
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.
Looks like this got caught by chance. Wonder how long it would have taken otherwise.
www.openwall.com/lists/oss-se...
It has everything: malicious upstream, masterful obfuscation, detection due to performance degradation, inclusion in OpenSSH via distro patches for systemd support…
Now I’m curious what it does in RSA_public_decrypt
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.


Today they informed me I have seven days to move the entire archive offsite. It's 150 TB.
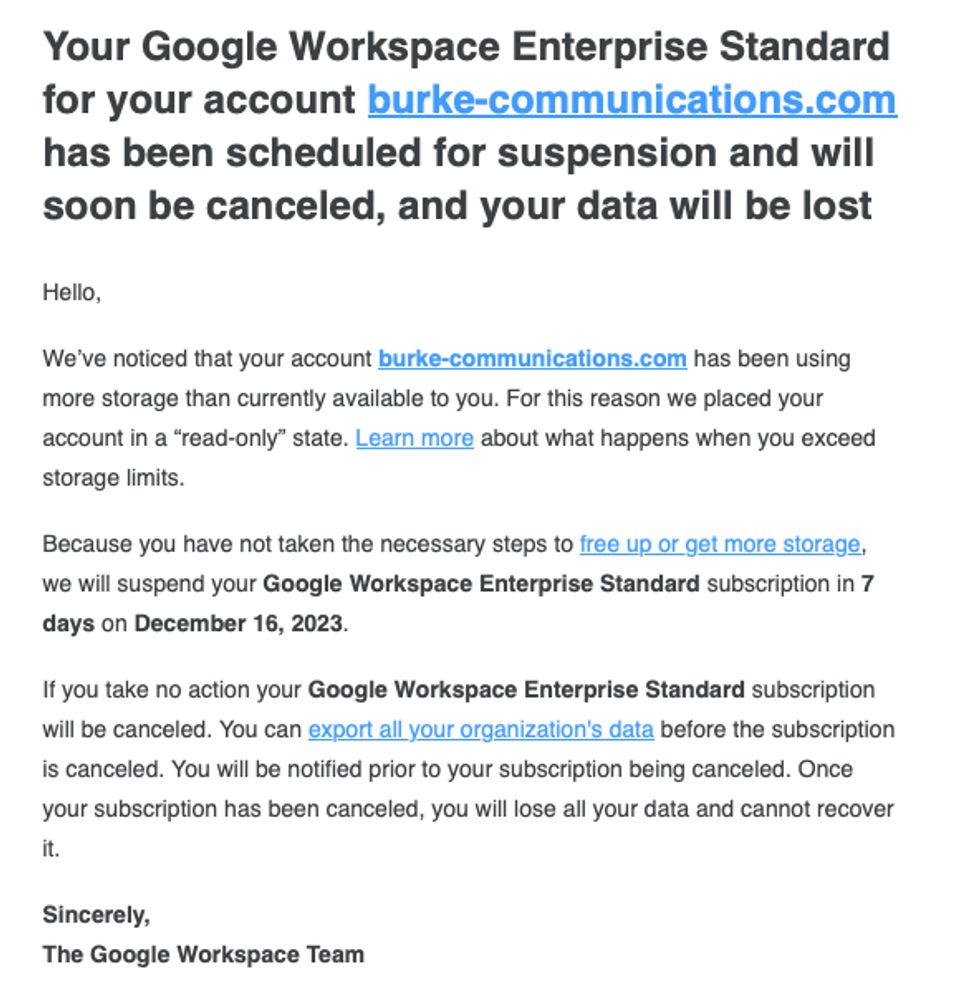
Today they informed me I have seven days to move the entire archive offsite. It's 150 TB.
www.crowdsupply.com/machinery-en...

www.crowdsupply.com/machinery-en...
Post time: 1701486310
Exposing the Flaws: Decoding the BLUFFS Attacks on Bluetooth's Secrecy Protocol
An analysis of BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
open.substack.com/pub/tengusec...

Post time: 1701486310
Exposing the Flaws: Decoding the BLUFFS Attacks on Bluetooth's Secrecy Protocol
An analysis of BLUFFS: Bluetooth Forward and Future Secrecy Attacks and Defenses
open.substack.com/pub/tengusec...
An analysis of "TRAP; RESET; POISON - Taking over a country Kaminsky style," authored by Timo Longin and the SEC Consult Vulnerability Lab
open.substack.com/pub/tengusec...

An analysis of "TRAP; RESET; POISON - Taking over a country Kaminsky style," authored by Timo Longin and the SEC Consult Vulnerability Lab
open.substack.com/pub/tengusec...
open.substack.com/pub/tengusec...
open.substack.com/pub/tengusec...








