

"Widgets Gone Wild: Exploiting XSS Through Flawed postMessage Checks"

"Widgets Gone Wild: Exploiting XSS Through Flawed postMessage Checks"

www.amazon.nl/-/en/Simone-...
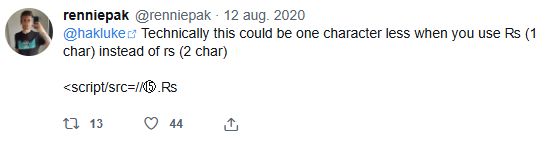
Since I deleted my account, this is the tweet:
www.amazon.nl/-/en/Simone-...
Since I deleted my account, this is the tweet:

Company with a annual revenue of 25 BILLION USD reduces my bounty by $5 because I didn't supply my IP address.
For a postMessage XSS, so the only thing showing up in their logs would be me opening the homepage...

Company with a annual revenue of 25 BILLION USD reduces my bounty by $5 because I didn't supply my IP address.
For a postMessage XSS, so the only thing showing up in their logs would be me opening the homepage...


I case you missed it:
I've created cspbypass.com
A site where you can search for known CSP bypass gadgets to gain XSS.
It already contains a bunch of useful gadgets with contributions from your favourite hackers.
If you have some CSP bypasses to share, feel free to contribute!
I case you missed it:
I've created cspbypass.com
A site where you can search for known CSP bypass gadgets to gain XSS.
It already contains a bunch of useful gadgets with contributions from your favourite hackers.
If you have some CSP bypasses to share, feel free to contribute!
You can find it here, if you want to try it out:
https://0-a.nl/jsendpoints.txt
#bugbountytips

You can find it here, if you want to try it out:
https://0-a.nl/jsendpoints.txt
#bugbountytips




