
Forget ads, trackers, and shady link - Pi-Hole is your network - level shield. And guess what? You don’t need a Raspberry Pi. That old Android in your drawer? It’s about to become your portable Pi-Hole server
www.mobile-hacker.com/2025/11/25/p...

Forget ads, trackers, and shady link - Pi-Hole is your network - level shield. And guess what? You don’t need a Raspberry Pi. That old Android in your drawer? It’s about to become your portable Pi-Hole server
www.mobile-hacker.com/2025/11/25/p...
I dived into anonymized metadata published after a #WhatsApp security issue that exposed 3.5B phone numbers
-Android rules (81%)
-iOS dominates in rich markets
-Monaco = multi-account heaven
-China is niche but enterprise-heavy
www.mobile-hacker.com/2025/11/20/w...

I dived into anonymized metadata published after a #WhatsApp security issue that exposed 3.5B phone numbers
-Android rules (81%)
-iOS dominates in rich markets
-Monaco = multi-account heaven
-China is niche but enterprise-heavy
www.mobile-hacker.com/2025/11/20/w...
This vulnerability allows any application installed on the device to read SMS/MMS without permission, user interaction, or consent.
www.rapid7.com/blog/post/cv...

This vulnerability allows any application installed on the device to read SMS/MMS without permission, user interaction, or consent.
www.rapid7.com/blog/post/cv...
✅As a bonus, example of deobfuscating Crocodilus Malware
www.mobile-hacker.com/2025/07/22/d...
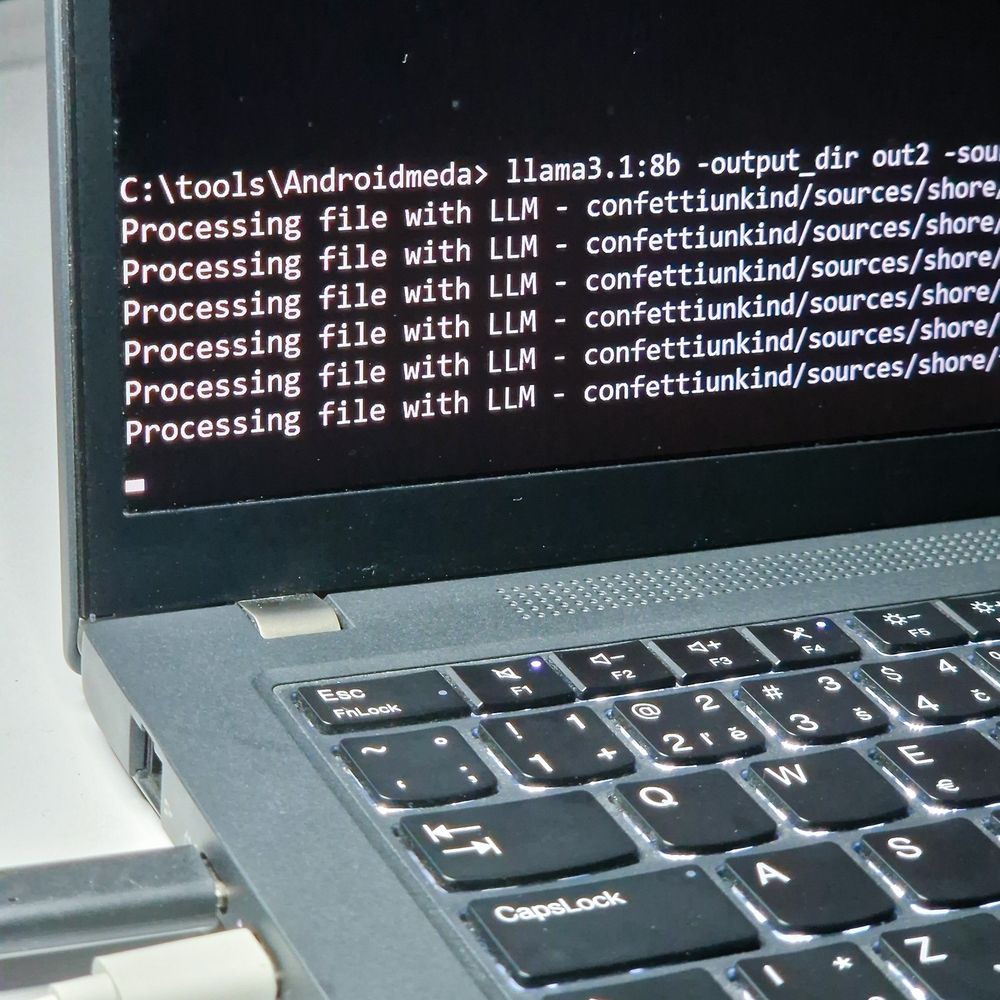
✅As a bonus, example of deobfuscating Crocodilus Malware
www.mobile-hacker.com/2025/07/22/d...
www.mobile-hacker.com/2025/07/21/h...

www.mobile-hacker.com/2025/07/21/h...
www.mobile-hacker.com/2025/07/17/r...
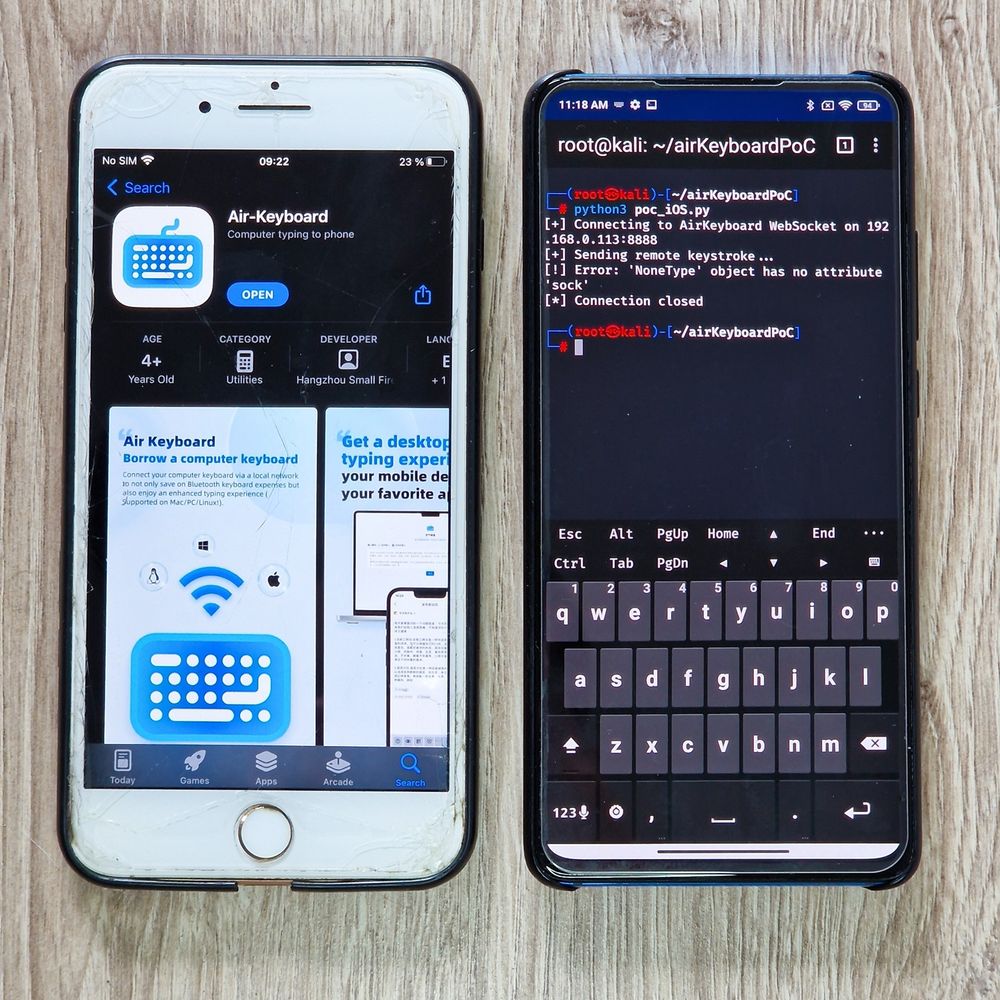
www.mobile-hacker.com/2025/07/17/r...
It is open-source, private, secure messaging app without needing the internet, that relies on Bluetooth mesh network
www.mobile-hacker.com/2025/07/10/o...

It is open-source, private, secure messaging app without needing the internet, that relies on Bluetooth mesh network
www.mobile-hacker.com/2025/07/10/o...
www.mobile-hacker.com/2025/07/09/h...

www.mobile-hacker.com/2025/07/09/h...
www.mobile-hacker.com/2025/07/07/v...

www.mobile-hacker.com/2025/07/07/v...
www.mobile-hacker.com/2025/06/24/i...
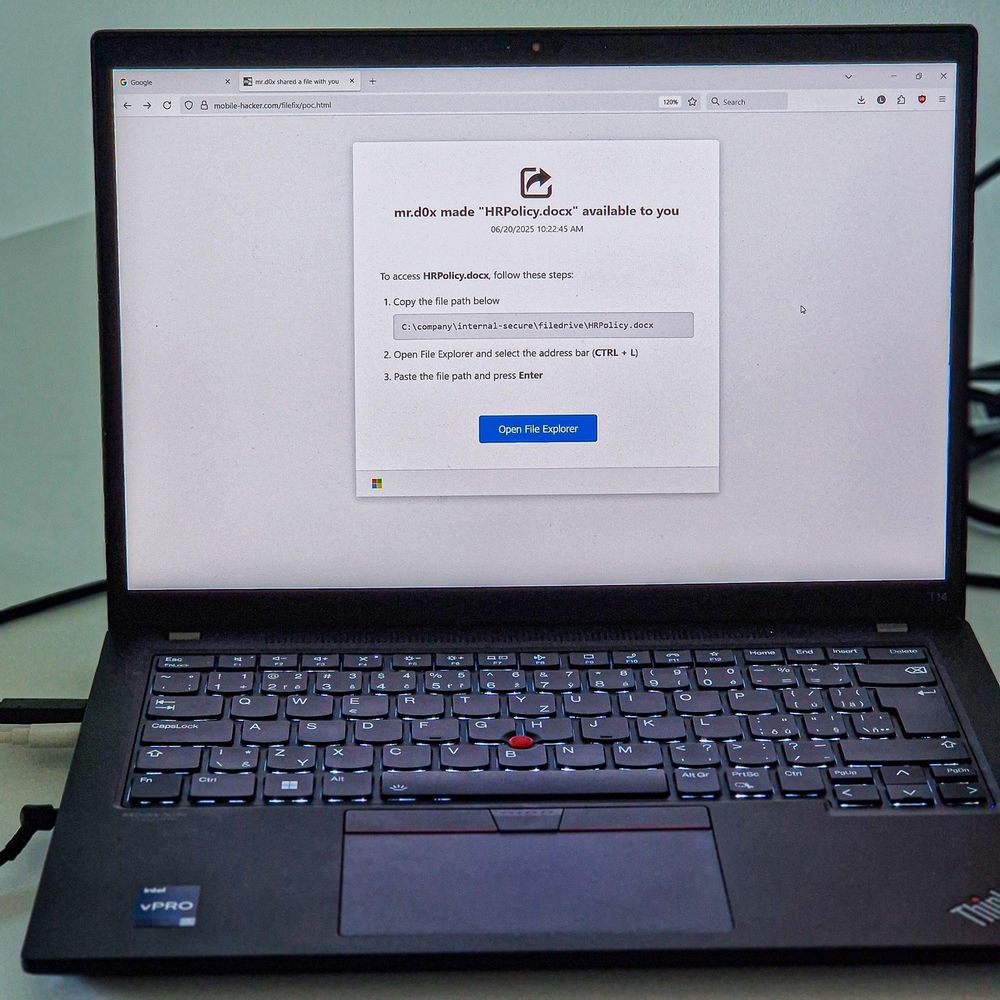
www.mobile-hacker.com/2025/06/24/i...
You can use non-rooted Android to unlock bootloader, run ADB commands, remove bloatware, flash ROM, or even root another Android
www.mobile-hacker.com/2025/06/16/h...

You can use non-rooted Android to unlock bootloader, run ADB commands, remove bloatware, flash ROM, or even root another Android
www.mobile-hacker.com/2025/06/16/h...
Scan networks, launch exploits, and test web apps—all from your phone
Bonus: includes a list of suggested WiFi adapters and SimpleUSB tool for identifying USB devices on the go
www.mobile-hacker.com/2025/06/12/s...
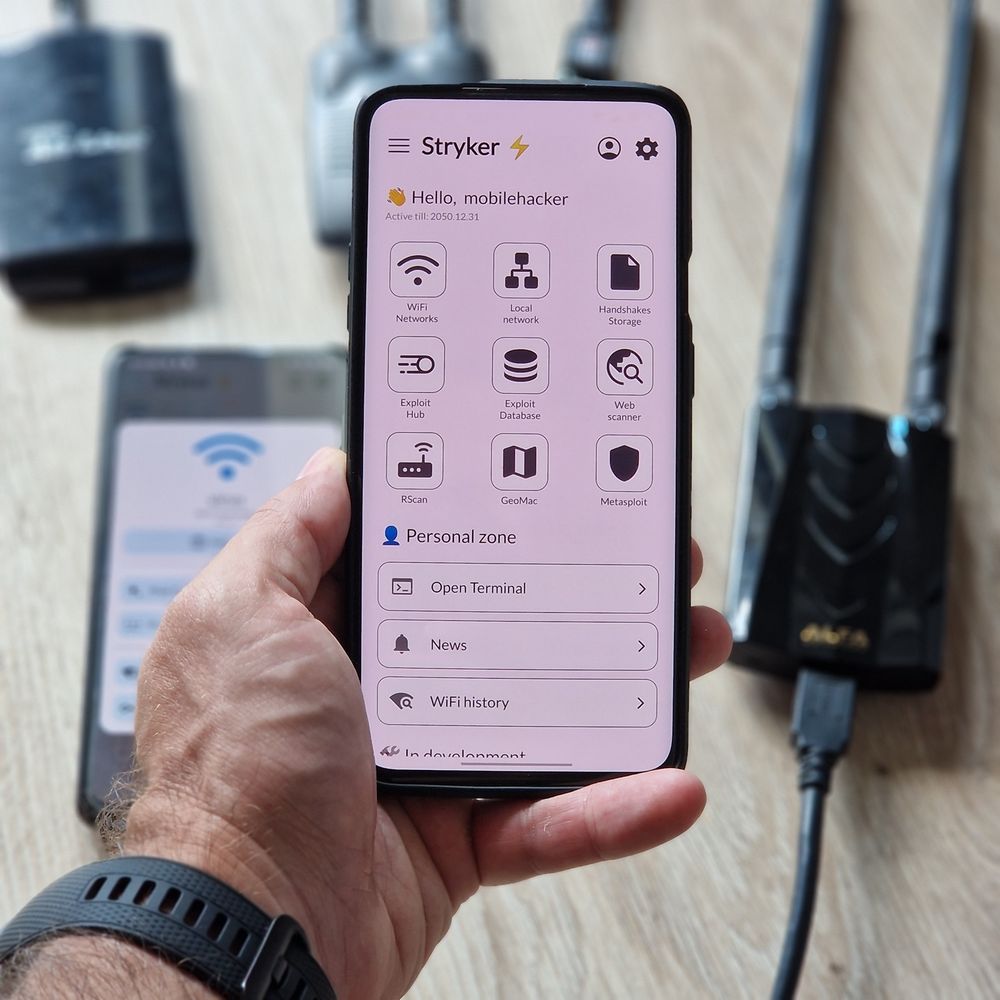
Scan networks, launch exploits, and test web apps—all from your phone
Bonus: includes a list of suggested WiFi adapters and SimpleUSB tool for identifying USB devices on the go
www.mobile-hacker.com/2025/06/12/s...
www.mobile-hacker.com/2025/06/10/s...
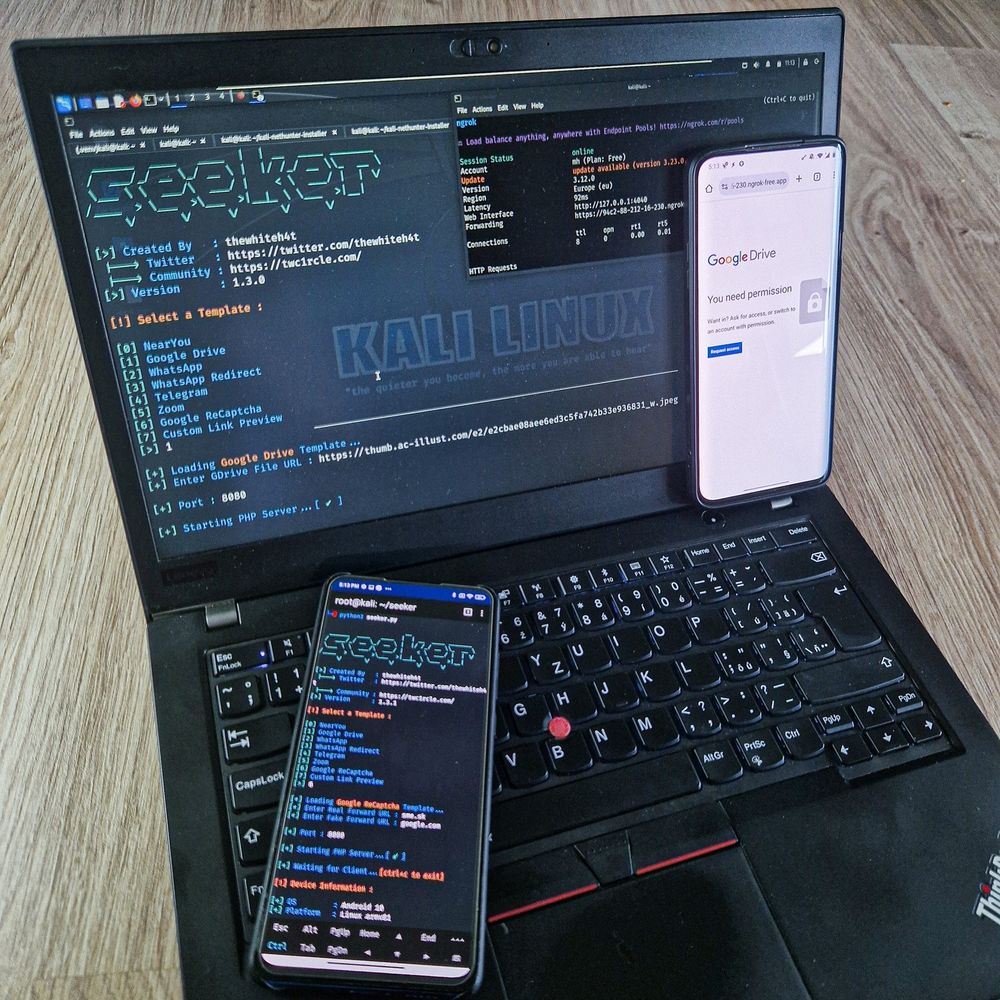
www.mobile-hacker.com/2025/06/10/s...
Tutorial on how to 3D-print a minimalist palmtop-style case for Google Pixel 3 XL and install NetHunter on it with custom kernel
www.mobile-hacker.com/2025/06/06/t...

Tutorial on how to 3D-print a minimalist palmtop-style case for Google Pixel 3 XL and install NetHunter on it with custom kernel
www.mobile-hacker.com/2025/06/06/t...
👉 Smartphone espionage doesn’t need expensive exploits. Cheap tools like SpyMax with targeted phishing a social engineering can breach even military targets - no 0-days required
www.mobile-hacker.com/2025/06/05/a...
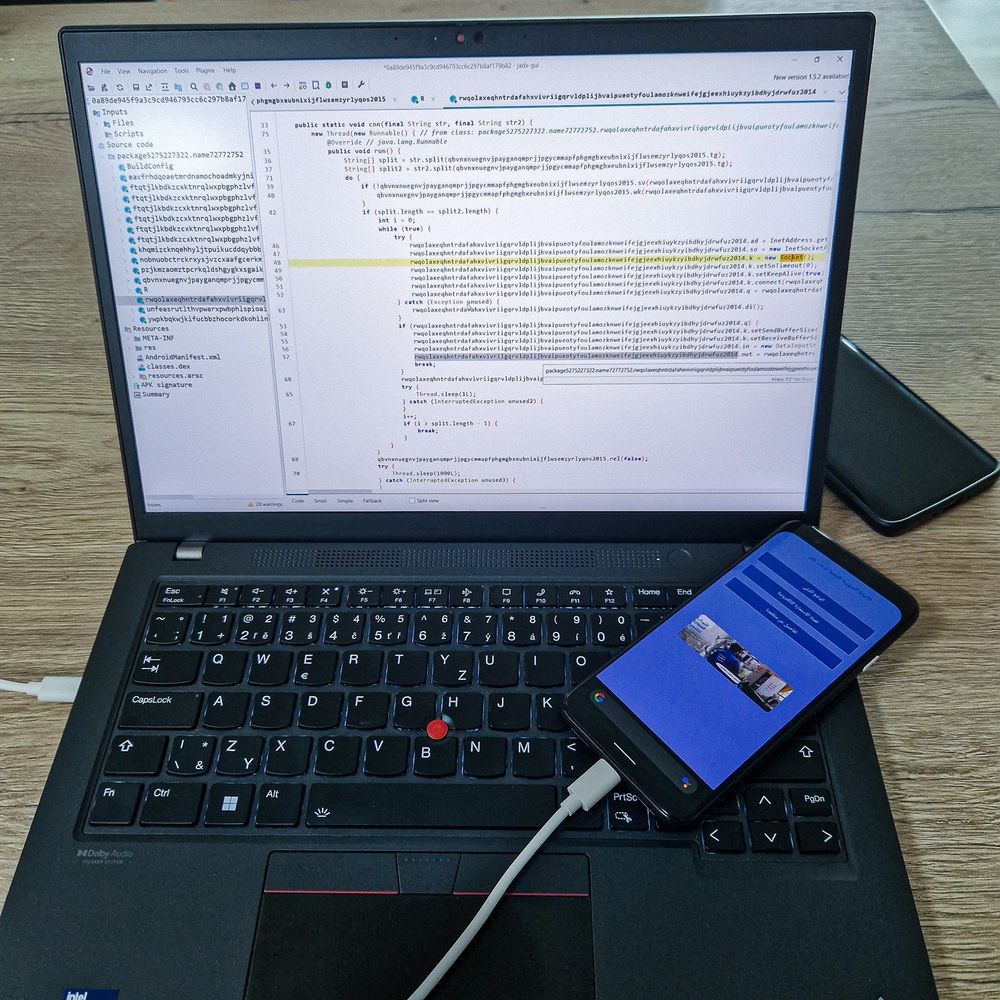
👉 Smartphone espionage doesn’t need expensive exploits. Cheap tools like SpyMax with targeted phishing a social engineering can breach even military targets - no 0-days required
www.mobile-hacker.com/2025/06/05/a...
3rd party app installed on a device could misuse vulnerabilities to:
✅perform factory reset of device
✅exfiltrate PIN code
✅inject an arbitrary intent with system-level privileges
www.mobile-hacker.com/2025/06/02/s...
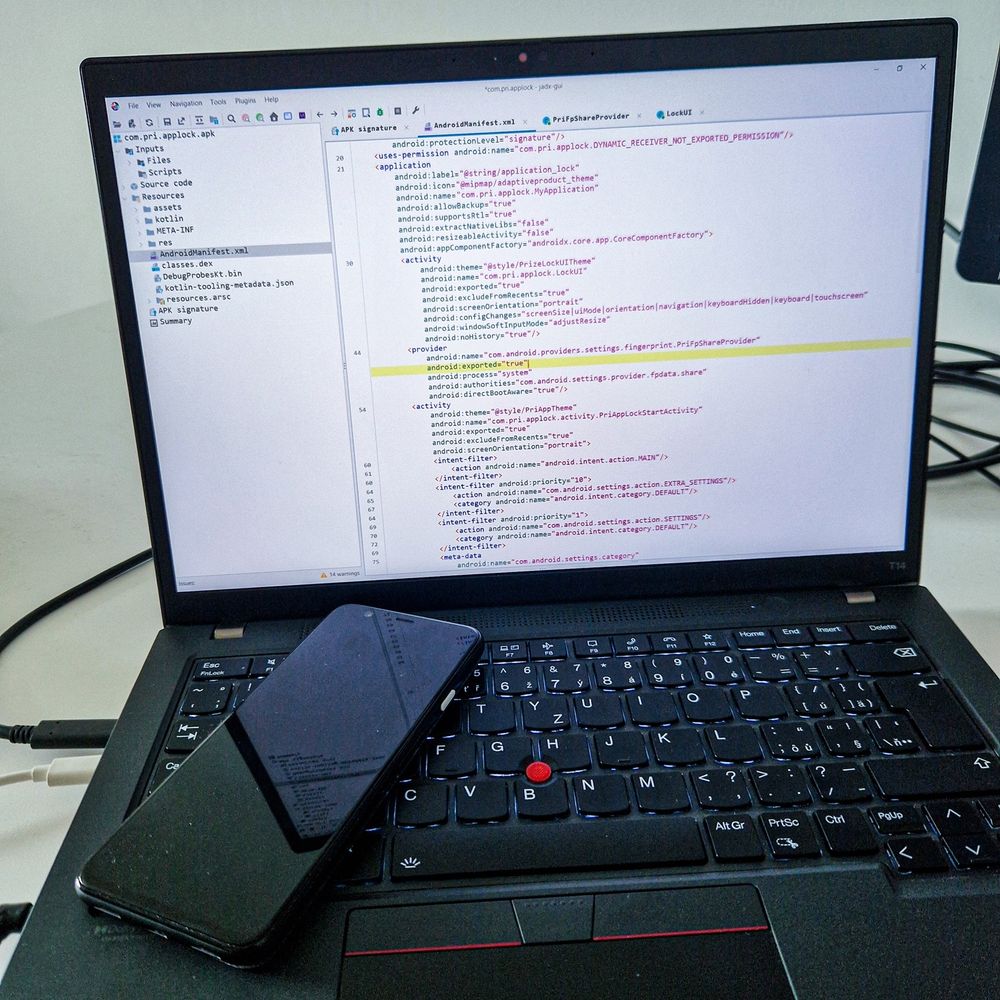
3rd party app installed on a device could misuse vulnerabilities to:
✅perform factory reset of device
✅exfiltrate PIN code
✅inject an arbitrary intent with system-level privileges
www.mobile-hacker.com/2025/06/02/s...
In a summary blog, you can find what's new with H4M, how to flash it, copy necessary data, and a couple of use-cases.
www.mobile-hacker.com/2025/05/19/h...

In a summary blog, you can find what's new with H4M, how to flash it, copy necessary data, and a couple of use-cases.
www.mobile-hacker.com/2025/05/19/h...
www.mobile-hacker.com/2025/03/31/f...

www.mobile-hacker.com/2025/03/31/f...
The exploit has been sold on underground forum since January 2025.
✅Don't install external players if requested by received corrupted video file on Telegram.
www.mobile-hacker.com/2025/03/05/e...
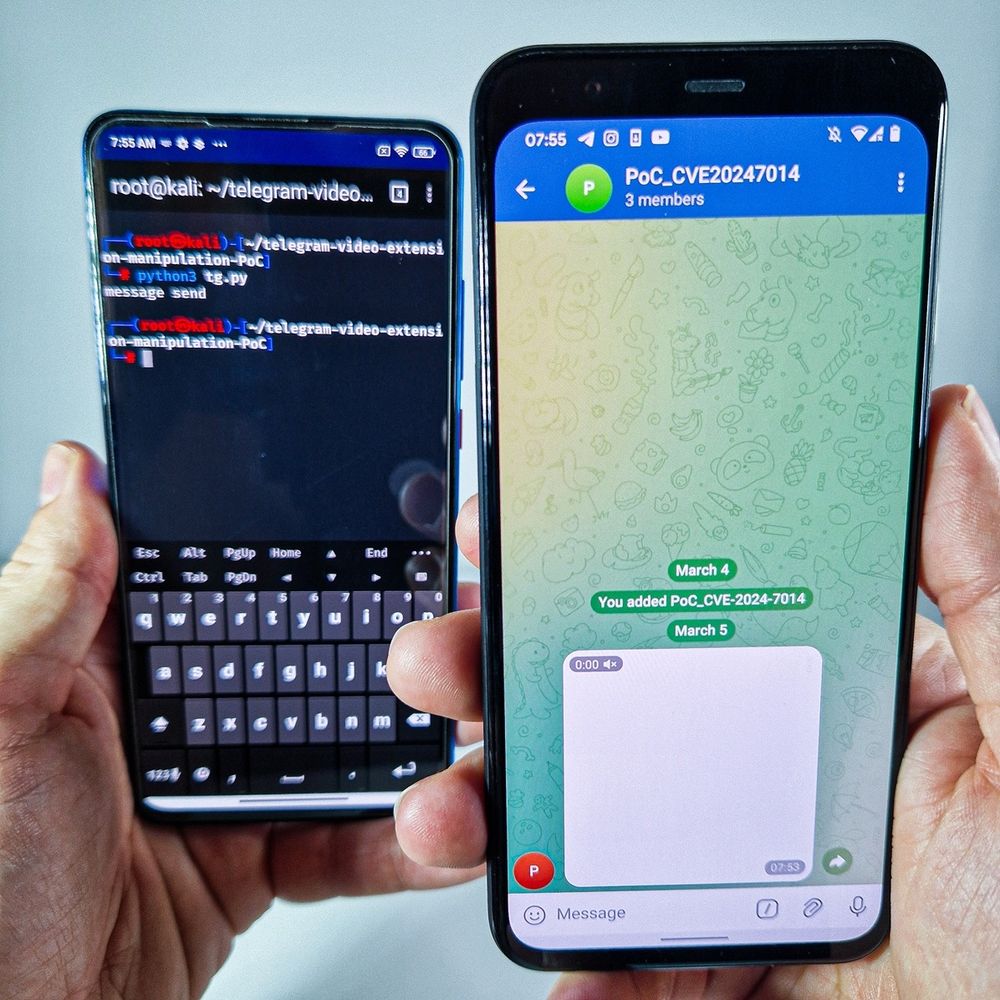
The exploit has been sold on underground forum since January 2025.
✅Don't install external players if requested by received corrupted video file on Telegram.
www.mobile-hacker.com/2025/03/05/e...
✅installation process
✅install drivers and switch output to touchscreen
✅allow auto-login
✅enable SSH as root
✅setup virtual keyboard
www.mobile-hacker.com/2025/02/26/b...

✅installation process
✅install drivers and switch output to touchscreen
✅allow auto-login
✅enable SSH as root
✅setup virtual keyboard
www.mobile-hacker.com/2025/02/26/b...
www.mobile-hacker.com/2025/02/21/b...

www.mobile-hacker.com/2025/02/21/b...
www.mobile-hacker.com/2025/02/11/e...

www.mobile-hacker.com/2025/02/11/e...
It is capable of remote keystroke injection, VNC, USB network adapter, EvilAP, Marauder, record microphone, controlled over web interface with fancy LCD screen
www.mobile-hacker.com/2025/01/24/u...

It is capable of remote keystroke injection, VNC, USB network adapter, EvilAP, Marauder, record microphone, controlled over web interface with fancy LCD screen
www.mobile-hacker.com/2025/01/24/u...
www.mobile-hacker.com/2025/01/09/b...
www.mobile-hacker.com/2025/01/09/b...
www.mobile-hacker.com/2024/12/23/e...
www.mobile-hacker.com/2024/12/23/e...

