|| Ex Mechanical Engineer
In the last thread, we explored major threats like ransomware and DDoS attacks. Now, let’s uncover three sneaky security gaps cybercriminals exploit:

In the last thread, we explored major threats like ransomware and DDoS attacks. Now, let’s uncover three sneaky security gaps cybercriminals exploit:
Imagine your company's digital security like leaving your house wide open—doors and windows included. Terrifying, right? 😱 Let's dive into three key cyber threats you MUST know:

Imagine your company's digital security like leaving your house wide open—doors and windows included. Terrifying, right? 😱 Let's dive into three key cyber threats you MUST know:
LLMs are smart, but they have a big flaw: they don’t know things beyond their training data.
RAG fixes this by letting models retrieve external info before generating responses, making them more accurate, up-to-date, and reliable. 🧠🔍
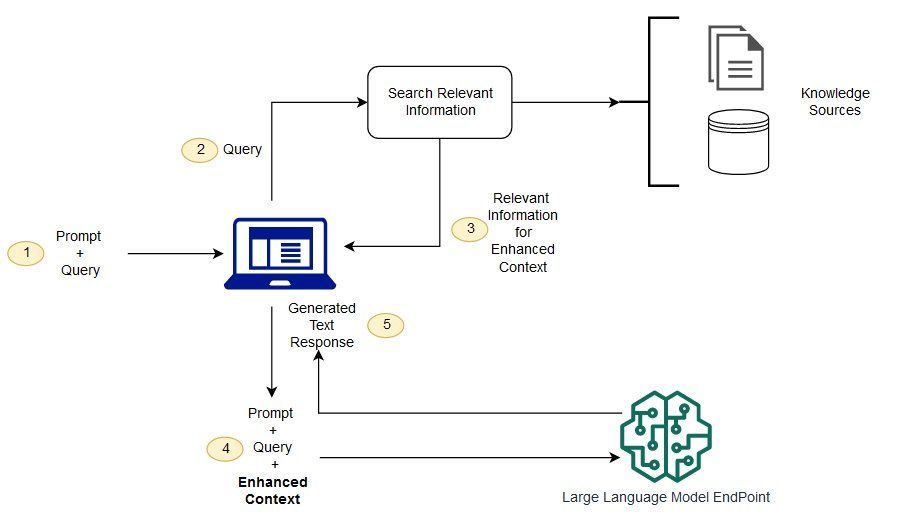
LLMs are smart, but they have a big flaw: they don’t know things beyond their training data.
RAG fixes this by letting models retrieve external info before generating responses, making them more accurate, up-to-date, and reliable. 🧠🔍
🔹 Hugging Face Agents Course – Beginner-friendly & hands-on 🚀
🔹 LangChain – Needs some Python but is powerful 💻
🔹 Relevance AI & Dify – No-code tools for non-tech users ⚡

🔹 Hugging Face Agents Course – Beginner-friendly & hands-on 🚀
🔹 LangChain – Needs some Python but is powerful 💻
🔹 Relevance AI & Dify – No-code tools for non-tech users ⚡
You’ve probably seen posts about them, but what exactly do they do? Here’s a quick, no-hype breakdown so you can understand & even build one yourself. 🧵👇
You’ve probably seen posts about them, but what exactly do they do? Here’s a quick, no-hype breakdown so you can understand & even build one yourself. 🧵👇


