1/3

1/3




www.welivesecurity.com/en/eset-rese...
🧵 1/6

www.welivesecurity.com/en/eset-rese...
🧵 1/6
#APT
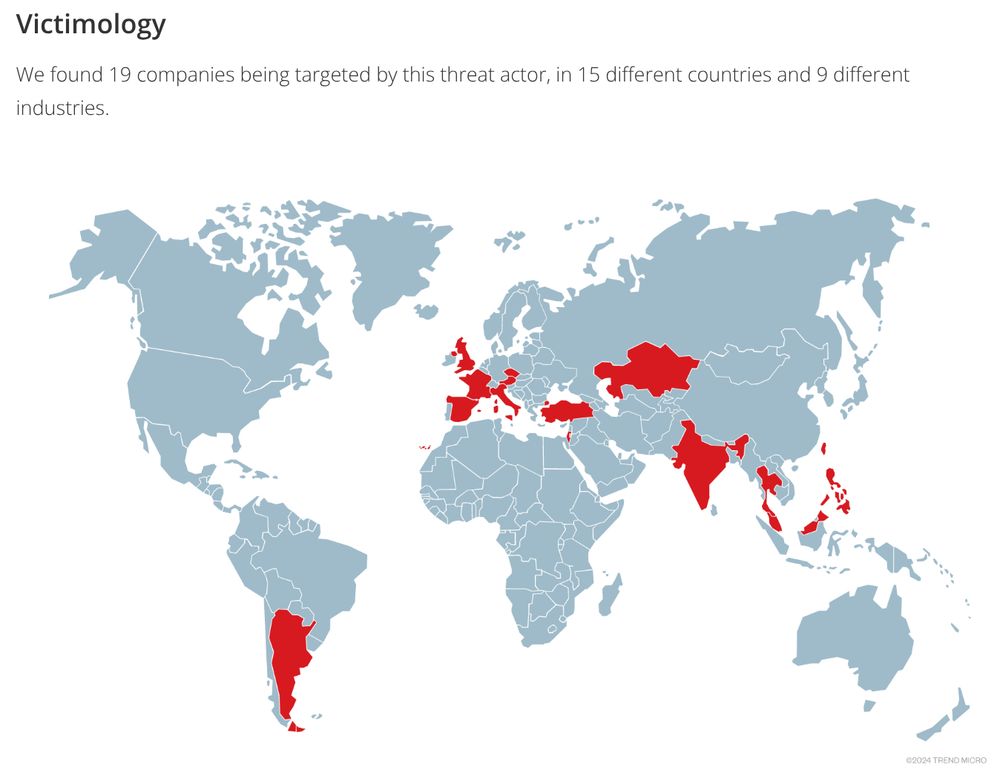
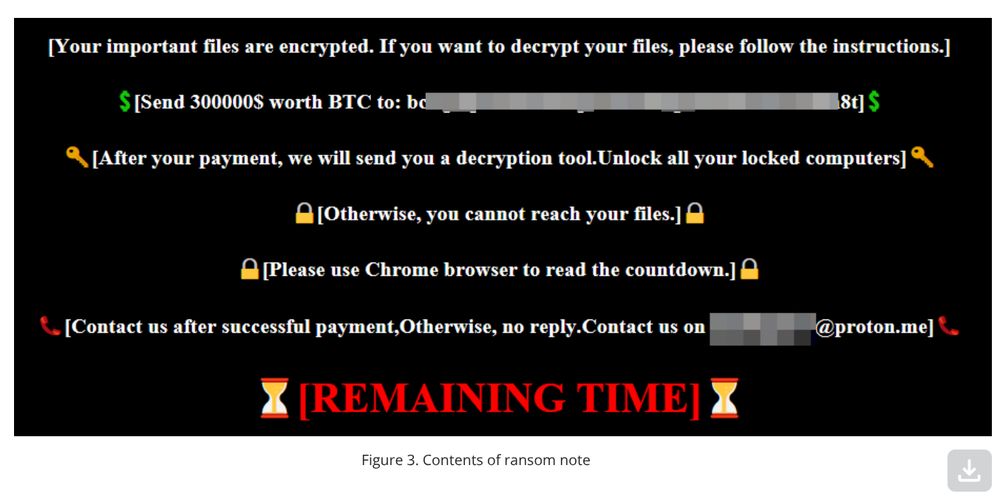
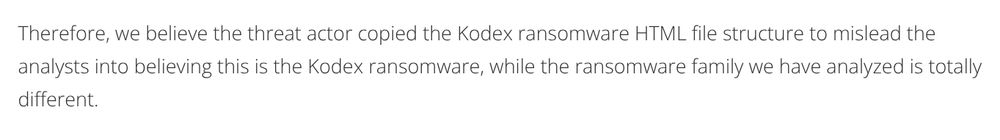
#APT
cloud.google.com/blog/topics/...
cloud.google.com/blog/topics/...
🧵1/6
🧵1/6

