
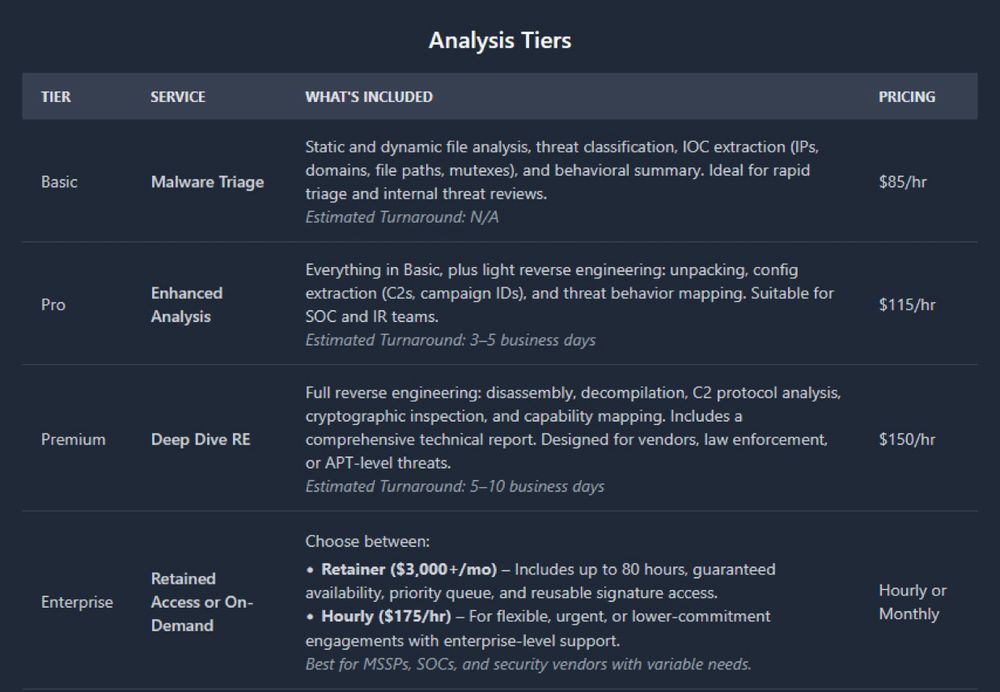
You can now hire one of our reverse engineers or malware analysts for tailored file analysis.
Go break stuff: malcore.io/hire-us
You can now hire one of our reverse engineers or malware analysts for tailored file analysis.
Go break stuff: malcore.io/hire-us
This course is perfect for those trying to start exploit dev and covers:
- Tooling
- Fuzzing
- Exploitation techniques
- And more!
You can take the course here: bible.malcore.io/readme/the-b...

This course is perfect for those trying to start exploit dev and covers:
- Tooling
- Fuzzing
- Exploitation techniques
- And more!
You can take the course here: bible.malcore.io/readme/the-b...
In order to get tax exempt status we need 500 USD. Please consider donating here: donorbox.org/malware-bibl...
All donations go straight to getting us tax exempt status and the Bible content.

In order to get tax exempt status we need 500 USD. Please consider donating here: donorbox.org/malware-bibl...
All donations go straight to getting us tax exempt status and the Bible content.
Unfortunately we have to start from scratch due to issues with the provider last time. I have a list of user emails so everyone that had an account will be sent an an invite email!

Unfortunately we have to start from scratch due to issues with the provider last time. I have a list of user emails so everyone that had an account will be sent an an invite email!
Use this as a replacement for xor to allow you to evade detection.

Use this as a replacement for xor to allow you to evade detection.
- Have Malcore’s analysis engine be able to use GPU
- Retrain the Malcore AI with billions of samples
- Make an endpoint specifically for detection using the Malcore AI to allow easy determination of file maliciousness
- Have Malcore’s analysis engine be able to use GPU
- Retrain the Malcore AI with billions of samples
- Make an endpoint specifically for detection using the Malcore AI to allow easy determination of file maliciousness


Today we are discussing API hammering!
API hammering is when malware repeatedly called benign APIs to try and detect delays caused by hooks or monitoring overhead.
This simple example shows how it can be done!

Today we are discussing API hammering!
API hammering is when malware repeatedly called benign APIs to try and detect delays caused by hooks or monitoring overhead.
This simple example shows how it can be done!
He deleted the post but you can find him @Sh0ckFR on X.
TL;DR: vxug giving away almost 100k in shit, this dude bitches about it.


He deleted the post but you can find him @Sh0ckFR on X.
TL;DR: vxug giving away almost 100k in shit, this dude bitches about it.
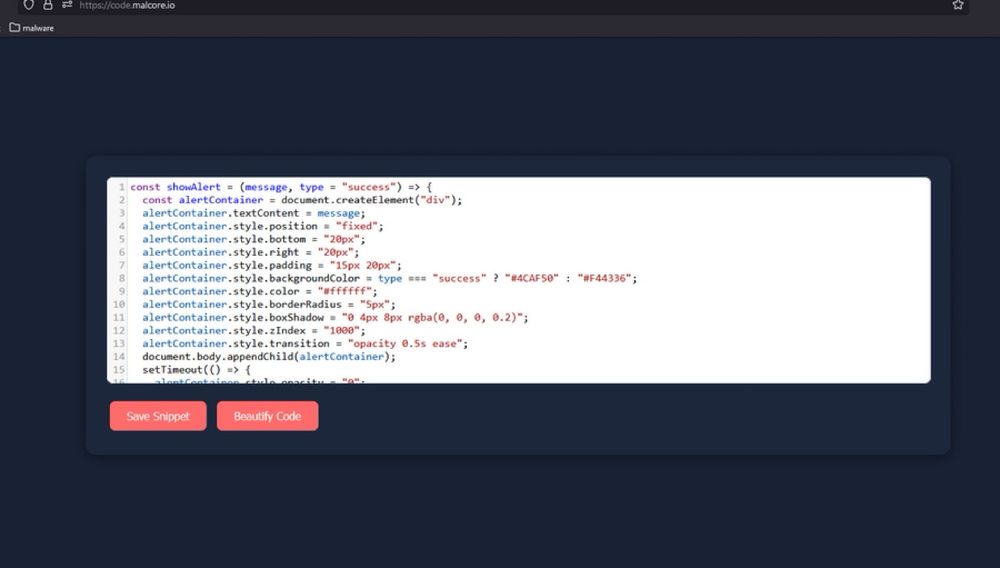
Features include:
- Full syntax highlighting
- Code is downloaded as a file
- Link is automatically copied to your clipboard
- Code beautification
- COMPLETELY FREE
Enjoy, and more to come later on!
Features include:
- Full syntax highlighting
- Code is downloaded as a file
- Link is automatically copied to your clipboard
- Code beautification
- COMPLETELY FREE
Enjoy, and more to come later on!
Find out more here: backyardbandwidth.com

Find out more here: backyardbandwidth.com
This simple example shows how you can create a file using a system call without using the Windows native CreateFile function, bypassing most API hooks AV or EDR have setup on user-mod API's!

This simple example shows how you can create a file using a system call without using the Windows native CreateFile function, bypassing most API hooks AV or EDR have setup on user-mod API's!
This SSD contains “embedded AI” to detect and prevent ransomware and other attacks.
Well my NDA expired so I’m gonna be reversing it, starting tomorrow!
Links below👇



This SSD contains “embedded AI” to detect and prevent ransomware and other attacks.
Well my NDA expired so I’m gonna be reversing it, starting tomorrow!
Links below👇

You can search, scroll to offsets, and view the disassembly of the file straight from your browser!
You can search, scroll to offsets, and view the disassembly of the file straight from your browser!
This example employees this technique to execute a function to mimic shellcode counting from 1-10.

This example employees this technique to execute a function to mimic shellcode counting from 1-10.
We are collabing with Cthulhu_Answers! 30% of ALL profits will go to a charity to help stop domestic violence: beckysfund.org
You can buy merch here: merch.malcore.io/collections/...
FREE SHIPPING WORLD WIDE!!

We are collabing with Cthulhu_Answers! 30% of ALL profits will go to a charity to help stop domestic violence: beckysfund.org
You can buy merch here: merch.malcore.io/collections/...
FREE SHIPPING WORLD WIDE!!
I own a data center!! It’s 150 per U per month starting.
You can learn more here: backyardbandwidth.com
We also have a VPN for 4.99/month as well send us an email for more info!

I own a data center!! It’s 150 per U per month starting.
You can learn more here: backyardbandwidth.com
We also have a VPN for 4.99/month as well send us an email for more info!







