
| Website: https://mizu.re
| Tool: https://github.com/kevin-mizu/domloggerpp
| Teams: @rhackgondins, @FlatNetworkOrg, @ECSC_TeamFrance
| From: https://twitter.com/kevin_mizu
This article mostly focuses on DOMPurify misconfigurations, especially hooks, that downgrade the sanitizer's protection (even in the latest version)!
Link 👇
mizu.re/post/explori...
1/2
It should be available on the stores in the coming hours.

It should be available on the stores in the coming hours.
Super excited to be part of this team, can't wait to see what crazy research is gonna come from this!
lab.ctbb.show/research/Exp...
Super excited to be part of this team, can't wait to see what crazy research is gonna come from this!
lab.ctbb.show/research/Exp...
In short, in non-strict mode, HTMLCollection items are not writable. This blocks property assignment, allowing unexpected values to be created 😄
👉 mizu.re/post/under-t...

In short, in non-strict mode, HTMLCollection items are not writable. This blocks property assignment, allowing unexpected values to be created 😄
👉 mizu.re/post/under-t...

This update fixes a lot of issues, including the historical DevTools bug on Chromium 🔥
It also brings full Caido session handling, which is going to be useful in the near future! 👀
👉 github.com/kevin-mizu/d...
1/2

This update fixes a lot of issues, including the historical DevTools bug on Chromium 🔥
It also brings full Caido session handling, which is going to be useful in the near future! 👀
👉 github.com/kevin-mizu/d...
1/2
I think it highlights how useful DOMLogger++ can be for tracking JS execution :D
👉 github.com/kevin-mizu/d...
1/3

I think it highlights how useful DOMLogger++ can be for tracking JS execution :D
👉 github.com/kevin-mizu/d...
1/3

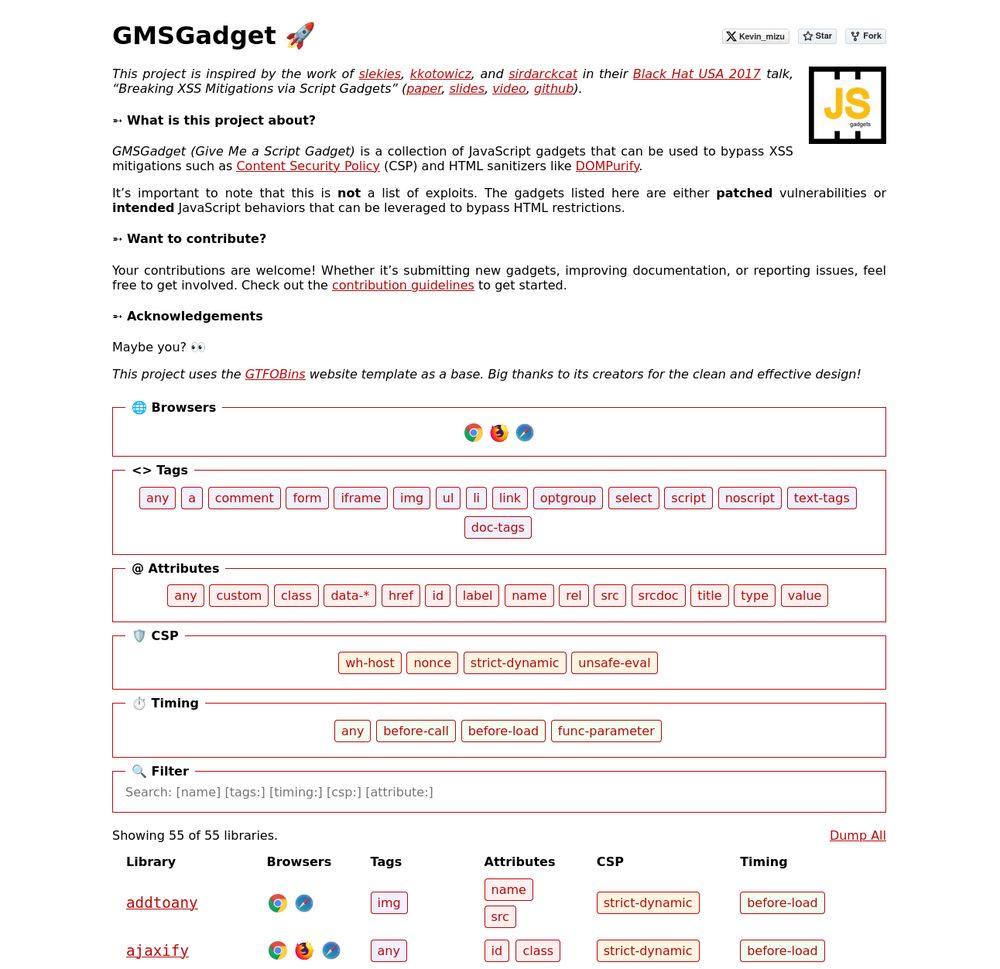
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4
The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇
gmsgadget.com
1/4

It's not a big deal, but it comes with a heavily hardened Docker setup. The bot also sends a lot of debugging information over the TCP socket (console logs, navigation), which makes remote debugging much easier! 🔎
👉 github.com/kevin-mizu/b...


It's not a big deal, but it comes with a heavily hardened Docker setup. The bot also sends a lot of debugging information over the TCP socket (console logs, navigation), which makes remote debugging much easier! 🔎
👉 github.com/kevin-mizu/b...
joaxcar.com/blog/2025/05...
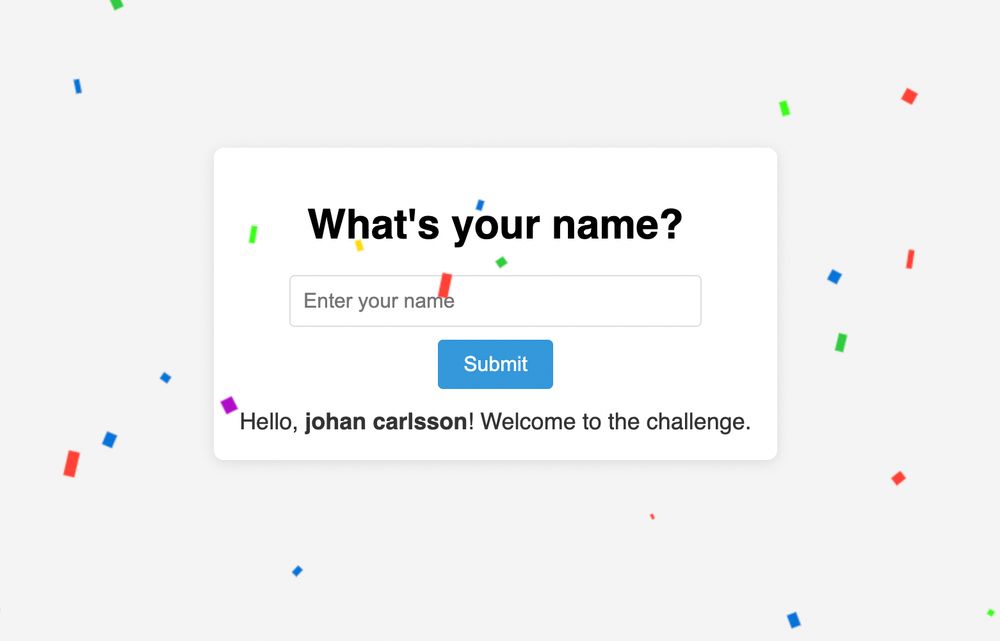
joaxcar.com/blog/2025/05...
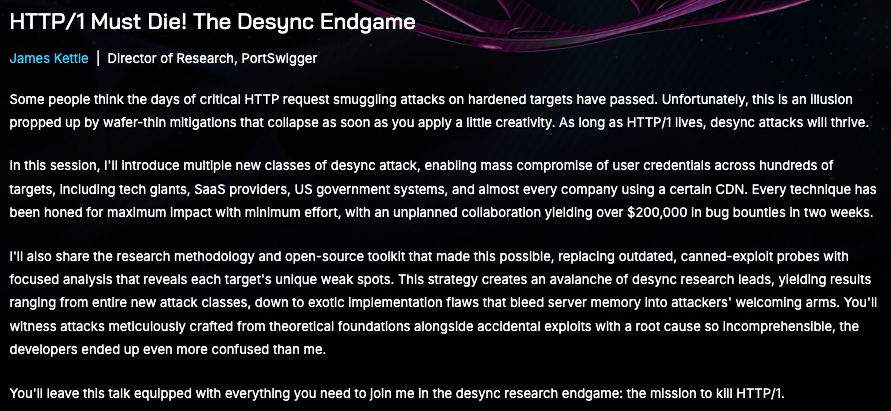
Think again, read our latest blog post!
Link in the comments👇
Think again, read our latest blog post!
Link in the comments👇
mizu.re/post/fcsc-2025…
Btw, like every year, all the challenges have also been added to hackropole.fr! 🚩
1/2

mizu.re/post/fcsc-2025…
Btw, like every year, all the challenges have also been added to hackropole.fr! 🚩
1/2
That tiny difference? It can turn a "non-exploitable" XSS into a real one.
Abuse boundary handling, bypass filters, and make your payload land.
thespanner.co.uk/making-the-u...

That tiny difference? It can turn a "non-exploitable" XSS into a real one.
Abuse boundary handling, bypass filters, and make your payload land.
thespanner.co.uk/making-the-u...
The CTF is solo and lasts 10 days, if you have some time, please give it a look 😁
Btw, even if you're not doing Web challenges, there are 100+ challenges in various categories, you should find something you like!

The CTF is solo and lasts 10 days, if you have some time, please give it a look 😁
Btw, even if you're not doing Web challenges, there are 100+ challenges in various categories, you should find something you like!
Watch how email parsing quirks turned into RCE in Joomla and critical access control bypasses across major platforms. See how these subtle flaws led to serious exploits!
www.youtube.com/watch?v=Uky4...

Watch how email parsing quirks turned into RCE in Joomla and critical access control bypasses across major platforms. See how these subtle flaws led to serious exploits!
www.youtube.com/watch?v=Uky4...
portswigger.net/research/sam...
portswigger.net/research/sam...
👉 bugzilla.mozilla.org/show_bug.cgi...
This allows to shift iframe rendering from one to another leading to a sandbox bypass 🔥
👉 mizu.re/post/an-18-y...
👉 bugzilla.mozilla.org/show_bug.cgi...
This allows to shift iframe rendering from one to another leading to a sandbox bypass 🔥
👉 mizu.re/post/an-18-y...
If you have some time this weekend, give it a try! 👀
👉 pwnme.phreaks.fr

If you have some time this weekend, give it a try! 👀
👉 pwnme.phreaks.fr
This update includes several UX improvements, such as syntax highlighting and new shortcuts. Major changes have been made to custom types and several annoying bugs have been fixed 🚀
👉 github.com/kevin-mizu/d...

This update includes several UX improvements, such as syntax highlighting and new shortcuts. Major changes have been made to custom types and several annoying bugs have been fixed 🚀
👉 github.com/kevin-mizu/d...

This article mostly focuses on DOMPurify misconfigurations, especially hooks, that downgrade the sanitizer's protection (even in the latest version)!
Link 👇
mizu.re/post/explori...
1/2
This article mostly focuses on DOMPurify misconfigurations, especially hooks, that downgrade the sanitizer's protection (even in the latest version)!
Link 👇
mizu.re/post/explori...
1/2
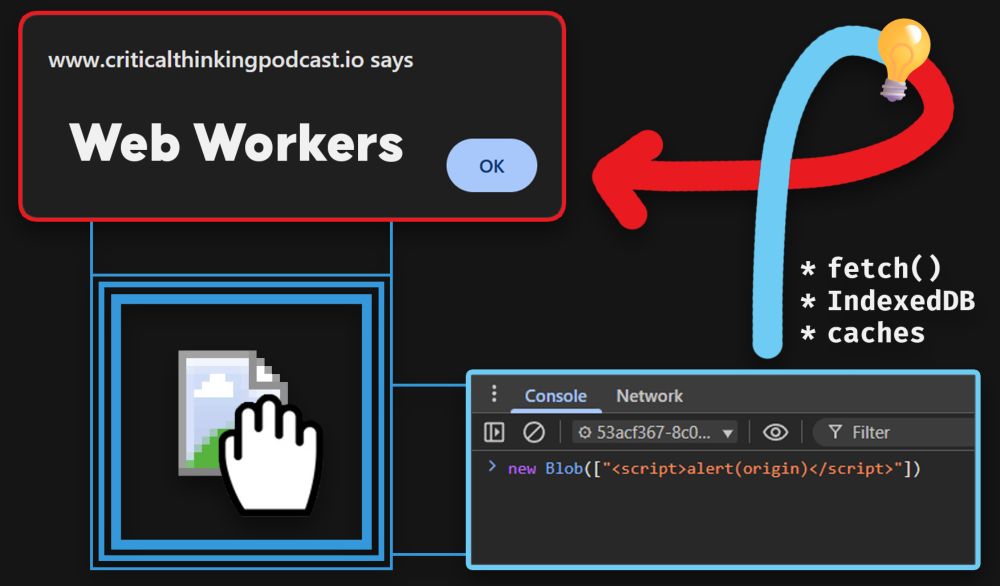
Before releasing it, I would like to share a small challenge 🚩
Challenge link 👇
challenges.mizu.re/xss_04.html
1/2

Before releasing it, I would like to share a small challenge 🚩
Challenge link 👇
challenges.mizu.re/xss_04.html
1/2


