
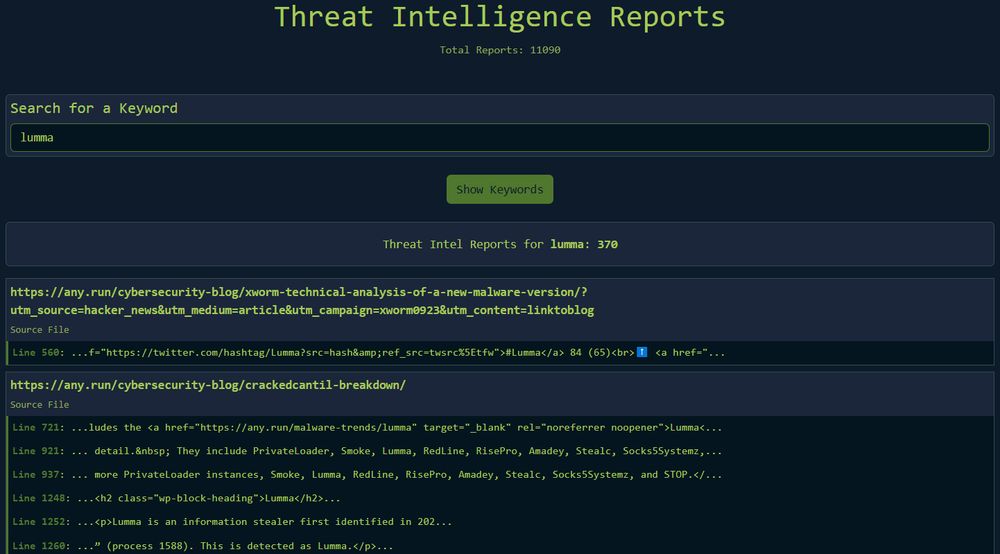
Prepare your #ThreatHunting sessions by gathering intelligence reports on specific topics - could be tools, patterns, or threat actor groups
🏛️ mthcht.github.io/ThreatIntel-...
Now featuring more than 1,000 search results in over 11,000 Intelligence Reports updated regularly!


Prepare your #ThreatHunting sessions by gathering intelligence reports on specific topics - could be tools, patterns, or threat actor groups
🏛️ mthcht.github.io/ThreatIntel-...
Now featuring more than 1,000 search results in over 11,000 Intelligence Reports updated regularly!

The warning comes days after a similar alert was issued by the BSI, Germany's cybersecurity agency: www.bsi.bund.de/SharedDocs/C...

The warning comes days after a similar alert was issued by the BSI, Germany's cybersecurity agency: www.bsi.bund.de/SharedDocs/C...
If you or someone you know aspires to be a SOC Analyst, check out my hands-on lab, "So you want to be a SOC Analyst?"
Thousands of people have been through it and the feedback has been 🔥
blog.ecapuano.com/p/so-you-wan... #infosec

If you or someone you know aspires to be a SOC Analyst, check out my hands-on lab, "So you want to be a SOC Analyst?"
Thousands of people have been through it and the feedback has been 🔥
blog.ecapuano.com/p/so-you-wan... #infosec
securityconversations.com/episode/insi...

securityconversations.com/episode/insi...
Via @lawrenceabrams.bsky.social & @bleepingcomputer.com

Via @lawrenceabrams.bsky.social & @bleepingcomputer.com



