- SecurityAudit got an update 🥳 mostly S3 tables
- network-firewall getting flow operations
- route53-recovery-control-config (???) getting resource policies
I'm still not sure why every week there seem to be version updates to some policies, but without actual changes?!

- SecurityAudit got an update 🥳 mostly S3 tables
- network-firewall getting flow operations
- route53-recovery-control-config (???) getting resource policies
I'm still not sure why every week there seem to be version updates to some policies, but without actual changes?!
GenAI remains a key part of my daily workflow, but it feels like I'm running in to more limitations - anyone else?
In this case, the LLM kept trying the same thing, even though it detected there was a problem with it (very neat!)

GenAI remains a key part of my daily workflow, but it feels like I'm running in to more limitations - anyone else?
In this case, the LLM kept trying the same thing, even though it detected there was a problem with it (very neat!)
Speaking at meetups and conferences has given me such a high ROI for the effort, and it gets easier the more you do it!

Speaking at meetups and conferences has given me such a high ROI for the effort, and it gets easier the more you do it!
- deeplens gone 🔪🤖
- cleanrooms gets protected (?) jobs
- connect gets data lake integration
15 separate updates detected this week, which is more than usual, but not to show for it...

- deeplens gone 🔪🤖
- cleanrooms gets protected (?) jobs
- connect gets data lake integration
15 separate updates detected this week, which is more than usual, but not to show for it...
Each one of these is its own AWS CloudFormation stack, with its own deployment, tests, etc
The complexity of SaaS is 🤯 no wonder it took me so long... and it's not finished yet!

Each one of these is its own AWS CloudFormation stack, with its own deployment, tests, etc
The complexity of SaaS is 🤯 no wonder it took me so long... and it's not finished yet!
- Bedrock gets prompt routing
- Support will allow starting and getting interactions
- Batch will get consumable resources (?)
- Can't set challenge questions for your account anymore
It's not often you see IAM actions removed, but it can happen!

- Bedrock gets prompt routing
- Support will allow starting and getting interactions
- Batch will get consumable resources (?)
- Can't set challenge questions for your account anymore
It's not often you see IAM actions removed, but it can happen!
It's on August 15 in Brisbane.
A bunch of sponsorship packages have already been sold, so if you want to get the best price reach out ASAP!
awscommunitydayaus.com/

It's on August 15 in Brisbane.
A bunch of sponsorship packages have already been sold, so if you want to get the best price reach out ASAP!
awscommunitydayaus.com/

Using the array index notion on what would *eventually* be an array was instead trying to access the Promise object... and failing silently 🤦♂️
It didn't pick it up until I asked very specifically about this logic, but the answer was spot on

Using the array index notion on what would *eventually* be an array was instead trying to access the Promise object... and failing silently 🤦♂️
It didn't pick it up until I asked very specifically about this logic, but the answer was spot on
- New iotmanagedintegrations action namespace
- New gameliftstreams action namespace
- CloudWatch RUM getting resource policies soon
- AWSFaultInjectionSimulatorECSAccess new version, but only the CreateDate changed? 🤨

- New iotmanagedintegrations action namespace
- New gameliftstreams action namespace
- CloudWatch RUM getting resource policies soon
- AWSFaultInjectionSimulatorECSAccess new version, but only the CreateDate changed? 🤨
Eventually I'll have time to go through the docs in detail 😆

Eventually I'll have time to go through the docs in detail 😆
This thread made me realise I was lucky - I learnt AWS when there were only a few services (not even IAM!)
I guess there's got to be *some* upside to getting old 👴

This thread made me realise I was lucky - I learnt AWS when there were only a few services (not even IAM!)
I guess there's got to be *some* upside to getting old 👴
Unfortunately I used the same interval for both checks, so a report would be PENDING up until the interval, then it would be marked FAILED.
Super.
Efficient.
Fail.
#buildinpublic

Unfortunately I used the same interval for both checks, so a report would be PENDING up until the interval, then it would be marked FAILED.
Super.
Efficient.
Fail.
#buildinpublic
Let me know if that's interesting to you, or tag someone who might be!

Let me know if that's interesting to you, or tag someone who might be!
I made an AWS IAM permissions error in my Lambda function that broke signups.
If I can still get it wrong after writing awsiamguide.com, then anyone can...

I made an AWS IAM permissions error in my Lambda function that broke signups.
If I can still get it wrong after writing awsiamguide.com, then anyone can...


It's free to connect your account and do a daily scan of publicly accessible AWS resources. There's half a dozen of the most common resources, with more to follow soon!
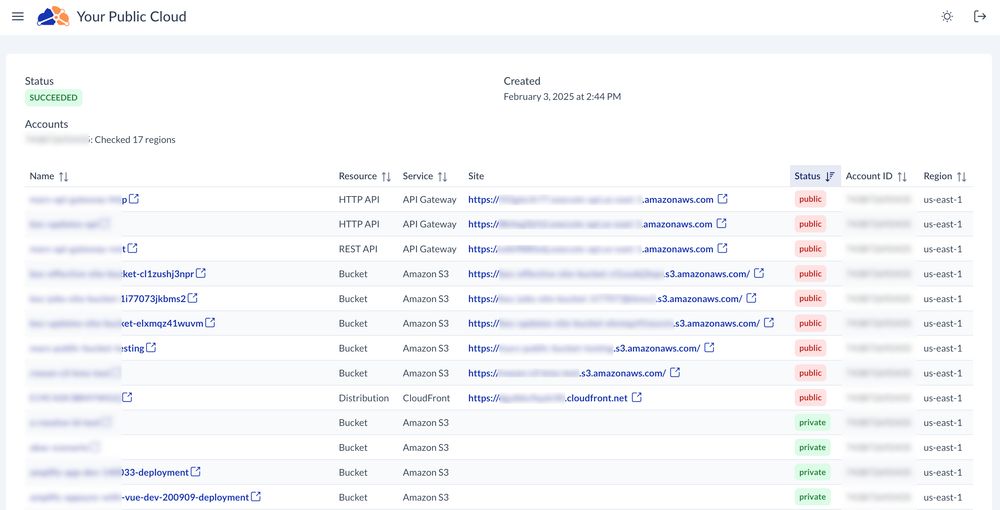
It's free to connect your account and do a daily scan of publicly accessible AWS resources. There's half a dozen of the most common resources, with more to follow soon!
While I appreciate the notice, it's IAM that's forcing me to use "*" when using conditions key eg. aws:PrincipalOrgID
I wish there was a better/limited way to specify a principal in my org #awswishlist

While I appreciate the notice, it's IAM that's forcing me to use "*" when using conditions key eg. aws:PrincipalOrgID
I wish there was a better/limited way to specify a principal in my org #awswishlist

That could be very useful... 🎩

That could be very useful... 🎩

This one about serverless API choices is a big one, and definitely worth being aware of blog.theserverlessterminal.com/serverless-a... It's really nice to have it all in one table.

This one about serverless API choices is a big one, and definitely worth being aware of blog.theserverlessterminal.com/serverless-a... It's really nice to have it all in one table.
I mean, CloudFront's always been good to me, but it's just ONE of many things AWS does, so I wasn't expecting them to beat out others...

I mean, CloudFront's always been good to me, but it's just ONE of many things AWS does, so I wasn't expecting them to beat out others...

