A Go library to create BloodHound OpenGraphs easily
github.com/TheManticore... by @podalirius.bsky.social

A Go library to create BloodHound OpenGraphs easily
github.com/TheManticore... by @podalirius.bsky.social
Meet ShareHound, an OpenGraph collector for BloodHound CE & Enterprise that reveals share-level attack paths at scale.
@podalirius.bsky.social unpacks all the details in our latest blog post. ghst.ly/4ogiBqt

Meet ShareHound, an OpenGraph collector for BloodHound CE & Enterprise that reveals share-level attack paths at scale.
@podalirius.bsky.social unpacks all the details in our latest blog post. ghst.ly/4ogiBqt
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
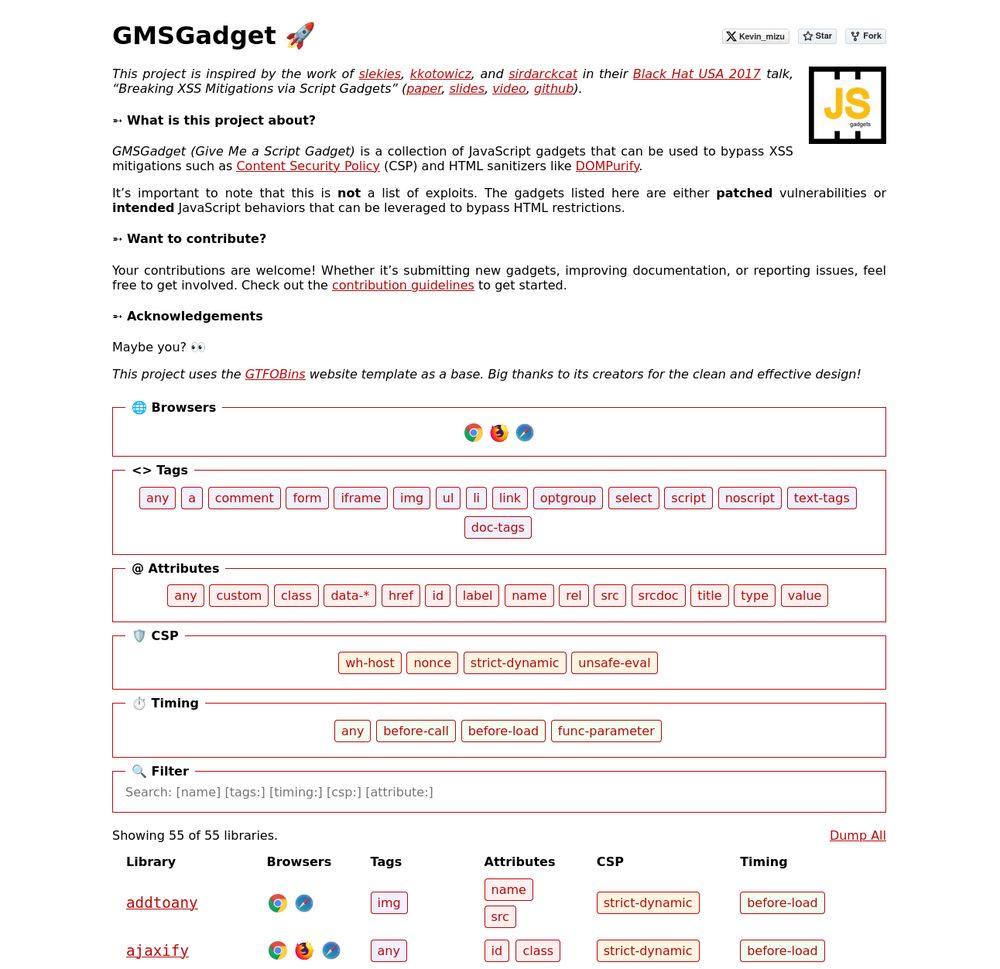
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
This tool allows you to create precise wordlists for finding passwords of users in an Active Directory domain using its LDAP data.
➡️ github.com/TheManticore...

This tool allows you to create precise wordlists for finding passwords of users in an Active Directory domain using its LDAP data.
➡️ github.com/TheManticore...
A cross-platform tool to find & decrypt Group Policy Preferences passwords from SYSVOL with low-privileged domain accounts!
🔗 Check it out on GitHub: github.com/p0dalirius/F...

A cross-platform tool to find & decrypt Group Policy Preferences passwords from SYSVOL with low-privileged domain accounts!
🔗 Check it out on GitHub: github.com/p0dalirius/F...
Analyzing Windows NT Security Descriptors can be a headache. I built DescribeNTSecurityDescriptor, a cross-platform tool to decode, parse & visualize them easily!
🔗 GitHub: github.com/p0dalirius/DescribeNTSecurityDescriptor

Analyzing Windows NT Security Descriptors can be a headache. I built DescribeNTSecurityDescriptor, a cross-platform tool to decode, parse & visualize them easily!
🔗 GitHub: github.com/p0dalirius/DescribeNTSecurityDescriptor

Dump #Entra access tokens from Windows Token Broker Cache, and make your way to Entra 🚀
Thanks @xpnsec.com for the technique! More info on his blog : blog.xpnsec.com/wam-bam/

Dump #Entra access tokens from Windows Token Broker Cache, and make your way to Entra 🚀
Thanks @xpnsec.com for the technique! More info on his blog : blog.xpnsec.com/wam-bam/
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...

I reverse engineered the kernel extension and the secure enclave processor, where this feature is implemented.
naehrdine.blogspot.com/2024/11/reve...
And I'll explain below how it works 🛠️🧵⬇️
And I'll explain below how it works 🛠️🧵⬇️
github.com/p0dalirius/L...
#infosec #pentest #redteam

github.com/p0dalirius/L...
#infosec #pentest #redteam
Article Highlight #1 - check it out in Paged Out #3 page 53
pagedout.institute/download/Pag...

Article Highlight #1 - check it out in Paged Out #3 page 53
pagedout.institute/download/Pag...

Check it out ⤵️
podalirius.net/en/articles/...
Check it out ⤵️
podalirius.net/en/articles/...
➡️ github.com/p0dalirius/L...
Happy password cracking!
➡️ github.com/p0dalirius/L...
Happy password cracking!
➡️ github.com/p0dalirius/L...
The generated wordlist cracked way more passwords than rockyou2021 on my latest client.
➡️ github.com/p0dalirius/L...
The generated wordlist cracked way more passwords than rockyou2021 on my latest client.
You can backup your BitLocker recovery keys in CSV or JSON.
➡️ github.com/p0dalirius/E...

You can backup your BitLocker recovery keys in CSV or JSON.
➡️ github.com/p0dalirius/E...
This is really useful in post-exploitation or system administration (to backup keys for example). Export in XLSX, SQLITE, JSON
github.com/p0dalirius/E...
Here is an example:

This is really useful in post-exploitation or system administration (to backup keys for example). Export in XLSX, SQLITE, JSON
github.com/p0dalirius/E...
Here is an example: