
2. Tie specific malicious behavior to an IP address to see where it originated.
Both of these really fall under the vulnerability assessment category.
2. Tie specific malicious behavior to an IP address to see where it originated.
Both of these really fall under the vulnerability assessment category.
Network Detection and Response (NDR) provides two primary capabilities:
Network Detection and Response (NDR) provides two primary capabilities:
The primary goal of a CDR is to have a deep understanding of the environment.
(cont)
The primary goal of a CDR is to have a deep understanding of the environment.
(cont)
If you try it from a cloud shell or something that isn't local, you won't be able to hit it via localhost.
(cont)
If you try it from a cloud shell or something that isn't local, you won't be able to hit it via localhost.
(cont)
KoaPerf is a scanner that tells you based on performance, cost, and resource needs where you should deploy a containerized workload.
KoaPerf is a scanner that tells you based on performance, cost, and resource needs where you should deploy a containerized workload.
✅ Azure Kubernetes Service (AKS)
✅ Azure Container Apps (ACA)
✅ Azure Container Instance (ACI)
✅ Azure Kubernetes Service (AKS)
✅ Azure Container Apps (ACA)
✅ Azure Container Instance (ACI)
CICD pipelines are still the best way to get workloads and infrastructure initially deployed in an automated fashion.
I break down my thoughts about it in the link below.
buff.ly/3GWl2wy
CICD pipelines are still the best way to get workloads and infrastructure initially deployed in an automated fashion.
I break down my thoughts about it in the link below.
buff.ly/3GWl2wy
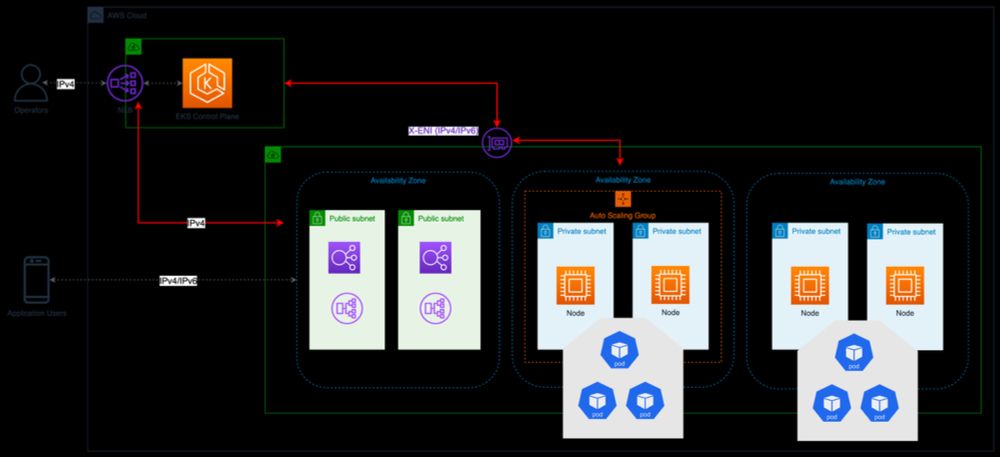
In this blog post, I break it all down.
buff.ly/WYBXgqU
In this blog post, I break it all down.
buff.ly/WYBXgqU
If they do, they can secure it.
If they do, they can secure it.
You must know the ins and outs in every capacity.
(cont)
You must know the ins and outs in every capacity.
(cont)

