
www.cybersecuritydive.com/news/cisa-hi...

www.cybersecuritydive.com/news/cisa-hi...


OpenAI's latest threat report found a similar phenomenon: cyberscoop.com/openai-threa...

OpenAI's latest threat report found a similar phenomenon: cyberscoop.com/openai-threa...

The Edge: What is the Role of Provable Randomness in Cybersecurity? https://zpr.io/WUMUznmTz4zs #DRTheEdge #darkreading #cybersecurity

The Edge: What is the Role of Provable Randomness in Cybersecurity? https://zpr.io/WUMUznmTz4zs #DRTheEdge #darkreading #cybersecurity

Exits are fueling worries about CISA's capabilities.
www.cybersecuritydive.com/news/cisa-se...
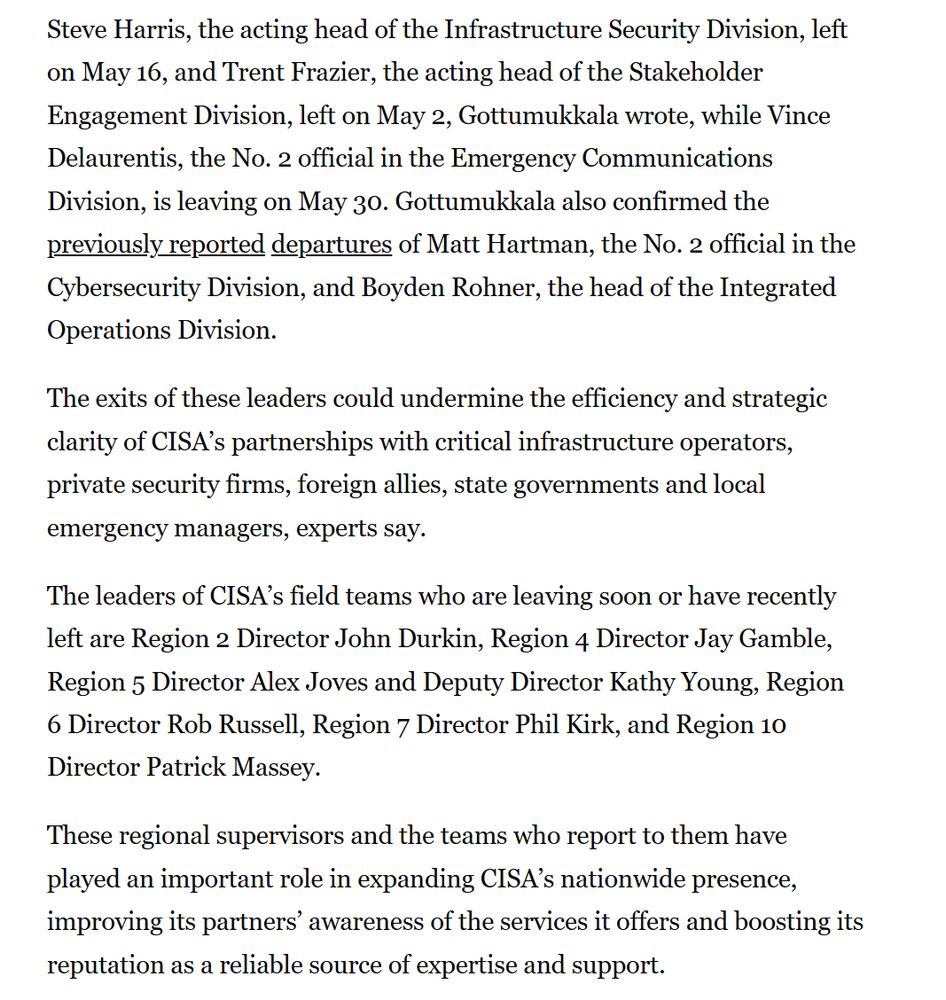
Exits are fueling worries about CISA's capabilities.
www.cybersecuritydive.com/news/cisa-se...
www.techtarget.com/searchsecuri...

www.techtarget.com/searchsecuri...



