
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
github.com/CravateRouge...
github.com/CravateRouge...
sensepost.com/blog/2025/in...
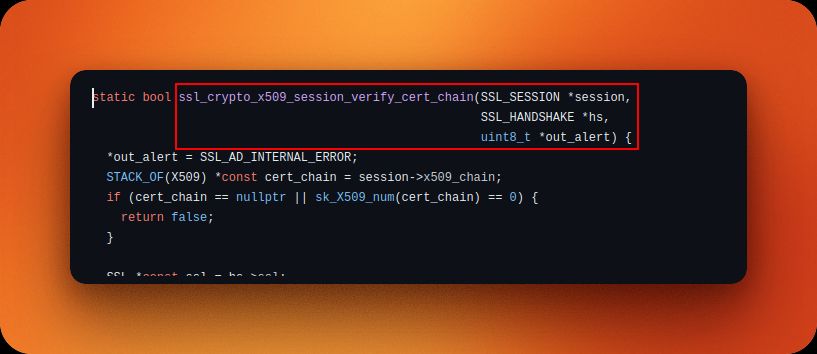
sensepost.com/blog/2025/in...
writeup: sensepost.com/blog/2025/is...
PR to impacket:
github.com/fortra/impac...
Demo: youtu.be/3mG2Ouu3Umk
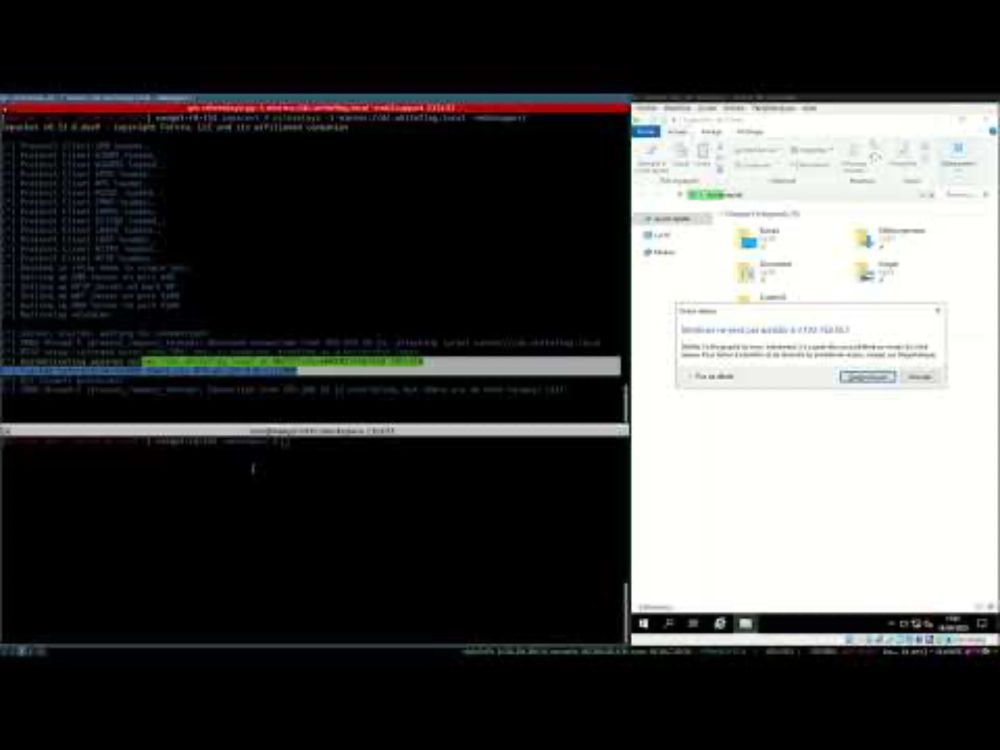
writeup: sensepost.com/blog/2025/is...
PR to impacket:
github.com/fortra/impac...
Demo: youtu.be/3mG2Ouu3Umk
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

