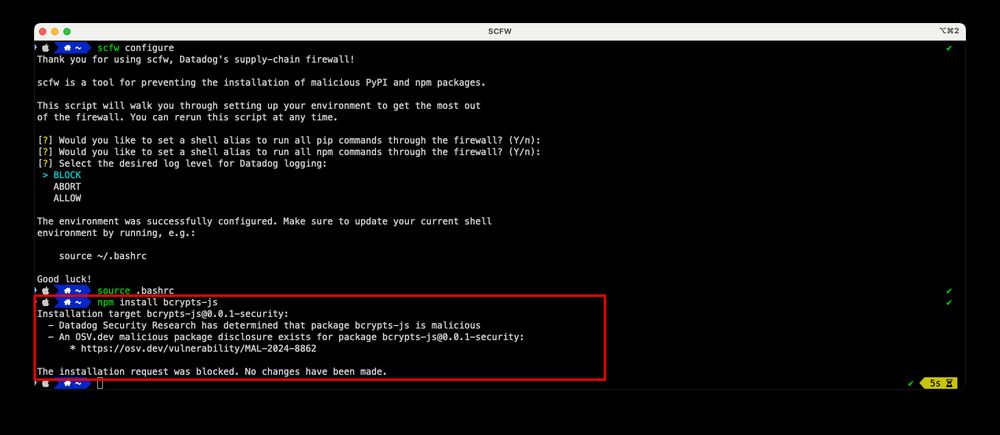
Subscribe to our monthly newsletter: https://securitylabs.datadoghq.com/newsletters/

fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
fwdcloudsec.org/conference/n...
@sethsec.bsky.social
@siigil.bsky.social
@gregfoss.com
github.com/DataDog/mali...
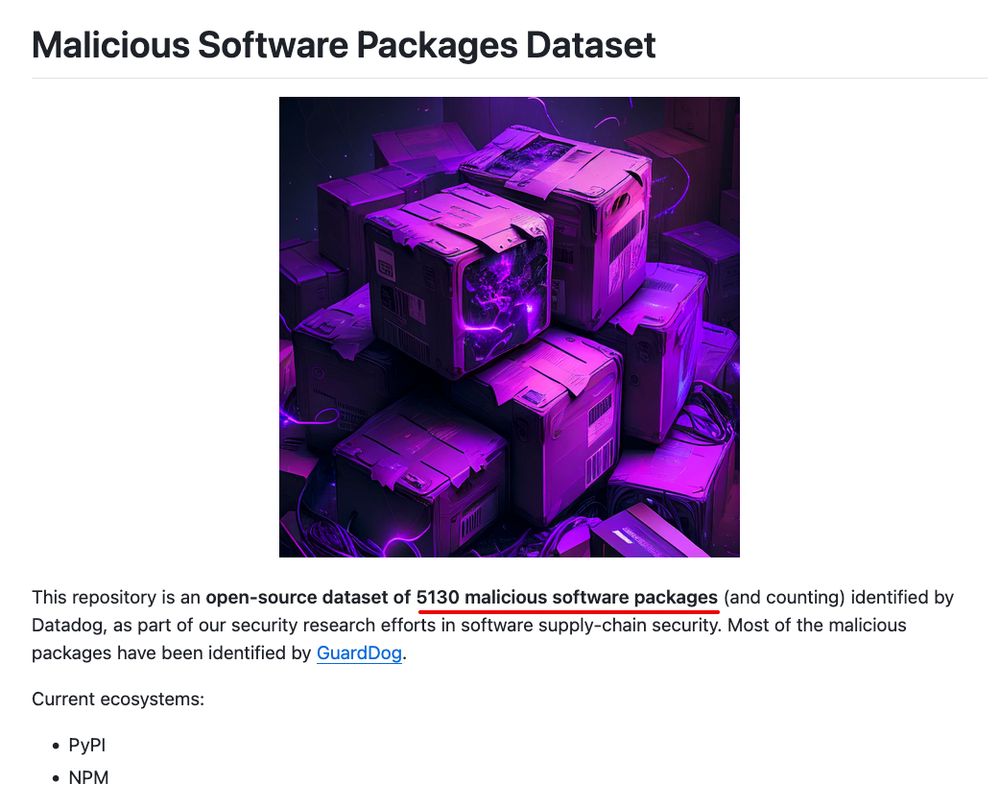
github.com/DataDog/mali...
Don't miss our February edition going live tomorrow!
securitylabs.datadoghq.com/newsletters/...

Don't miss our February edition going live tomorrow!
securitylabs.datadoghq.com/newsletters/...
github.com/DataDog/whoA...
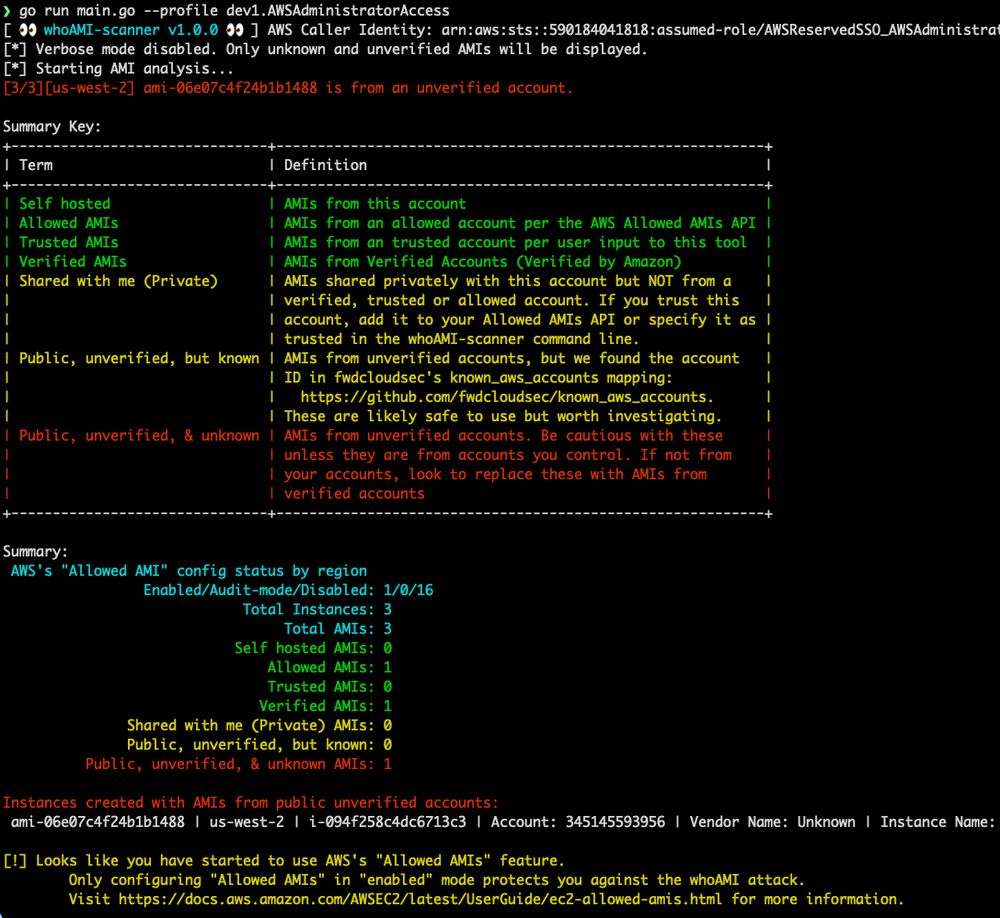
github.com/DataDog/whoA...
securitylabs.datadoghq.com/articles/tal...
This post describes an attacker that we've observed in the wild, including a malicious AWS account ID used to create a backdoor IAM role.
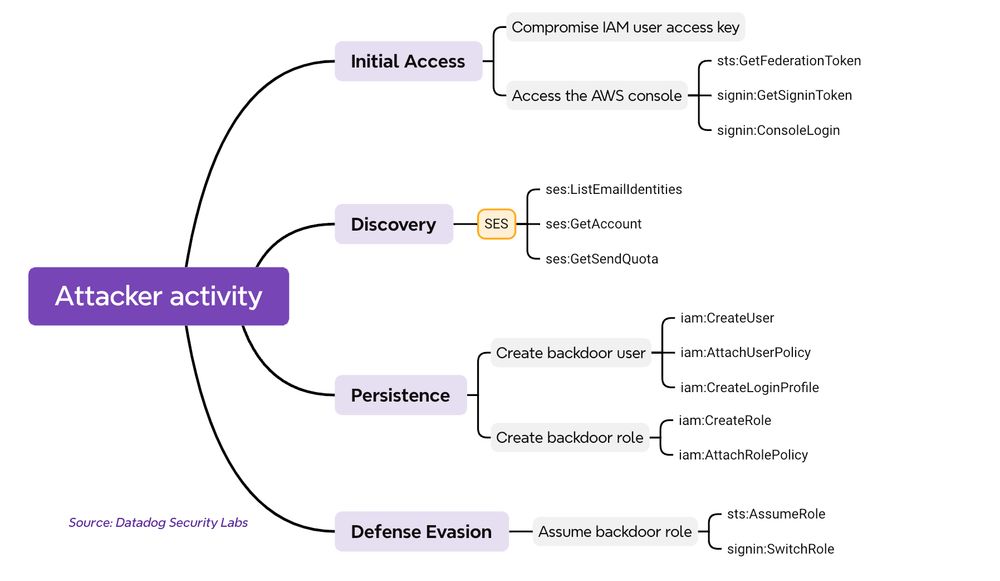
securitylabs.datadoghq.com/articles/tal...
This post describes an attacker that we've observed in the wild, including a malicious AWS account ID used to create a backdoor IAM role.