That new iOS 26 jailbreak everyone's talking about? It's fake. And it's stealing your data.
Here's what @corellium.bsky.social Labs found when they tore apart #nekoJB Online 🧵

That new iOS 26 jailbreak everyone's talking about? It's fake. And it's stealing your data.
Here's what @corellium.bsky.social Labs found when they tore apart #nekoJB Online 🧵
They offer jailbroken iOS 26.0.1 on virtual devices including iPhone 17 Pro Max. No waiting for public exploits. No compromise on testing depth.
Root access across ALL iOS versions for comprehensive MAST.

They offer jailbroken iOS 26.0.1 on virtual devices including iPhone 17 Pro Max. No waiting for public exploits. No compromise on testing depth.
Root access across ALL iOS versions for comprehensive MAST.
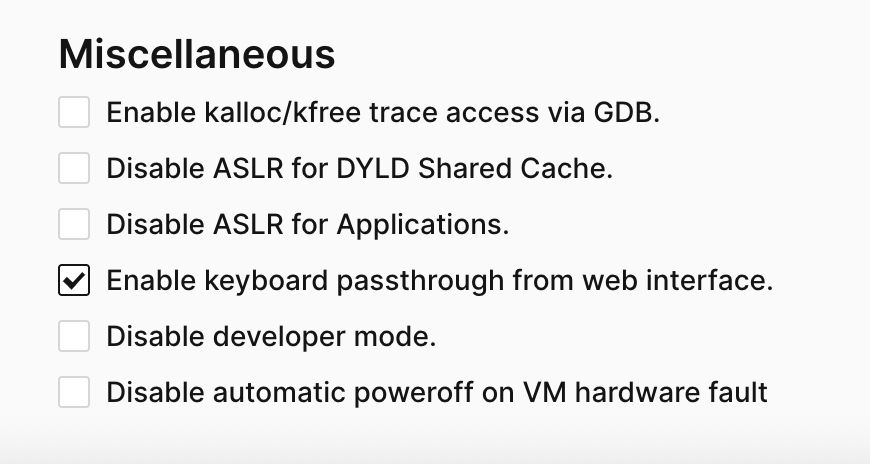
Platforms like @corellium.bsky.social let professionals safely disable ASLR in controlled environments - like a practice gym for cybersecurity experts.
This is how we stay ahead of attackers! 💪
#iOS
Platforms like @corellium.bsky.social let professionals safely disable ASLR in controlled environments - like a practice gym for cybersecurity experts.
This is how we stay ahead of attackers! 💪
#iOS
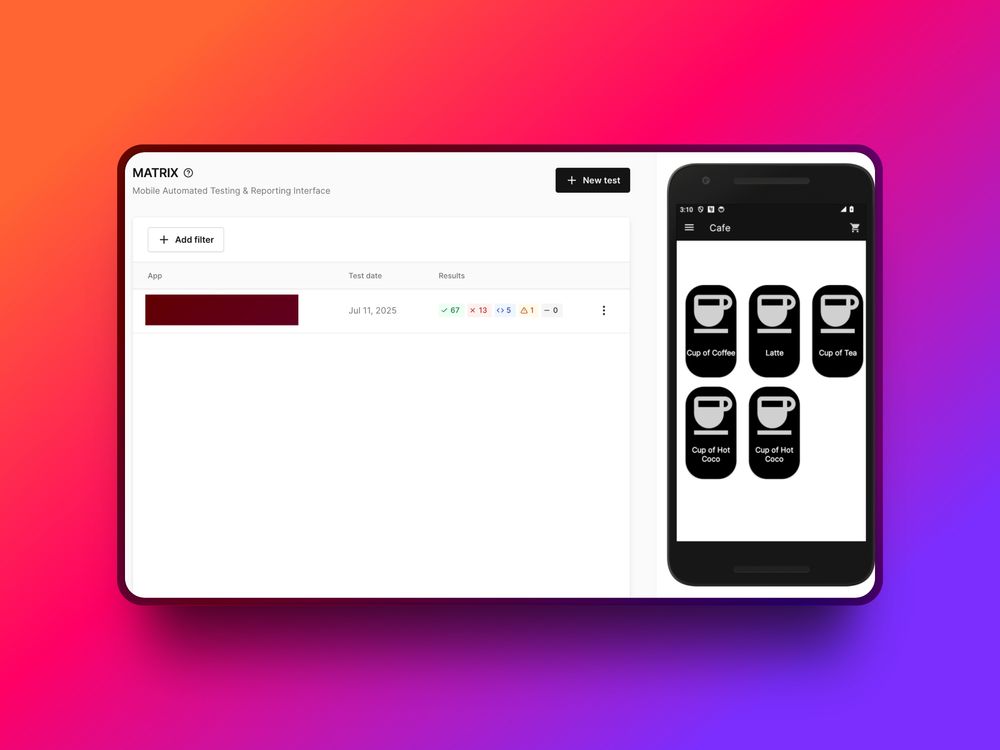
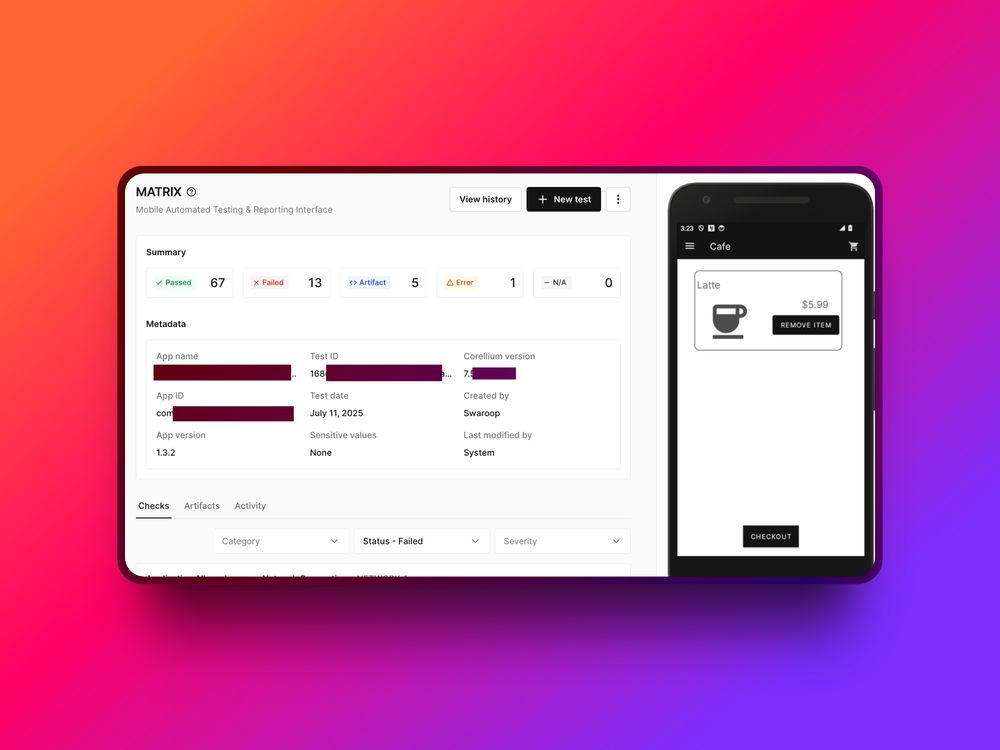
Platforms like @corellium.bsky.social's MATRIX feature automatically map findings to compliance standards (PCI DSS v4, GDPR, HIPAA), catching violations early.

Platforms like @corellium.bsky.social's MATRIX feature automatically map findings to compliance standards (PCI DSS v4, GDPR, HIPAA), catching violations early.



Getting started?
Try tools like @corellium.bsky.social to spin up iOS/Android in seconds & test safely.
What’s the wildest mobile bug you’ve found? Drop it below 👇
#BugBounty #MobileSecurity #CyberSecurity #InfoSec #Corellium

Getting started?
Try tools like @corellium.bsky.social to spin up iOS/Android in seconds & test safely.
What’s the wildest mobile bug you’ve found? Drop it below 👇
#BugBounty #MobileSecurity #CyberSecurity #InfoSec #Corellium
Always decrypt first before static analysis.
Skipping this step = false negatives & weak security reports.
#iOSSecurity #MobilePentesting #AppSec #Corellium

Always decrypt first before static analysis.
Skipping this step = false negatives & weak security reports.
#iOSSecurity #MobilePentesting #AppSec #Corellium
Platforms like @corellium.bsky.social make this possible by letting you safely analyze SDK behavior in virtual devices.
The question isn’t if your dependencies are secure - it’s whether you’ll find out before your users do #Corellium

Platforms like @corellium.bsky.social make this possible by letting you safely analyze SDK behavior in virtual devices.
The question isn’t if your dependencies are secure - it’s whether you’ll find out before your users do #Corellium
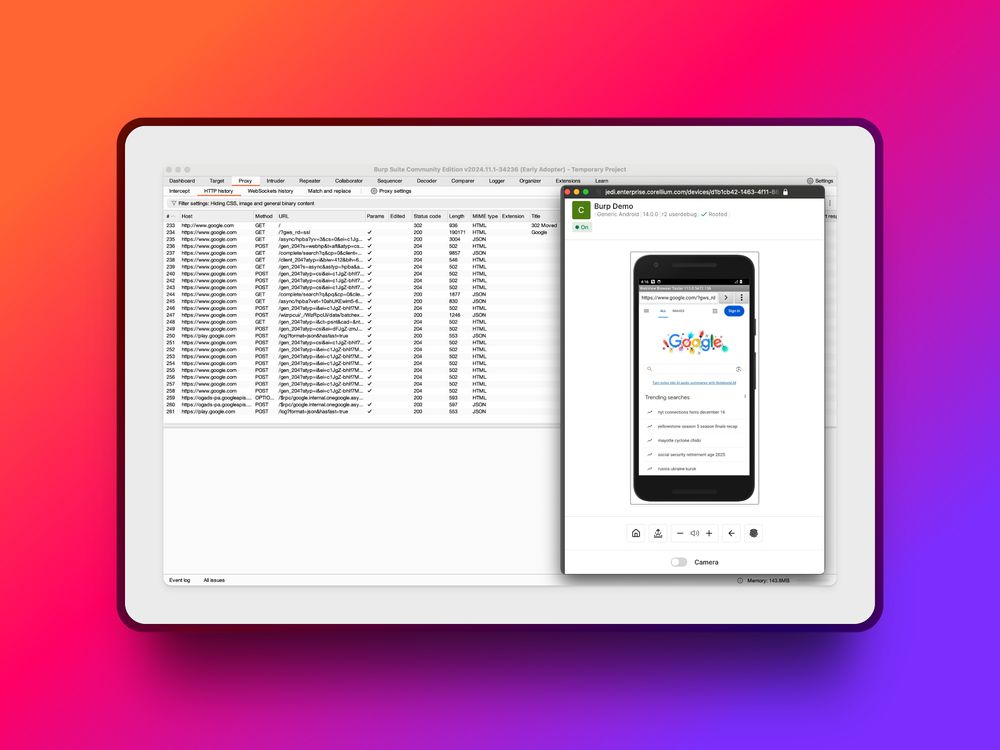
Platforms like @corellium.bsky.social let teams test mobile apps & APIs in realistic environments - trace every call, check auth flows, and find issues before they become headlines.
How does your team test mobile app APIs?
#MobileSecurity #MobileApp #Corellium #CyberSecurity
Platforms like @corellium.bsky.social let teams test mobile apps & APIs in realistic environments - trace every call, check auth flows, and find issues before they become headlines.
How does your team test mobile app APIs?
#MobileSecurity #MobileApp #Corellium #CyberSecurity
⚠️ 91% of organizations faced a software supply chain attack in 2024.
Mobile apps aren’t immune.
The SpinOK malware case proves it:
101 Android apps infected via a malicious ad SDK.
43 still live on Google Play-some with over 5M downloads.
⚠️ 91% of organizations faced a software supply chain attack in 2024.
Mobile apps aren’t immune.
The SpinOK malware case proves it:
101 Android apps infected via a malicious ad SDK.
43 still live on Google Play-some with over 5M downloads.
A new invisible Android attack just dropped… and it's sneaky.
Researchers from TU Wien & University of Bayreuth discovered TapTrap – a tapjacking technique that tricks users into giving dangerous permissions without knowing.
#TapTrap #mobilesecurity
A new invisible Android attack just dropped… and it's sneaky.
Researchers from TU Wien & University of Bayreuth discovered TapTrap – a tapjacking technique that tricks users into giving dangerous permissions without knowing.
#TapTrap #mobilesecurity
The world is in a mobile security crisis 📱⚠️
A recent AP investigation revealed that hackers are silently targeting smartphones of officials, journalists, and tech workers using zero-click attacks.
These attacks leave no trace.
The world is in a mobile security crisis 📱⚠️
A recent AP investigation revealed that hackers are silently targeting smartphones of officials, journalists, and tech workers using zero-click attacks.
These attacks leave no trace.
In April 2025, a researcher bought a budget smartphone online. Looked legit. Pre-installed messaging apps. No red flags.
Then they tried sending crypto… and it was silently hijacked.
#SupplyChainSecurity #MobileSecurity #RuntimeTesting #Corellium

In April 2025, a researcher bought a budget smartphone online. Looked legit. Pre-installed messaging apps. No red flags.
Then they tried sending crypto… and it was silently hijacked.
#SupplyChainSecurity #MobileSecurity #RuntimeTesting #Corellium
Step 1: Get a jailbroken device
unc0ver (iOS 11-14.8)
palera1n (newer versions)
Check Can I Jailbreak? for compatibility
⚠️ New iPhones come with latest iOS = no public jailbreak. Buy older devices!
#iOSSecurity

Step 1: Get a jailbroken device
unc0ver (iOS 11-14.8)
palera1n (newer versions)
Check Can I Jailbreak? for compatibility
⚠️ New iPhones come with latest iOS = no public jailbreak. Buy older devices!
#iOSSecurity

🚨 SparkCat Malware Alert: "Safe" apps on Google Play and Apple App Store were stealing crypto wallet recovery phrases from your photos. Here's what happened and how to stay safe 🧵
#CyberSecurity #MobileSecurity #Cryptocurrency #AppSecurity #Corellium

🚨 SparkCat Malware Alert: "Safe" apps on Google Play and Apple App Store were stealing crypto wallet recovery phrases from your photos. Here's what happened and how to stay safe 🧵
#CyberSecurity #MobileSecurity #Cryptocurrency #AppSecurity #Corellium
Most teams are not testing for it, and it is surprisingly easy to exploit.
#MobileSecurity #Corellium #VulnerabilityResearch #CyberSecurity #AppSec

Most teams are not testing for it, and it is surprisingly easy to exploit.
#MobileSecurity #Corellium #VulnerabilityResearch #CyberSecurity #AppSec
Reverse engineering iOS apps is tough - no public jailbreaks, code signing issues, and getting decrypted IPAs is a pain.
It gets even harder with iOS 18+.
But using Ghidra + a virtual iPhone changed everything for me. 🧵

Reverse engineering iOS apps is tough - no public jailbreaks, code signing issues, and getting decrypted IPAs is a pain.
It gets even harder with iOS 18+.
But using Ghidra + a virtual iPhone changed everything for me. 🧵
The new SANS product review of @corellium.bsky.social validates what we've all been dealing with - iOS security testing with physical devices just isn't working anymore.

The new SANS product review of @corellium.bsky.social validates what we've all been dealing with - iOS security testing with physical devices just isn't working anymore.
“10 iPhones in my luggage” — that’s what iOS security training used to look like.
Throwback to AppSec USA when I had to bring 8–10 physical devices to every session. It was… a process.

“10 iPhones in my luggage” — that’s what iOS security training used to look like.
Throwback to AppSec USA when I had to bring 8–10 physical devices to every session. It was… a process.

The recent Perplexity AI Android app launched with 10 security bugs that put users at risk for months. In past roles, I've heard "we can fix security later" too many times.

The recent Perplexity AI Android app launched with 10 security bugs that put users at risk for months. In past roles, I've heard "we can fix security later" too many times.
Why? Lack of transparency in data handling and unclear privacy policies.
A wake-up call for mobile apps. 🧵

Why? Lack of transparency in data handling and unclear privacy policies.
A wake-up call for mobile apps. 🧵

