
Recently, I've released a #KQL function integrating #ExposureManagement and #EntraOps data to identify sensitive callers, actions, and targets. Updated to support parameters like IP Address and Token Identifier.
🔗 github.com/Cloud-Archit...
Recently, I've released a #KQL function integrating #ExposureManagement and #EntraOps data to identify sensitive callers, actions, and targets. Updated to support parameters like IP Address and Token Identifier.
🔗 github.com/Cloud-Archit...
Want to reuse existing queries or unify detection logic across both tables? I’ve published a #KQL function that normalizes the schema of GraphApiAuditEvents to match that of MicrosoftGraphActivityLogs.
🔗 github.com/Cloud-Archit...
Want to reuse existing queries or unify detection logic across both tables? I’ve published a #KQL function that normalizes the schema of GraphApiAuditEvents to match that of MicrosoftGraphActivityLogs.
🔗 github.com/Cloud-Archit...
What are the differences between GraphApiAuditEvents (XDR) and MicrosoftGraphActivityLogs (Diagnostic Logs in hashtag#MicrosoftSentinel)? I’ve built a comparison table outlining the differences in column availability and detail levels.
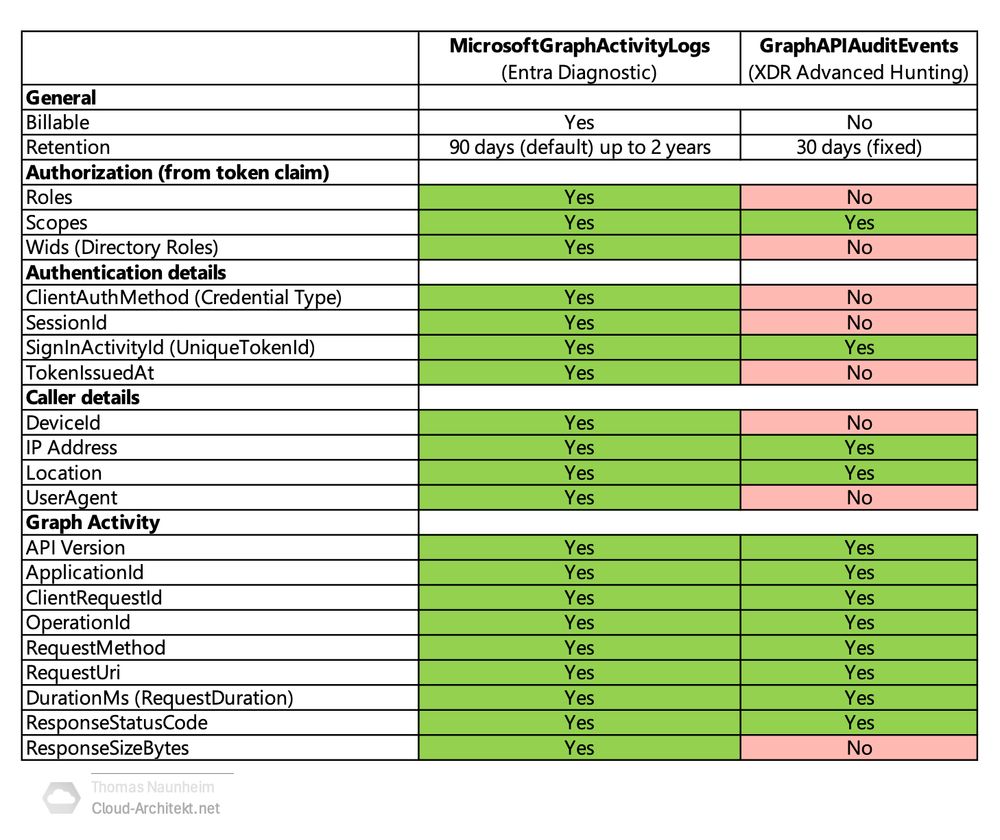
What are the differences between GraphApiAuditEvents (XDR) and MicrosoftGraphActivityLogs (Diagnostic Logs in hashtag#MicrosoftSentinel)? I’ve built a comparison table outlining the differences in column availability and detail levels.
The modified object is classified as critical (based on Exposure Management Critical Assets), and the applied rule details are displayed. In this case, the service principal has been assigned critical app permissions in Exchange Online.
The modified object is classified as critical (based on Exposure Management Critical Assets), and the applied rule details are displayed. In this case, the service principal has been assigned critical app permissions in Exchange Online.
The Graph request includes a POST to the servicePrincipal endpoint, which is flagged as a sensitive modification. This logic is experimental and simplified, so it may result in inaccurate classification and should be used in combo with others indicators.
The Graph request includes a POST to the servicePrincipal endpoint, which is flagged as a sensitive modification. This logic is experimental and simplified, so it may result in inaccurate classification and should be used in combo with others indicators.
However, the scope includes Application.ReadWrite.All, which has been identified as "Control Plane" by using EntraOps classification model.
However, the scope includes Application.ReadWrite.All, which has been identified as "Control Plane" by using EntraOps classification model.
1. IsSensitiveCaller 🗣️
A regular enterprise user (based on Exposure Management Critical Asset information) is calling Graph.
1. IsSensitiveCaller 🗣️
A regular enterprise user (based on Exposure Management Critical Asset information) is calling Graph.
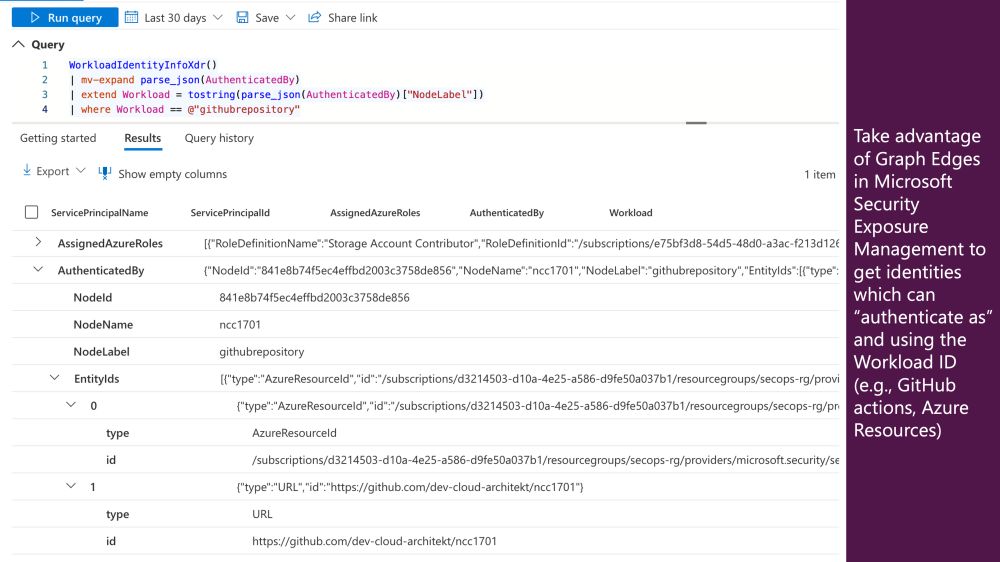
🔗 The query is available here:
github.com/Cloud-Archit...
🔗 The query is available here:
github.com/Cloud-Archit...
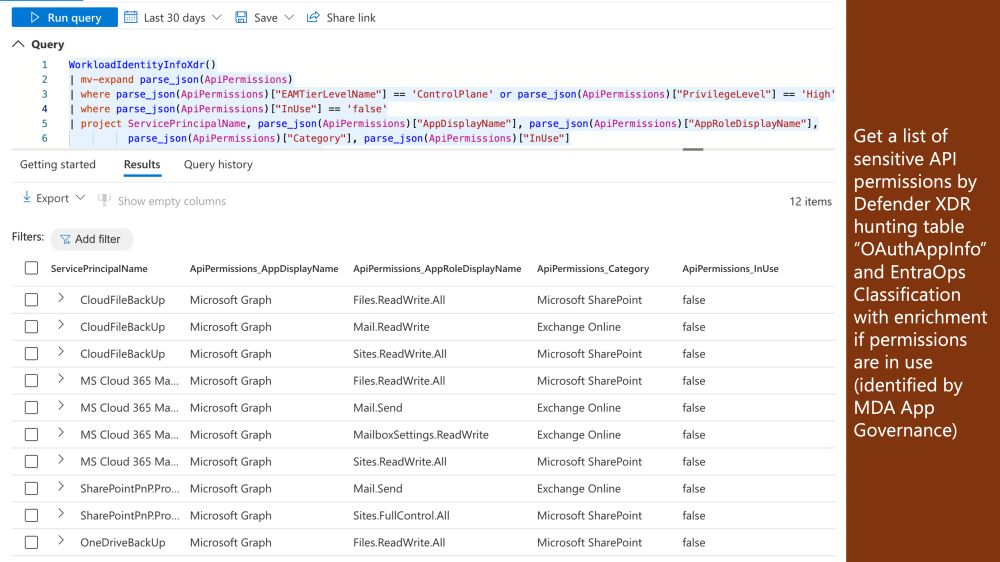
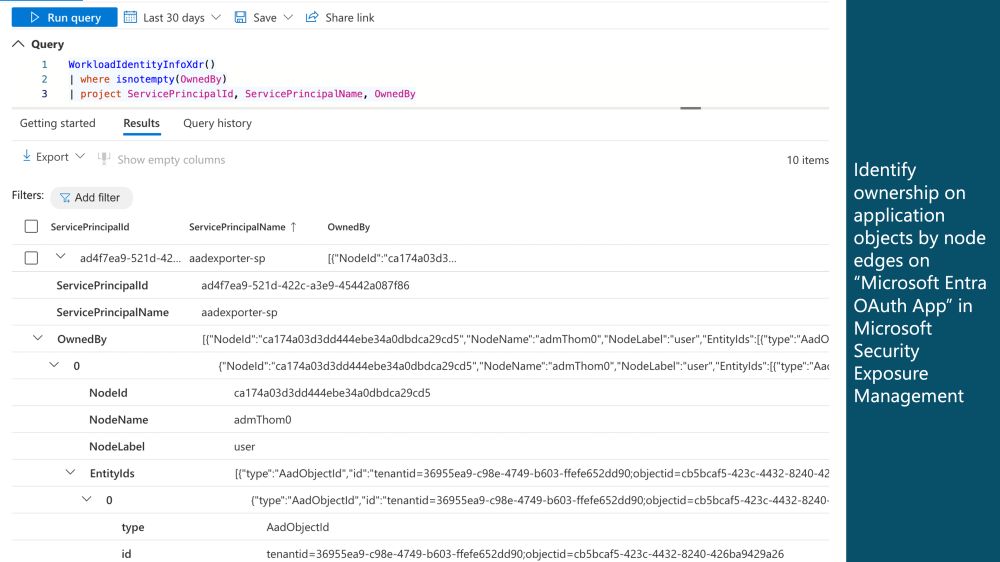
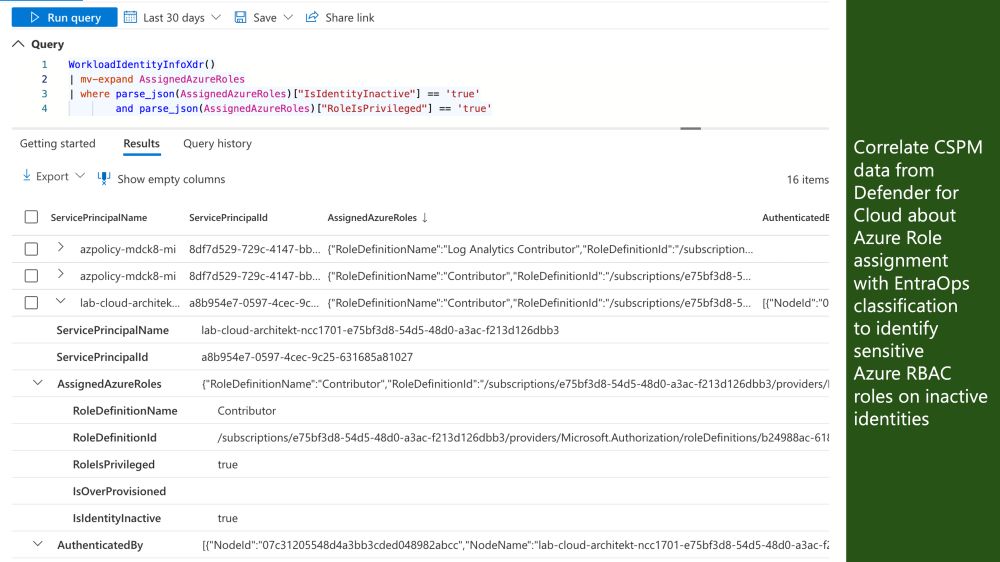

- 🕓 Determine which eligible or active roles were assigned at a specific time, and compare them to their current status
- 🕓 Determine which eligible or active roles were assigned at a specific time, and compare them to their current status
-⚡️ Identifying assigned roles that include specific actions (e.g., reading BitLocker keys).
- 🦸♂️ Listing all eligible assignments for Control Plane (Tier0) roles, including Microsoft role categories and assignment types (direct or indirect).
-⚡️ Identifying assigned roles that include specific actions (e.g., reading BitLocker keys).
- 🦸♂️ Listing all eligible assignments for Control Plane (Tier0) roles, including Microsoft role categories and assignment types (direct or indirect).

learn.microsoft.com/en-us/azure/...

learn.microsoft.com/en-us/azure/...

