
Sudo Truth
@sudotruth.bsky.social
Sudo Truth: Intelligent cyber defense. Custom business security solutions. AI + human expertise = accurate insights.
More at https://sudotruth.com
Substack: https://sudotruth.substack.com
Medium: https://medium.com/@sudotruth
More at https://sudotruth.com
Substack: https://sudotruth.substack.com
Medium: https://medium.com/@sudotruth
#Cybersecurity #IndustryInsights
Insider risk is real: cases where #security professionals turn rogue highlight the threat of internal actors monetizing access, underscoring the need for strict #access controls and ongoing monitoring.
Insider risk is real: cases where #security professionals turn rogue highlight the threat of internal actors monetizing access, underscoring the need for strict #access controls and ongoing monitoring.

November 11, 2025 at 4:41 PM
#Cybersecurity #IndustryInsights
Insider risk is real: cases where #security professionals turn rogue highlight the threat of internal actors monetizing access, underscoring the need for strict #access controls and ongoing monitoring.
Insider risk is real: cases where #security professionals turn rogue highlight the threat of internal actors monetizing access, underscoring the need for strict #access controls and ongoing monitoring.
Monday thought: In the enterprise, privacy and cybersecurity aren't IT issues; they're business imperatives.
With work-from-home, where are your biggest gaps: data minimization, endpoint hygiene, or access control?
How will you fix them this quarter?
#CyberSecurity #Privacy #WFH
With work-from-home, where are your biggest gaps: data minimization, endpoint hygiene, or access control?
How will you fix them this quarter?
#CyberSecurity #Privacy #WFH
November 10, 2025 at 4:27 PM
Monday thought: In the enterprise, privacy and cybersecurity aren't IT issues; they're business imperatives.
With work-from-home, where are your biggest gaps: data minimization, endpoint hygiene, or access control?
How will you fix them this quarter?
#CyberSecurity #Privacy #WFH
With work-from-home, where are your biggest gaps: data minimization, endpoint hygiene, or access control?
How will you fix them this quarter?
#CyberSecurity #Privacy #WFH
Reposted by Sudo Truth
Unfortunately, it's how privacy works :( timsh.org/tracking-mys...
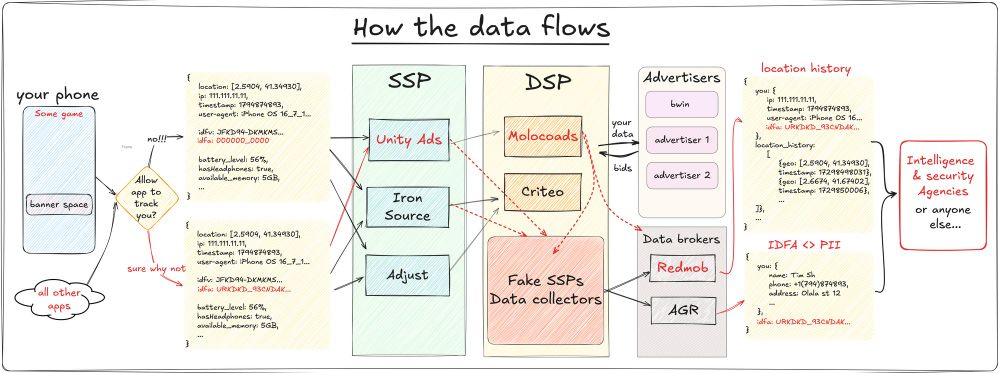
Everyone knows your location
How I tracked myself down using leaked location data in the in-app ads, and what I found along the way.
timsh.org
February 12, 2025 at 3:31 PM
Unfortunately, it's how privacy works :( timsh.org/tracking-mys...
Throwback:
On this day in 1980, Microsoft inks a contract with IBM to build the OS for the IBM PC. MS-DOS, born from a Seattle foundation, would ignite home computing and launch Bill Gates & Paul Allen’s empire.
#TechHistory #MSDOS #IBMPC #Microsoft #ThrowbackThursday
On this day in 1980, Microsoft inks a contract with IBM to build the OS for the IBM PC. MS-DOS, born from a Seattle foundation, would ignite home computing and launch Bill Gates & Paul Allen’s empire.
#TechHistory #MSDOS #IBMPC #Microsoft #ThrowbackThursday


November 6, 2025 at 6:31 PM
Throwback:
On this day in 1980, Microsoft inks a contract with IBM to build the OS for the IBM PC. MS-DOS, born from a Seattle foundation, would ignite home computing and launch Bill Gates & Paul Allen’s empire.
#TechHistory #MSDOS #IBMPC #Microsoft #ThrowbackThursday
On this day in 1980, Microsoft inks a contract with IBM to build the OS for the IBM PC. MS-DOS, born from a Seattle foundation, would ignite home computing and launch Bill Gates & Paul Allen’s empire.
#TechHistory #MSDOS #IBMPC #Microsoft #ThrowbackThursday
#Cybersecurity Tip:
Build security into the #Software Development Life Cycle (SDLC) from day one. Require developers to run an ongoing security testing plan (unit, integration, system, regression), capture evidence, and fix flaws fast. Tailor test depth to #risk and document outcomes.
Build security into the #Software Development Life Cycle (SDLC) from day one. Require developers to run an ongoing security testing plan (unit, integration, system, regression), capture evidence, and fix flaws fast. Tailor test depth to #risk and document outcomes.

November 5, 2025 at 6:06 PM
#Cybersecurity Tip:
Build security into the #Software Development Life Cycle (SDLC) from day one. Require developers to run an ongoing security testing plan (unit, integration, system, regression), capture evidence, and fix flaws fast. Tailor test depth to #risk and document outcomes.
Build security into the #Software Development Life Cycle (SDLC) from day one. Require developers to run an ongoing security testing plan (unit, integration, system, regression), capture evidence, and fix flaws fast. Tailor test depth to #risk and document outcomes.
AI literacy is a must for security. AvePoint: 75% of orgs saw data-security incidents in AI rollouts; 68% cite data quality and security concerns. 99.5% are training staff. SOCs must blend human judgment with ML; beware shadow AI.
#CyberSecurity #AI #InfoSec
#CyberSecurity #AI #InfoSec

November 4, 2025 at 3:28 PM
AI literacy is a must for security. AvePoint: 75% of orgs saw data-security incidents in AI rollouts; 68% cite data quality and security concerns. 99.5% are training staff. SOCs must blend human judgment with ML; beware shadow AI.
#CyberSecurity #AI #InfoSec
#CyberSecurity #AI #InfoSec
If you could fix one cybersecurity gap today, what would it be? Describe the risk and your first 7-day win to cut exposure.
Bonus: one resource you’d deploy.
#InfoSec #ThreatHunting #CISOlife
Bonus: one resource you’d deploy.
#InfoSec #ThreatHunting #CISOlife
November 3, 2025 at 6:48 PM
If you could fix one cybersecurity gap today, what would it be? Describe the risk and your first 7-day win to cut exposure.
Bonus: one resource you’d deploy.
#InfoSec #ThreatHunting #CISOlife
Bonus: one resource you’d deploy.
#InfoSec #ThreatHunting #CISOlife
Throwback:
Oct 30, 2000 — the last Multics time-sharing OS was shut down at Canada's Department of National Defence in Halifax. A landmark in computing history: Multics helped shape Unix and modern OS design.
#TechHistory #Multics #Unix #Halifax #Computing
Oct 30, 2000 — the last Multics time-sharing OS was shut down at Canada's Department of National Defence in Halifax. A landmark in computing history: Multics helped shape Unix and modern OS design.
#TechHistory #Multics #Unix #Halifax #Computing

October 30, 2025 at 4:26 PM
Throwback:
Oct 30, 2000 — the last Multics time-sharing OS was shut down at Canada's Department of National Defence in Halifax. A landmark in computing history: Multics helped shape Unix and modern OS design.
#TechHistory #Multics #Unix #Halifax #Computing
Oct 30, 2000 — the last Multics time-sharing OS was shut down at Canada's Department of National Defence in Halifax. A landmark in computing history: Multics helped shape Unix and modern OS design.
#TechHistory #Multics #Unix #Halifax #Computing
#Cybersecurity Tip:
Make startup/shutdown a safety check. Use automated tests that run at boot, restart, or shutdown to verify privacy and security features. If something looks off, get alerts and follow a simple recovery plan. Keep an easy activity log.
#Cybersecurity #Privacy #InfoSec
Make startup/shutdown a safety check. Use automated tests that run at boot, restart, or shutdown to verify privacy and security features. If something looks off, get alerts and follow a simple recovery plan. Keep an easy activity log.
#Cybersecurity #Privacy #InfoSec

October 29, 2025 at 4:07 PM
#Cybersecurity Tip:
Make startup/shutdown a safety check. Use automated tests that run at boot, restart, or shutdown to verify privacy and security features. If something looks off, get alerts and follow a simple recovery plan. Keep an easy activity log.
#Cybersecurity #Privacy #InfoSec
Make startup/shutdown a safety check. Use automated tests that run at boot, restart, or shutdown to verify privacy and security features. If something looks off, get alerts and follow a simple recovery plan. Keep an easy activity log.
#Cybersecurity #Privacy #InfoSec
AWS outage: a trillion-dollar lesson—AI-driven infra still needs robust software. CrowdStrike calls it a "platform moment" as Falcon extends to identity, cloud, threat intel. 2025 Gartner: security spend $213B; 2026 +12%.
#AI #CyberSecurity #CloudSecurity #industryInsights
#AI #CyberSecurity #CloudSecurity #industryInsights

October 28, 2025 at 5:09 PM
AWS outage: a trillion-dollar lesson—AI-driven infra still needs robust software. CrowdStrike calls it a "platform moment" as Falcon extends to identity, cloud, threat intel. 2025 Gartner: security spend $213B; 2026 +12%.
#AI #CyberSecurity #CloudSecurity #industryInsights
#AI #CyberSecurity #CloudSecurity #industryInsights
October is Cybersecurity Awareness Month.
Could cyber privateers join public-private partnerships to share real-time threat intel for rapid cross-sector containment?
What would you want in a cross-sector intel-sharing framework?
#Cybersecurity #ThreatIntelligence #PublicPrivatePartnership
Could cyber privateers join public-private partnerships to share real-time threat intel for rapid cross-sector containment?
What would you want in a cross-sector intel-sharing framework?
#Cybersecurity #ThreatIntelligence #PublicPrivatePartnership

October 27, 2025 at 3:54 PM
October is Cybersecurity Awareness Month.
Could cyber privateers join public-private partnerships to share real-time threat intel for rapid cross-sector containment?
What would you want in a cross-sector intel-sharing framework?
#Cybersecurity #ThreatIntelligence #PublicPrivatePartnership
Could cyber privateers join public-private partnerships to share real-time threat intel for rapid cross-sector containment?
What would you want in a cross-sector intel-sharing framework?
#Cybersecurity #ThreatIntelligence #PublicPrivatePartnership
Reposted by Sudo Truth
🚨 In IT hiring: don’t trust the CV, verify the person.
Call ex-employers, ask colleagues, debunk the résumé.
The wrong hire can be your biggest cyber risk.
#CyberSecurity #InsiderThreats #ITRecruitment
Call ex-employers, ask colleagues, debunk the résumé.
The wrong hire can be your biggest cyber risk.
#CyberSecurity #InsiderThreats #ITRecruitment
September 3, 2025 at 6:43 PM
🚨 In IT hiring: don’t trust the CV, verify the person.
Call ex-employers, ask colleagues, debunk the résumé.
The wrong hire can be your biggest cyber risk.
#CyberSecurity #InsiderThreats #ITRecruitment
Call ex-employers, ask colleagues, debunk the résumé.
The wrong hire can be your biggest cyber risk.
#CyberSecurity #InsiderThreats #ITRecruitment
Reposted by Sudo Truth
RedTiger Malware: The Hacker’s New Weapon Targeting Gamers Worldwide
A Silent War Behind the Screens Cybercriminals are turning the gaming world into a hunting ground. A powerful tool once meant to protect networks—RedTiger—has now been corrupted into a weapon for mass data theft. What started as…
A Silent War Behind the Screens Cybercriminals are turning the gaming world into a hunting ground. A powerful tool once meant to protect networks—RedTiger—has now been corrupted into a weapon for mass data theft. What started as…

RedTiger Malware: The Hacker’s New Weapon Targeting Gamers Worldwide
A Silent War Behind the Screens Cybercriminals are turning the gaming world into a hunting ground. A powerful tool once meant to protect networks—RedTiger—has now been corrupted into a weapon for mass data theft. What started as a legitimate red-teaming framework for ethical hackers has evolved into a sophisticated infostealer, targeting gamers, streamers, and even casual Discord users around the globe.
undercodenews.com
October 24, 2025 at 2:19 PM
RedTiger Malware: The Hacker’s New Weapon Targeting Gamers Worldwide
A Silent War Behind the Screens Cybercriminals are turning the gaming world into a hunting ground. A powerful tool once meant to protect networks—RedTiger—has now been corrupted into a weapon for mass data theft. What started as…
A Silent War Behind the Screens Cybercriminals are turning the gaming world into a hunting ground. A powerful tool once meant to protect networks—RedTiger—has now been corrupted into a weapon for mass data theft. What started as…
Throwback Thursday:
Oct 23, 2001 — Apple drops the iPod, turning music🎶 into a pocket-sized revolution. 1,000 songs in your pocket, paired with iTunes, reshaping how we buy, store, and share tunes. The handheld era begins.
#TBT #iPod #Apple🍏 #MusicTech #TechHistory
Oct 23, 2001 — Apple drops the iPod, turning music🎶 into a pocket-sized revolution. 1,000 songs in your pocket, paired with iTunes, reshaping how we buy, store, and share tunes. The handheld era begins.
#TBT #iPod #Apple🍏 #MusicTech #TechHistory

October 23, 2025 at 4:42 PM
Throwback Thursday:
Oct 23, 2001 — Apple drops the iPod, turning music🎶 into a pocket-sized revolution. 1,000 songs in your pocket, paired with iTunes, reshaping how we buy, store, and share tunes. The handheld era begins.
#TBT #iPod #Apple🍏 #MusicTech #TechHistory
Oct 23, 2001 — Apple drops the iPod, turning music🎶 into a pocket-sized revolution. 1,000 songs in your pocket, paired with iTunes, reshaping how we buy, store, and share tunes. The handheld era begins.
#TBT #iPod #Apple🍏 #MusicTech #TechHistory
Cyber Risk Tip:
Start with a Business Impact Assessment (BIA) to identify mission-critical functions and IT systems. Prioritize risks by potential losses, then run a cost-benefit analysis to justify controls. In cloud, replicate across regions for resilience. #CyberSecurity #BIA #Cloud
Start with a Business Impact Assessment (BIA) to identify mission-critical functions and IT systems. Prioritize risks by potential losses, then run a cost-benefit analysis to justify controls. In cloud, replicate across regions for resilience. #CyberSecurity #BIA #Cloud

October 22, 2025 at 4:32 PM
Cyber Risk Tip:
Start with a Business Impact Assessment (BIA) to identify mission-critical functions and IT systems. Prioritize risks by potential losses, then run a cost-benefit analysis to justify controls. In cloud, replicate across regions for resilience. #CyberSecurity #BIA #Cloud
Start with a Business Impact Assessment (BIA) to identify mission-critical functions and IT systems. Prioritize risks by potential losses, then run a cost-benefit analysis to justify controls. In cloud, replicate across regions for resilience. #CyberSecurity #BIA #Cloud
Reposted by Sudo Truth
Can cyber privateers help beat cybercrime? Time argues for public-private collaboration: real-time threat intel, rapid containment, and cross‑sector resilience. Move from silos to shared defense.
time.com/7317012/can-...
#CyberSecurity #ThreatIntelligence #PublicPrivatePartnership
time.com/7317012/can-...
#CyberSecurity #ThreatIntelligence #PublicPrivatePartnership
time.com
October 21, 2025 at 4:34 PM
Can cyber privateers help beat cybercrime? Time argues for public-private collaboration: real-time threat intel, rapid containment, and cross‑sector resilience. Move from silos to shared defense.
time.com/7317012/can-...
#CyberSecurity #ThreatIntelligence #PublicPrivatePartnership
time.com/7317012/can-...
#CyberSecurity #ThreatIntelligence #PublicPrivatePartnership
Cybersecurity is all about keeping our business running smoothly. But how does your COOP define what’s covered? Which activities, systems, and controls are included? And are you sure your organization can stay up and running even if something goes wrong? #cybersecurity #COOP #businesscontinuity
October 20, 2025 at 3:59 PM
Cybersecurity is all about keeping our business running smoothly. But how does your COOP define what’s covered? Which activities, systems, and controls are included? And are you sure your organization can stay up and running even if something goes wrong? #cybersecurity #COOP #businesscontinuity
#Throwback to October 16, 1959! Control #Data Corp unveiled the CDC 1604—the powerhouse computer designed by Seymour Cray that processed real-time data, powered weapon systems, and solved huge scientific problems. A true tech pioneer!

October 16, 2025 at 8:43 PM
#Throwback to October 16, 1959! Control #Data Corp unveiled the CDC 1604—the powerhouse computer designed by Seymour Cray that processed real-time data, powered weapon systems, and solved huge scientific problems. A true tech pioneer!
Cumulative inaction is costing. Experts warn that government and business inaction on #cybersecurity is finally biting. A laissez-faire cyber strategy could unleash cascades of #economic disruption, affecting #financial services, energy, and transport systems. - BBC
#IndustryInsights
#IndustryInsights

October 15, 2025 at 4:43 PM
Cumulative inaction is costing. Experts warn that government and business inaction on #cybersecurity is finally biting. A laissez-faire cyber strategy could unleash cascades of #economic disruption, affecting #financial services, energy, and transport systems. - BBC
#IndustryInsights
#IndustryInsights
Reposted by Sudo Truth
Microsoft addresses 167 CVEs in its largest #PatchTuesday to date, including three zero-day vulnerabilities, two of which were exploited in the wild. See the #TenableResearch recap: spr.ly/63325AIIMF

October 14, 2025 at 6:53 PM
Microsoft addresses 167 CVEs in its largest #PatchTuesday to date, including three zero-day vulnerabilities, two of which were exploited in the wild. See the #TenableResearch recap: spr.ly/63325AIIMF
#Cybersecurity Tip:
Now is the time to create a security checklist for 2026.
Map out & classify all your #data. Create a #taxonomy of every information type to tailor security controls based on impact and #risk. Regularly review your inventory to ensure no data is left unprotected.
Now is the time to create a security checklist for 2026.
Map out & classify all your #data. Create a #taxonomy of every information type to tailor security controls based on impact and #risk. Regularly review your inventory to ensure no data is left unprotected.

October 14, 2025 at 7:11 PM
#Cybersecurity Tip:
Now is the time to create a security checklist for 2026.
Map out & classify all your #data. Create a #taxonomy of every information type to tailor security controls based on impact and #risk. Regularly review your inventory to ensure no data is left unprotected.
Now is the time to create a security checklist for 2026.
Map out & classify all your #data. Create a #taxonomy of every information type to tailor security controls based on impact and #risk. Regularly review your inventory to ensure no data is left unprotected.
During Cybersecurity Awareness Month, revisit our classic guide, “ #Cybersecurity Fundamentals: A Guide for Non-Technical Leaders,” published a year ago. Its essential tips remain relevant. Empower your leadership in today’s digital landscape!
open.substack.com/pub/sudotrut...
open.substack.com/pub/sudotrut...

October 13, 2025 at 5:12 PM
During Cybersecurity Awareness Month, revisit our classic guide, “ #Cybersecurity Fundamentals: A Guide for Non-Technical Leaders,” published a year ago. Its essential tips remain relevant. Empower your leadership in today’s digital landscape!
open.substack.com/pub/sudotrut...
open.substack.com/pub/sudotrut...
Given the threat posed by sophisticated cyber actors to water treatment facilities, some dating back to the 1970s that are just now going online, what measures have you taken to safeguard your #critical systems, especially those previously considered immune, from emerging #cyberthreats?
#SCADA
#SCADA
October 13, 2025 at 3:29 PM
Given the threat posed by sophisticated cyber actors to water treatment facilities, some dating back to the 1970s that are just now going online, what measures have you taken to safeguard your #critical systems, especially those previously considered immune, from emerging #cyberthreats?
#SCADA
#SCADA
Reposted by Sudo Truth
Flock is preparing to roll out a new feature: Its gunshot detection devices will begin listening for voices in “distress.” www.eff.org/deeplinks/2...

Flock’s Gunshot Detection Microphones Will Start Listening for Human
Flock Safety, the police technology company most notable for their extensive network of automated license plate readers spread throughout the United States, is rolling out a new and troubling product
www.eff.org
October 9, 2025 at 9:03 PM
Flock is preparing to roll out a new feature: Its gunshot detection devices will begin listening for voices in “distress.” www.eff.org/deeplinks/2...


