Not affiliated with @portswigger.net ©️
Managed by @agarri.fr 🇫🇷
Additional free resources 🎁
http://hackademy.agarri.fr/freebies

Big thanks to CoreyD97 for the suggestion!
Big thanks to CoreyD97 for the suggestion!


github.com/CoreyD97/Ins...

github.com/CoreyD97/Ins...

The directories is especially useful in combination with something like ffuf, e.g. for /path/to/folder/file.txt will return the list
/path
/path/to
/path/to/folder

The directories is especially useful in combination with something like ffuf, e.g. for /path/to/folder/file.txt will return the list
/path
/path/to
/path/to/folder
The ugly UX where only opened panes were saved is gone (since at least EA 2025.9.1) 🗑️
The ugly UX where only opened panes were saved is gone (since at least EA 2025.9.1) 🗑️
www.youtube.com/watch?v=lHby...

www.youtube.com/watch?v=lHby...
youtu.be/bSt6E48mGuc
youtu.be/bSt6E48mGuc
Check out "resources/Scanner/jwt_secrets.txt". It contains over 100k passwords used by the passive scanner to decrypt JWT tokens 🗝️
And it works: that's how @evilpacket.net scored a $1500 bug affecting Cursor 💰
A range of emotions pushed me in various directions at once. What? no.!? yes!!!!!!! let's verify...
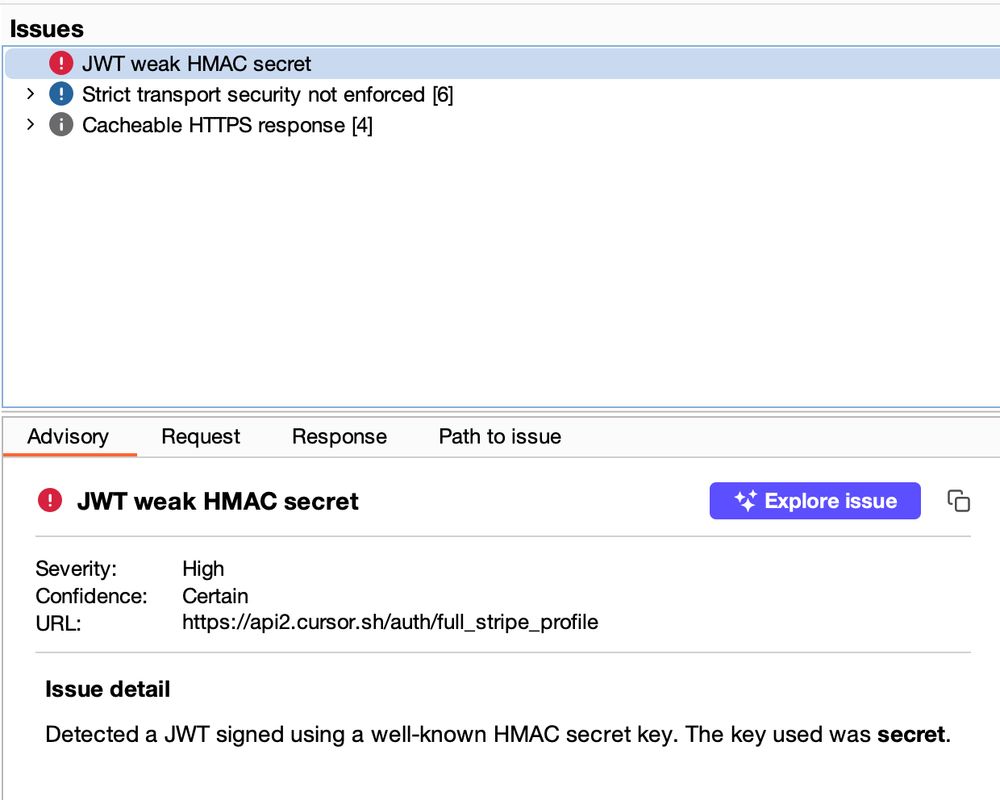
Check out "resources/Scanner/jwt_secrets.txt". It contains over 100k passwords used by the passive scanner to decrypt JWT tokens 🗝️
And it works: that's how @evilpacket.net scored a $1500 bug affecting Cursor 💰
aws.amazon.com/fr/security/...
aws.amazon.com/fr/security/...
curl -s portswigger.net/burp/release... | jq -r '[.ResultSet.Results[] | select(.releaseChannels[0] == "Early Adopter")][:2] | .[] | "=== Version EA v\(.version), \(.releaseDate) ===", "\(.content)"' | html2text
curl -s portswigger.net/burp/release... | jq -r '[.ResultSet.Results[] | select(.releaseChannels[0] == "Early Adopter")][:2] | .[] | "=== Version EA v\(.version), \(.releaseDate) ===", "\(.content)"' | html2text
The blog post is live! Read it here:
portswigger.net/research/web...

The blog post is live! Read it here:
portswigger.net/research/web...
www.linkedin.com/in/peter-wei...
Did I send him an invitation? OF COURSE!!
Has he accepted it? Not yet, but fingers crossed.
www.linkedin.com/in/peter-wei...
Did I send him an invitation? OF COURSE!!
Has he accepted it? Not yet, but fingers crossed.
Today, I used the embedded flag "(?-s)" to disable the DOTALL mode and be able to work one a single line 🔬
The goal was to append a string to the User-Agent header, and it now works perfectly 🎉

Today, I used the embedded flag "(?-s)" to disable the DOTALL mode and be able to work one a single line 🔬
The goal was to append a string to the User-Agent header, and it now works perfectly 🎉
Find out more here: blog.compass-security.com/2025/09/coll...
#AppSec #BurpSuite #Pentesting

Find out more here: blog.compass-security.com/2025/09/coll...
#AppSec #BurpSuite #Pentesting
All the bugs I reported have been patched, including the one where Repeater for Websocket wasn't showing the correspoding "response" in the bottom-right corner

All the bugs I reported have been patched, including the one where Repeater for Websocket wasn't showing the correspoding "response" in the bottom-right corner
All the bugs I reported have been patched, including the one where Repeater for Websocket wasn't showing the correspoding "response" in the bottom-right corner

All the bugs I reported have been patched, including the one where Repeater for Websocket wasn't showing the correspoding "response" in the bottom-right corner



