
https://detections.ai/user/KQLWizard
www.safebreach.com/blog/ldapnig...

www.safebreach.com/blog/ldapnig...
www.extensiontotal.com/cyberhaven-i...

www.extensiontotal.com/cyberhaven-i...


www.trendmicro.com/en_us/resear...

www.trendmicro.com/en_us/resear...
Proofpoint highlights a social engineering tactic where users are tricked into running malicious PowerShell scripts, leading to malware infections. Despite needing user interaction, the attack's success relies on clever social engineering.

Proofpoint highlights a social engineering tactic where users are tricked into running malicious PowerShell scripts, leading to malware infections. Despite needing user interaction, the attack's success relies on clever social engineering.
cybersecuritynews.com/red-team-too...
cybersecuritynews.com/red-team-too...

A collection of the most sought-after KQL spells for Microsoft Sentinel and DefenderXDR
www.linkedin.com/pulse/slims-...

A collection of the most sought-after KQL spells for Microsoft Sentinel and DefenderXDR
www.linkedin.com/pulse/slims-...
A highly accurate DefenderXDR exposure management detection for URL File NTLM Hash Disclosure Vulnerability (0day) www.bleepingcomputer.com/news/securit...

A highly accurate DefenderXDR exposure management detection for URL File NTLM Hash Disclosure Vulnerability (0day) www.bleepingcomputer.com/news/securit...


www.trustwave.com/en-us/resour...

www.trustwave.com/en-us/resour...
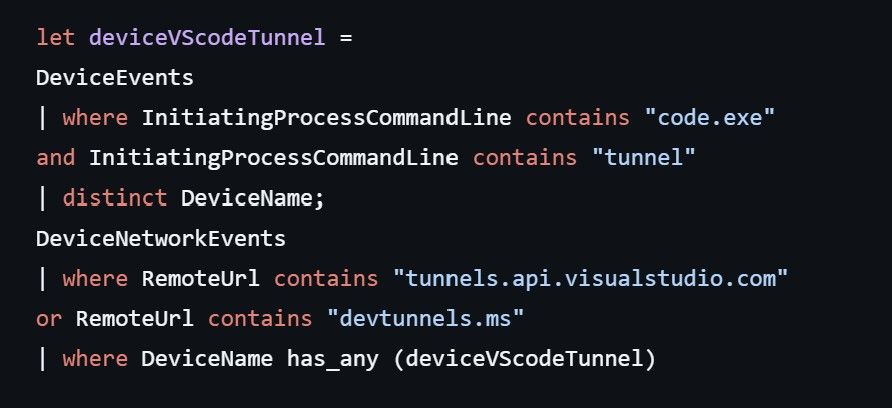
Kevin Beaumont shared insights on helping orgs recover from ransomware attacks. Key tactic: social engineering. Attackers used phone recon to gather contacts, then flooded users with emails & Teams messages. Custom KQL script for early detection:

Kevin Beaumont shared insights on helping orgs recover from ransomware attacks. Key tactic: social engineering. Attackers used phone recon to gather contacts, then flooded users with emails & Teams messages. Custom KQL script for early detection:
Attackers bypass MFA using a phishing framework with Axios HTTP client. Detect compromise in sign-in logs with user agent axios/1.7.7. Proposing auto-detection & isolation for SecOps assessment.
Sources: Asger Deleuran Strunk / Stephan Berger

Attackers bypass MFA using a phishing framework with Axios HTTP client. Detect compromise in sign-in logs with user agent axios/1.7.7. Proposing auto-detection & isolation for SecOps assessment.
Sources: Asger Deleuran Strunk / Stephan Berger
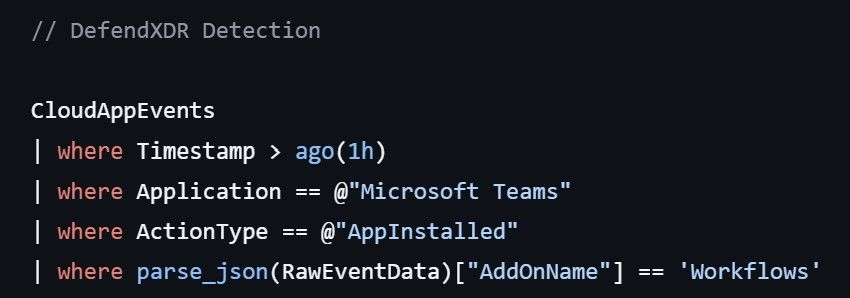
Using CloudApp & Behaviour Analytics to detect malicious threat actor Copilot Agent.
#Cybersecurity #DefenderXDR #CloudApp #CopilotAgent #KQL

Using CloudApp & Behaviour Analytics to detect malicious threat actor Copilot Agent.
#Cybersecurity #DefenderXDR #CloudApp #CopilotAgent #KQL
www.linkedin.com/pulse/copilo...

www.linkedin.com/pulse/copilo...
I have crafted a precise KQL using Microsoft Defender for Office 365 and Endpoint to detect such abuse scenarios.
perception-point.io/blog/phishin...
#Cybersecurity #KQL #Phishing #Evasion #TrustedPlatform

I have crafted a precise KQL using Microsoft Defender for Office 365 and Endpoint to detect such abuse scenarios.
perception-point.io/blog/phishin...
#Cybersecurity #KQL #Phishing #Evasion #TrustedPlatform
👉 Add yourself and anyone you know today 👈
🫂 All are welcome.
This is my v1, I'll add options to directly follow from the site itself but first 👇
LET'S FILL IT UP! 🙏

👉 Add yourself and anyone you know today 👈
🫂 All are welcome.
This is my v1, I'll add options to directly follow from the site itself but first 👇
LET'S FILL IT UP! 🙏


#ilightsingapore #singapore

#ilightsingapore #singapore



