I sniffed raw APDU traffic off the SIM pins, decoded the UART based on the ATR, and piped it into Wireshark.
Full guide: how to wire it, decode it, and see the bytes for yourself.
🔎💥📶
github.com/theXappy/tra...




I sniffed raw APDU traffic off the SIM pins, decoded the UART based on the ATR, and piped it into Wireshark.
Full guide: how to wire it, decode it, and see the bytes for yourself.
🔎💥📶
github.com/theXappy/tra...
Made `Console.WriteLine` throw a `System.UnauthorizedAccessException`.

Made `Console.WriteLine` throw a `System.UnauthorizedAccessException`.
Installed and used `dotnet-symbol` to fetch a PDB for SharedLibrary.dll and it wasn't a complete fiasco.
10/10
learn.microsoft.com/en-us/dotnet...

Installed and used `dotnet-symbol` to fetch a PDB for SharedLibrary.dll and it wasn't a complete fiasco.
10/10
learn.microsoft.com/en-us/dotnet...
Caller created an empty struct -> Passes pointer to the func, as the last arg -> func populated the pointed struct.
* at least for MSVC for x64

Caller created an empty struct -> Passes pointer to the func, as the last arg -> func populated the pointed struct.
* at least for MSVC for x64
Damn I love reversing protocols
github.com/theXappy/Kon...
#reverseengineering #reversing #wireshark

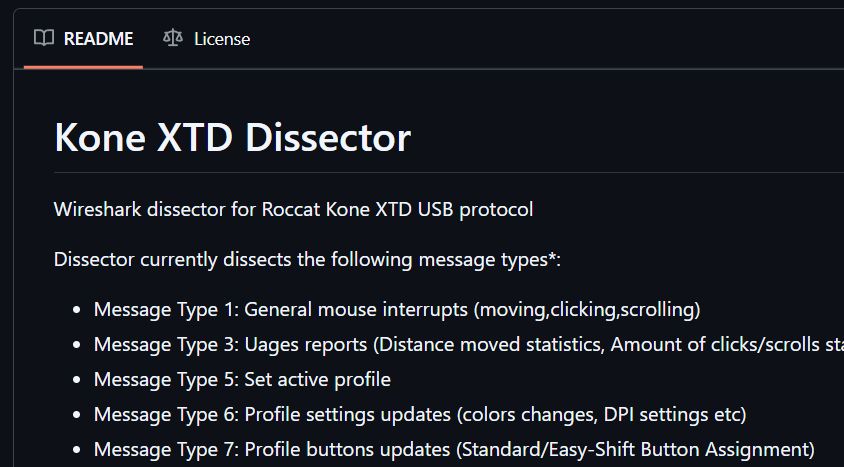
Damn I love reversing protocols
github.com/theXappy/Kon...
#reverseengineering #reversing #wireshark
therecord.media/nso-group-wh...

Early 2014, someone came to me about a catastrophic vulnerability in Apple's TLS implementation.
I shit you not, they'd overheard someone at a bar drunkenly bragging about how they were going to sell it to a FVEY intelligence agency for six figures.
The documents show how NSO targeted WhatsApp, citing depositions from NSO employees, and more.
Here are the biggest revelations.
techcrunch.com/2024/11/15/n...

The documents show how NSO targeted WhatsApp, citing depositions from NSO employees, and more.
Here are the biggest revelations.
techcrunch.com/2024/11/15/n...
One of the topics that came up at BlueHat last week was around apps. Lots of good information was covered that will be posted at www.microsoft.com/bluehat/. Until then here are some resources for you to check out. /1

One of the topics that came up at BlueHat last week was around apps. Lots of good information was covered that will be posted at www.microsoft.com/bluehat/. Until then here are some resources for you to check out. /1

