
https://mgreen27.github.io
This is useful for hunting across browser artefacts - covers Chrome, Edge and Firefox
LINK: github.com/mgreen27/Det...
#DFIR

This is useful for hunting across browser artefacts - covers Chrome, Edge and Firefox
LINK: github.com/mgreen27/Det...
#DFIR
Expanded to look at installed applications, dns and running applications (process name and original/internal name of binaries on disk).
github.com/mgreen27/Det...
#dfir

Expanded to look at installed applications, dns and running applications (process name and original/internal name of binaries on disk).
github.com/mgreen27/Det...
#dfir
Im using it for targeted live strings extraction in Velociraptor and some cool workflow to drive things like building yara rules.
The screenshot shows VQL to dynamically generate a yara rule to preferred string size.


Im using it for targeted live strings extraction in Velociraptor and some cool workflow to drive things like building yara rules.
The screenshot shows VQL to dynamically generate a yara rule to preferred string size.
Rule: github.com/mgreen27/100...

Rule: github.com/mgreen27/100...
github.com/mgreen27/100...

github.com/mgreen27/100...
1. Packer related API strings and no import
Rule: github.com/mgreen27/100...
2. Downloader related API strings and no import
Rule: github.com/mgreen27/100...


1. Packer related API strings and no import
Rule: github.com/mgreen27/100...
2. Downloader related API strings and no import
Rule: github.com/mgreen27/100...



1. Microsoft Teams without a MS cert
2. Detect cert metadata
github.com/mgreen27/100...
3. Anomaly detection for PE files with large difference between physical and virtual size of a section
github.com/mgreen27/100...


1. Microsoft Teams without a MS cert
2. Detect cert metadata
github.com/mgreen27/100...
3. Anomaly detection for PE files with large difference between physical and virtual size of a section
github.com/mgreen27/100...
✅ @volexity.com
✅ @volatilityfoundation.org
✅ @attrc.bsky.social
✅ @rmettig.bsky.social
✅ @nolaforensix.bsky.social
➡️ more to come!
✅ @volexity.com
✅ @volatilityfoundation.org
✅ @attrc.bsky.social
✅ @rmettig.bsky.social
✅ @nolaforensix.bsky.social
➡️ more to come!
Rule: github.com/mgreen27/100...
VQL: github.com/mgreen27/100...



Rule: github.com/mgreen27/100...
VQL: github.com/mgreen27/100...
github.com/mgreen27/100...

github.com/mgreen27/100...
github.com/mgreen27/100...

github.com/mgreen27/100...
github.com/mgreen27/100...

github.com/mgreen27/100...
Rule: github.com/mgreen27/100...


Rule: github.com/mgreen27/100...
Rule: github.com/mgreen27/100...

Rule: github.com/mgreen27/100...
more yara-x > Dumping a RedCurl malware pe I saw Rich Header and thought I would give it a try.
Rule: github.com/mgreen27/100...


more yara-x > Dumping a RedCurl malware pe I saw Rich Header and thought I would give it a try.
Rule: github.com/mgreen27/100...
In an IR last week, we discovered and stopped an in progress exfil. This process rule detects the in memory renamed rclone - should be cross platform.
Rule: github.com/mgreen27/100...

In an IR last week, we discovered and stopped an in progress exfil. This process rule detects the in memory renamed rclone - should be cross platform.
Rule: github.com/mgreen27/100...
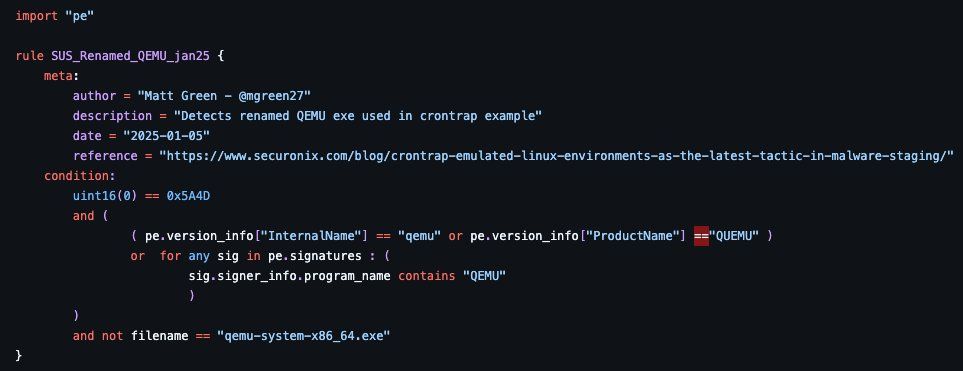
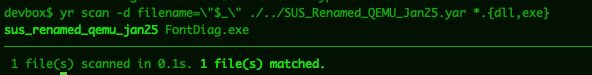
In the example rule I’m targeting the Korean font gulimche - ive added a few other system fonts for reference.
Rule: github.com/mgreen27/100...


In the example rule I’m targeting the Korean font gulimche - ive added a few other system fonts for reference.
Rule: github.com/mgreen27/100...
Rules: github.com/mgreen27/100...

Rules: github.com/mgreen27/100...
I initially tried to do a fancy for loop looking at zip attributes but performance was terrible so simple strings wins the day!
github.com/mgreen27/100...

I initially tried to do a fancy for loop looking at zip attributes but performance was terrible so simple strings wins the day!
github.com/mgreen27/100...
This week's #Metasploit wrap-up has Windows secrets dump improvements (and a JetBrains TeamCity login scanner, too!)
We're bad at poetry but good at shells. Check out the latest. www.rapid7.com/blog/post/20...

This week's #Metasploit wrap-up has Windows secrets dump improvements (and a JetBrains TeamCity login scanner, too!)
We're bad at poetry but good at shells. Check out the latest. www.rapid7.com/blog/post/20...

