"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
🎥 All presentations from SO-CON 2025 are now live at ghst.ly/socon25-talks.
💻 Slides for each talk are available at ghst.ly/socon25-slides.
🎥 All presentations from SO-CON 2025 are now live at ghst.ly/socon25-talks.
💻 Slides for each talk are available at ghst.ly/socon25-slides.
That tiny difference? It can turn a "non-exploitable" XSS into a real one.
Abuse boundary handling, bypass filters, and make your payload land.
thespanner.co.uk/making-the-u...

That tiny difference? It can turn a "non-exploitable" XSS into a real one.
Abuse boundary handling, bypass filters, and make your payload land.
thespanner.co.uk/making-the-u...
www.synacktiv.com/publications...

www.synacktiv.com/publications...
👉 blog.scrt.ch/2025/02/18/r...
👉 blog.scrt.ch/2025/02/18/r...

blog.thc.org/practical-ht...
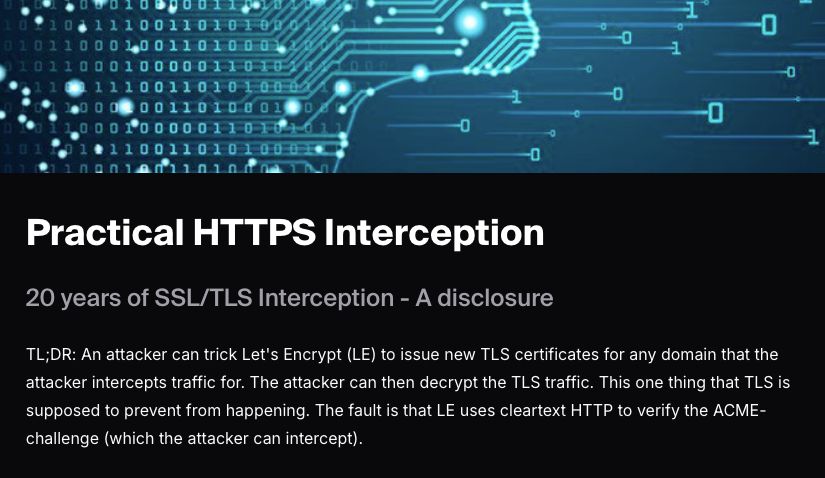
blog.thc.org/practical-ht...
github.com/monasticacad...

github.com/monasticacad...

"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...

"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...

