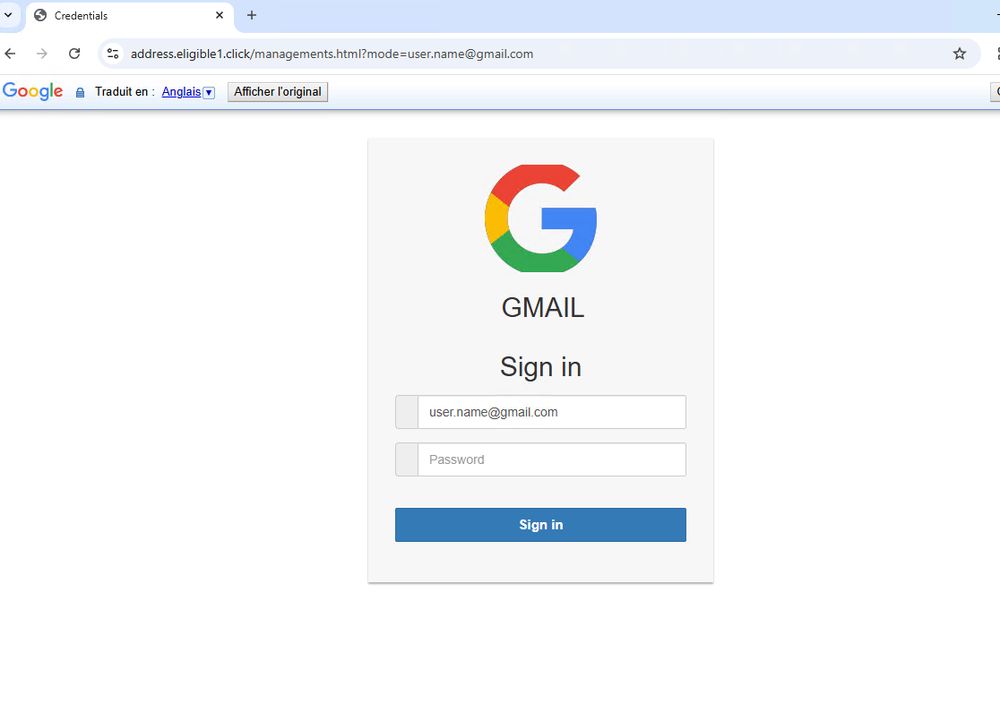
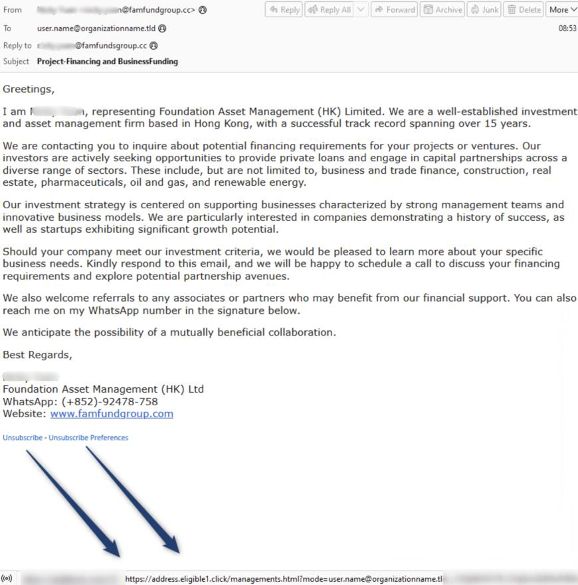
Below the sender’s signature is hyperlinked text purporting to be an “unsubscribe” option for recipients to remove themselves from the mailing list.
If clicked, it actually leads to a bogus authentication page designed to harvest credentials.
If clicked, it actually leads to a bogus authentication page designed to harvest credentials.
July 1, 2025 at 4:30 PM
Below the sender’s signature is hyperlinked text purporting to be an “unsubscribe” option for recipients to remove themselves from the mailing list.
If clicked, it actually leads to a bogus authentication page designed to harvest credentials.
If clicked, it actually leads to a bogus authentication page designed to harvest credentials.
Confirm before you click! 🖱️
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
July 1, 2025 at 4:30 PM
Confirm before you click! 🖱️
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
TA4557 is highly active with its specific targeting.
Last week, we observed the actor use its typical TTPs to deliver emails with new geographic targeting, with emails and landing pages aligned to the geographic region.
Below is a French language example.
Last week, we observed the actor use its typical TTPs to deliver emails with new geographic targeting, with emails and landing pages aligned to the geographic region.
Below is a French language example.


June 16, 2025 at 3:09 PM
TA4557 is highly active with its specific targeting.
Last week, we observed the actor use its typical TTPs to deliver emails with new geographic targeting, with emails and landing pages aligned to the geographic region.
Below is a French language example.
Last week, we observed the actor use its typical TTPs to deliver emails with new geographic targeting, with emails and landing pages aligned to the geographic region.
Below is a French language example.
To get the target's geolocation, the malware makes a call to 'http://ip-api[.]com.
Configuration examples ⤵️
Configuration examples ⤵️

June 5, 2025 at 9:07 PM
To get the target's geolocation, the malware makes a call to 'http://ip-api[.]com.
Configuration examples ⤵️
Configuration examples ⤵️

