• mTLS agents & listeners
• ChaCha20-Poly1305 encryption + DH key exchange
• HTTPS host reuse across HTTP & malleable listeners
• Customizable C# obfuscation via EmpireCompiler
• Major dependency upgrades & stability fixes
github.com/BC-SECURITY/...

• mTLS agents & listeners
• ChaCha20-Poly1305 encryption + DH key exchange
• HTTPS host reuse across HTTP & malleable listeners
• Customizable C# obfuscation via EmpireCompiler
• Major dependency upgrades & stability fixes
github.com/BC-SECURITY/...
Penetration Testing: Beyond the Basics, Offense for Defense, Kerberos Workshop all now on-demand🔗 training.redsiege.com
#hacking #infosec #cybersecurity #training


Penetration Testing: Beyond the Basics, Offense for Defense, Kerberos Workshop all now on-demand🔗 training.redsiege.com
#hacking #infosec #cybersecurity #training
So we had Troy Wojewoda join us to give you a introduction to Zeek log analysis, covering key concepts & practical applications.
Watch -- youtube.com/live/a2Cp6VY...
🔗 Register for webcasts, summits, & workshops -
poweredbybhis.com

So we had Troy Wojewoda join us to give you a introduction to Zeek log analysis, covering key concepts & practical applications.
Watch -- youtube.com/live/a2Cp6VY...
🔗 Register for webcasts, summits, & workshops -
poweredbybhis.com
This workshop will cover the basics of common offensive tools used by security professionals to identify vulnerabilities & exploit them.
Friday, May 30th 11am – 4pm ET
Register: www.antisyphontraining.com/course/works...

This workshop will cover the basics of common offensive tools used by security professionals to identify vulnerabilities & exploit them.
Friday, May 30th 11am – 4pm ET
Register: www.antisyphontraining.com/course/works...
An exploration of using flexicache for caching in Python.
https://daniel.feldroy.com/posts/2025-05-flexicache
An exploration of using flexicache for caching in Python.
https://daniel.feldroy.com/posts/2025-05-flexicache
Join Steve Borosh for a free webcast to learn how trusted Microsoft tools can be combined with .NET hijacking to create reverse SSH tunnels.
Read the technical details and register (Zoom): events.zoom.us/ev/AmH5cm3GK...

Join Steve Borosh for a free webcast to learn how trusted Microsoft tools can be combined with .NET hijacking to create reverse SSH tunnels.
Read the technical details and register (Zoom): events.zoom.us/ev/AmH5cm3GK...
He introduced us to Portswigger's Burp - a powerful tool for web application security testing. He covered the capabilities of Burp & demonstrated how it's used to identify vulnerabilities!
Watch - youtu.be/Gb7OQm5-Xdw?...

He introduced us to Portswigger's Burp - a powerful tool for web application security testing. He covered the capabilities of Burp & demonstrated how it's used to identify vulnerabilities!
Watch - youtu.be/Gb7OQm5-Xdw?...
Have you experienced this?
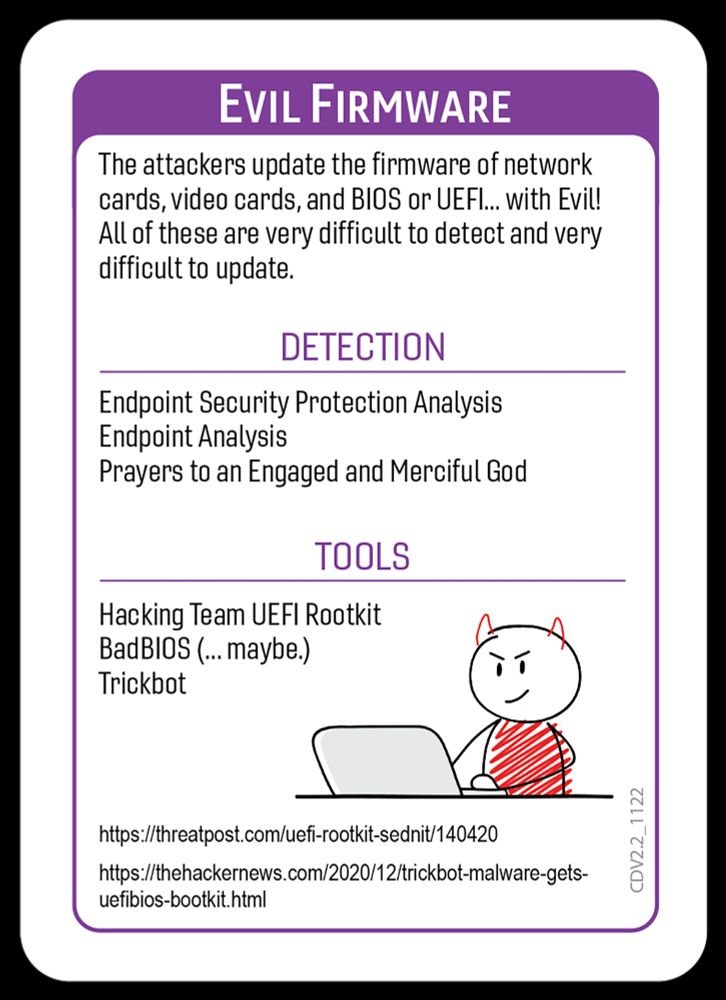
Deck: Core Deck 2.2
Attack/Procedure Type: Persistence
Attack/Procedure Evil Firmware
Play for free play.backdoorsandbreaches.com
Get physical card decks spearphish-general-store.myshopify.com/collections/...
Have you experienced this?
Deck: Core Deck 2.2
Attack/Procedure Type: Persistence
Attack/Procedure Evil Firmware
Play for free play.backdoorsandbreaches.com
Get physical card decks spearphish-general-store.myshopify.com/collections/...
academy.cyber5w.com/courses/C5W-...

academy.cyber5w.com/courses/C5W-...
* Professionally Evil API – Jennifer Shannon
* REAL Social Engineering – Michael Allen
* Defending M365 & Azure – Kevin Klingbile
* Professionally Evil API – Jennifer Shannon
* REAL Social Engineering – Michael Allen
* Defending M365 & Azure – Kevin Klingbile
Light at the End of the Dark Web w/ Joseph
What is the dark web
Join us for a free one-hour webcast with Joseph - Security Analyst, as he shares with you what he's discovered and learned about the Dark Web!
Feb 20th - 1PM ET
Register:
events.zoom.us/ev/AsVTPKKY3...

Light at the End of the Dark Web w/ Joseph
What is the dark web
Join us for a free one-hour webcast with Joseph - Security Analyst, as he shares with you what he's discovered and learned about the Dark Web!
Feb 20th - 1PM ET
Register:
events.zoom.us/ev/AsVTPKKY3...
Getting Started in Pentesting The Cloud–Azure youtu.be/u_3cV0pzptY?...
Cloud Pentest Apocalypse Part 1 - youtu.be/garHtW-bL7U?...
Cloud Pentest Apocalypse Part 2 |
youtu.be/HbX9d5v7VxY?...

Getting Started in Pentesting The Cloud–Azure youtu.be/u_3cV0pzptY?...
Cloud Pentest Apocalypse Part 1 - youtu.be/garHtW-bL7U?...
Cloud Pentest Apocalypse Part 2 |
youtu.be/HbX9d5v7VxY?...
To Enter: Like, Repost, and Leave a Comment
On January 12th, 1 winner will be chosen from LinkedIn and 1 winner will be chosen from Bluesky.
#DFIR #DigitalForensics #IncidentResponse

To Enter: Like, Repost, and Leave a Comment
On January 12th, 1 winner will be chosen from LinkedIn and 1 winner will be chosen from Bluesky.
#DFIR #DigitalForensics #IncidentResponse
🖥️ Hands-on labs with cloud VMs
👨🏫 Expert-led by @eric.zip & @whit.zip
🎯 Real-world hunting skills

Watch the full webcast here - www.youtube.com/live/uJi8GhG...



Watch the full webcast here - www.youtube.com/live/uJi8GhG...

