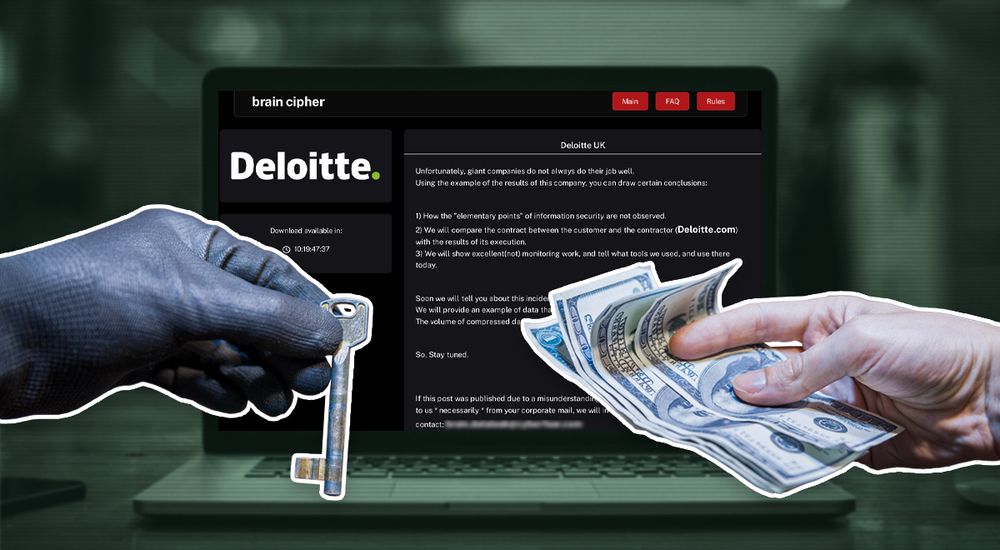
www.bleepingcomputer.com/news/securit...
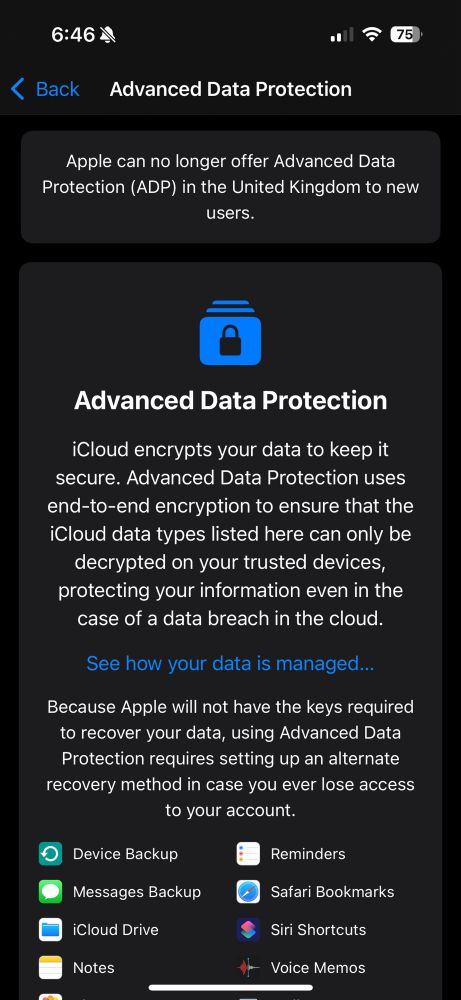
www.bleepingcomputer.com/news/securit...
InvisibleFerret exhibits a range of capabilities aimed at exfiltrating sensitive data. It actively searches for source code, cryptocurrency wallets, user credentials, and important files by targeting browser data, clipboard contents, and system directories
#anyrun
#malware
#analysis

Malware trends are shifting, and businesses are in the crosshairs. Discover how stealers are dominating the threat landscape and what it means for your organization.
www.linkedin.com/pulse/steale...

Malware trends are shifting, and businesses are in the crosshairs. Discover how stealers are dominating the threat landscape and what it means for your organization.
www.linkedin.com/pulse/steale...
www.bleepingcomputer.com/news/securit...

www.bleepingcomputer.com/news/securit...