
https://github.com/marktsec




Advertised on underground forums with:
• Anti-kill, watchdog, persistence & injection modules
• AV evasion claims (C + ASM)
• Targets Windows 8.1 → Server 2025
• Seller offering only 5 “licenses”
#ThreatIntel #Cryptomining #InfoSec

Advertised on underground forums with:
• Anti-kill, watchdog, persistence & injection modules
• AV evasion claims (C + ASM)
• Targets Windows 8.1 → Server 2025
• Seller offering only 5 “licenses”
#ThreatIntel #Cryptomining #InfoSec
1. Girls phone voice callers to call CEOs/AI voice-spoofers.
2. Social-media “black ad” operators.
3. Offering a paid “Premium” panel with auto-activation via invoice.
#Nova #Ransomware #ThreatIntel #InfoSec




1. Girls phone voice callers to call CEOs/AI voice-spoofers.
2. Social-media “black ad” operators.
3. Offering a paid “Premium” panel with auto-activation via invoice.
#Nova #Ransomware #ThreatIntel #InfoSec

#infosec #ThreatIntel
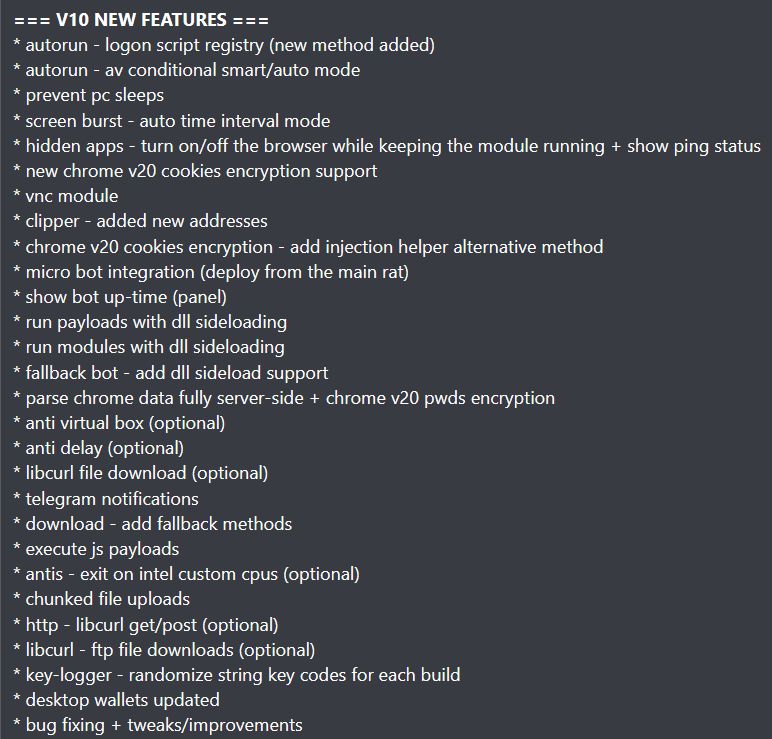
#infosec #ThreatIntel

#infosec #threatintel



#infosec #threatintel
Adds persistent self-restart (schtasks + registry), a silent mode that preserves filenames/timestamps, built-in network/domain spread (WMI/SC/PowerShell/etc.),
#ransomware #infosec #ThreatIntel

Adds persistent self-restart (schtasks + registry), a silent mode that preserves filenames/timestamps, built-in network/domain spread (WMI/SC/PowerShell/etc.),
#ransomware #infosec #ThreatIntel
#Ransomware #ThreatIntel #infosec

#Ransomware #ThreatIntel #infosec
#ThreatIntel #infosec #infostealer #vidar


#ThreatIntel #infosec #infostealer #vidar
#ransomware #threatintel #infosec

#ransomware #threatintel #infosec
#Infosec #ThreatIntel

#Infosec #ThreatIntel

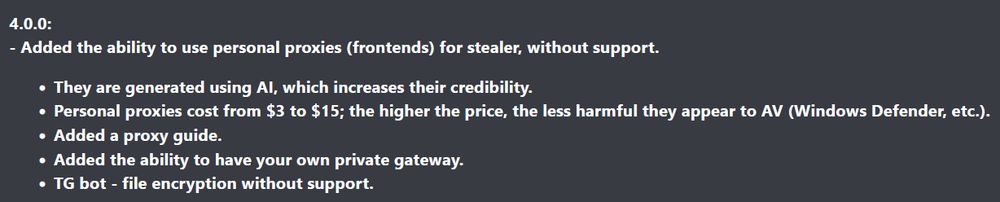




claims: remote unlock, VNC control, keylogging, OTP/SMS interception, wallet address swaps, live audio/video, persistence & anti-analysis.
#ThreatIntel #infosec


claims: remote unlock, VNC control, keylogging, OTP/SMS interception, wallet address swaps, live audio/video, persistence & anti-analysis.
#ThreatIntel #infosec
Key notes from dev:
🔓 Experimental app-bound decryption for Chromium browsers (no admin) now working.
🧩 Cookie decryption bugs fixed.
🛠️ Panel optimizations + cache clear/restart feature.
#ThreatIntel #Infostealer #infosec

Key notes from dev:
🔓 Experimental app-bound decryption for Chromium browsers (no admin) now working.
🧩 Cookie decryption bugs fixed.
🛠️ Panel optimizations + cache clear/restart feature.
#ThreatIntel #Infostealer #infosec
Key changes:
EN/RU panel toggle
"Human Check" to avoid sandboxes/honeypots
WPAD (auto-proxy) support → enables exfiltration from corp networks behind proxy configs
#ThreatIntel #infosec

Key changes:
EN/RU panel toggle
"Human Check" to avoid sandboxes/honeypots
WPAD (auto-proxy) support → enables exfiltration from corp networks behind proxy configs
#ThreatIntel #infosec
#infosec

#infosec
🔑 Features:
Clipboard hijacking via regex
Blockchain-based C2 for resilience
Unlimited .exe builder
TOX-only sales
#infosec #ThreatIntel #DarkWeb


🔑 Features:
Clipboard hijacking via regex
Blockchain-based C2 for resilience
Unlimited .exe builder
TOX-only sales
#infosec #ThreatIntel #DarkWeb





