
🔗 Advisory: certvde.com/en/advisorie... @ruheabteil.ch
🔗 Mole: github.com/cyber-defenc...
More vulnerabilities have been reported - stay tuned for upcoming advisories.

🔗 Advisory: certvde.com/en/advisorie... @ruheabteil.ch
🔗 Mole: github.com/cyber-defenc...
More vulnerabilities have been reported - stay tuned for upcoming advisories.
socket.dev/blog/securit...

socket.dev/blog/securit...






github.com/olafhartong/...
Slides available here:
github.com/olafhartong/...
github.com/olafhartong/...
Slides available here:
github.com/olafhartong/...
allocation, no alignment
don't give a fuck if it faults on assignment
this is fatal abort()
allocation, no alignment
don't give a fuck if it faults on assignment
this is fatal abort()
They graded it.
Bwahahaha.


They graded it.
Bwahahaha.
It's a nasty new technique: puts target thread into ⓪ deadloop, for as long as you can afford. Requires THREAD_GET_CONTEXT right.
The gist? Just spam NtGetContextThread(tgt).😸
Target will be jailed, running nt!PspGetSetContextSpecialApc 🔁.
Src & binary in [ALT].
Usecases: ⤵️
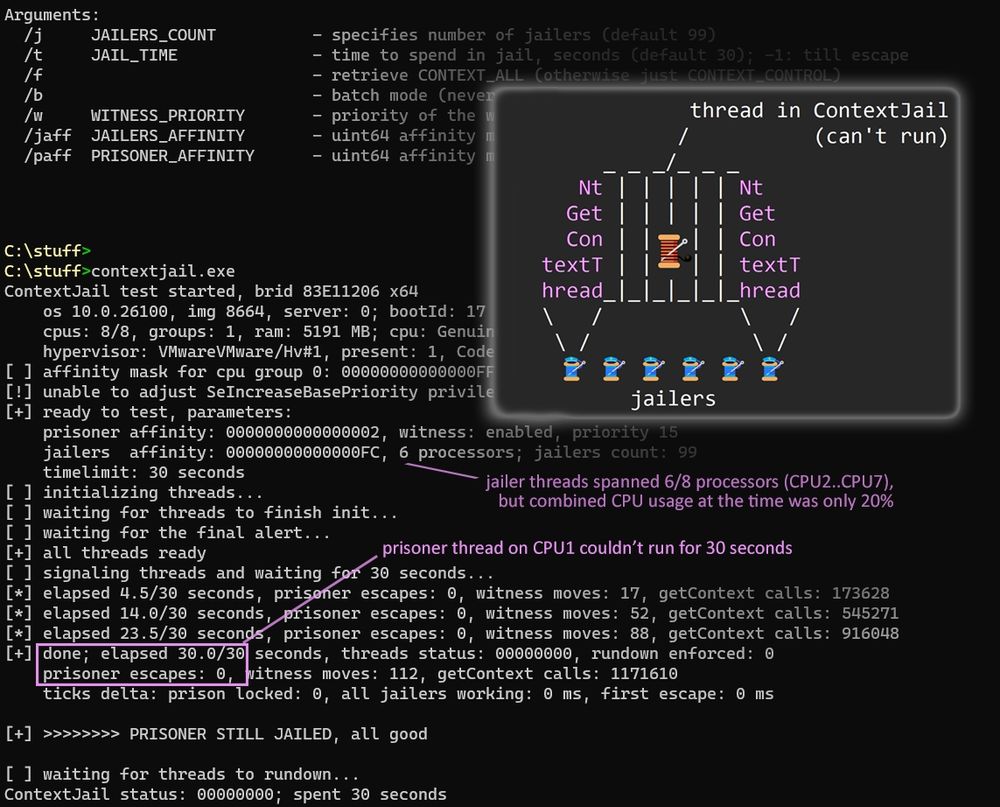
It's a nasty new technique: puts target thread into ⓪ deadloop, for as long as you can afford. Requires THREAD_GET_CONTEXT right.
The gist? Just spam NtGetContextThread(tgt).😸
Target will be jailed, running nt!PspGetSetContextSpecialApc 🔁.
Src & binary in [ALT].
Usecases: ⤵️
aff-wg.org/2025/04/10/p...
A walk-through of some history on post-ex eco-systems used by CS (PowerShell, Reflective DLLs, .NET, and BOFs).
Ends with a coffee conversation talking about magician's guilds, security research, and ideas about what's next.
aff-wg.org/2025/04/10/p...
A walk-through of some history on post-ex eco-systems used by CS (PowerShell, Reflective DLLs, .NET, and BOFs).
Ends with a coffee conversation talking about magician's guilds, security research, and ideas about what's next.
It runs Doom on OS from 1993 until today, and Chrome-based PDF viewers!
You can make it an HTML/JS polyglot too to run on most browsers! (3/3)

It runs Doom on OS from 1993 until today, and Chrome-based PDF viewers!
You can make it an HTML/JS polyglot too to run on most browsers! (3/3)


My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...

My research, comprising ~70 Windows executables, found that all of them were vulnerable to this, to varying degrees.
Here’s what I found and why it matters 👉 wietze.github.io/blog/bypassi...
I had a series in mind like "Rubeus' Hidden Secrets" or something like that. Basically, highlighting features of the tool that seem less well known. I'm starting off with a basic one for getting crackable hashes from cached service tickets.
rastamouse.me/kerberoastin...

I had a series in mind like "Rubeus' Hidden Secrets" or something like that. Basically, highlighting features of the tool that seem less well known. I'm starting off with a basic one for getting crackable hashes from cached service tickets.
rastamouse.me/kerberoastin...
Slides are here:
docs.google.com/presentation...

Slides are here:
docs.google.com/presentation...
Original->





