
www.npr.org/2025/04/15/n...

www.npr.org/2025/04/15/n...
CISA’s cyber response team.
But senior officials told them to stand down — no report, no investigation.

CISA’s cyber response team.
But senior officials told them to stand down — no report, no investigation.
While preparing this disclosure, Berulis found a drone surveillance photo of himself taped to his front door with a threatening note.
This was just a few days ago.

While preparing this disclosure, Berulis found a drone surveillance photo of himself taped to his front door with a threatening note.
This was just a few days ago.
Azure billing jumped 8% — likely from short-lived high-cost compute used for data extraction, then deleted.

Azure billing jumped 8% — likely from short-lived high-cost compute used for data extraction, then deleted.
Someone downgraded Azure conditional access rules — MFA was off for mobile.
This was not approved and not logged.

Someone downgraded Azure conditional access rules — MFA was off for mobile.
This was not approved and not logged.
Within 15 minutes of DOGE accounts being created…
Attackers in Russia tried logging in using those new creds.
Correct usernames and passwords.
2 options here. The DOGE device was hacked. And I don't think I need to explain the 2nd.
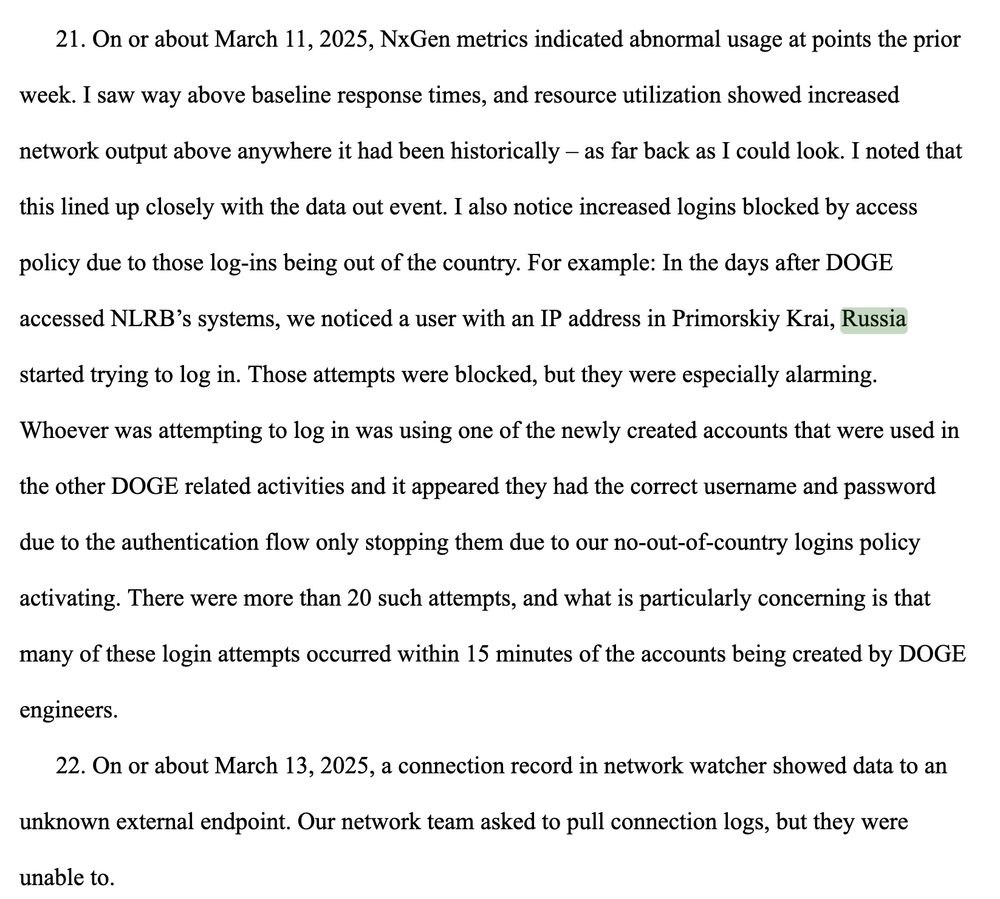
Within 15 minutes of DOGE accounts being created…
Attackers in Russia tried logging in using those new creds.
Correct usernames and passwords.
2 options here. The DOGE device was hacked. And I don't think I need to explain the 2nd.
They downloaded external GitHub tools like requests-ip-rotator and browserless — neither of which the agency uses.

They downloaded external GitHub tools like requests-ip-rotator and browserless — neither of which the agency uses.
10+ GB spike in outbound traffic
Exfiltration from NxGen, the NLRB's legal case database
No corresponding inbound traffic
Unusual ephemeral containers and expired storage tokens
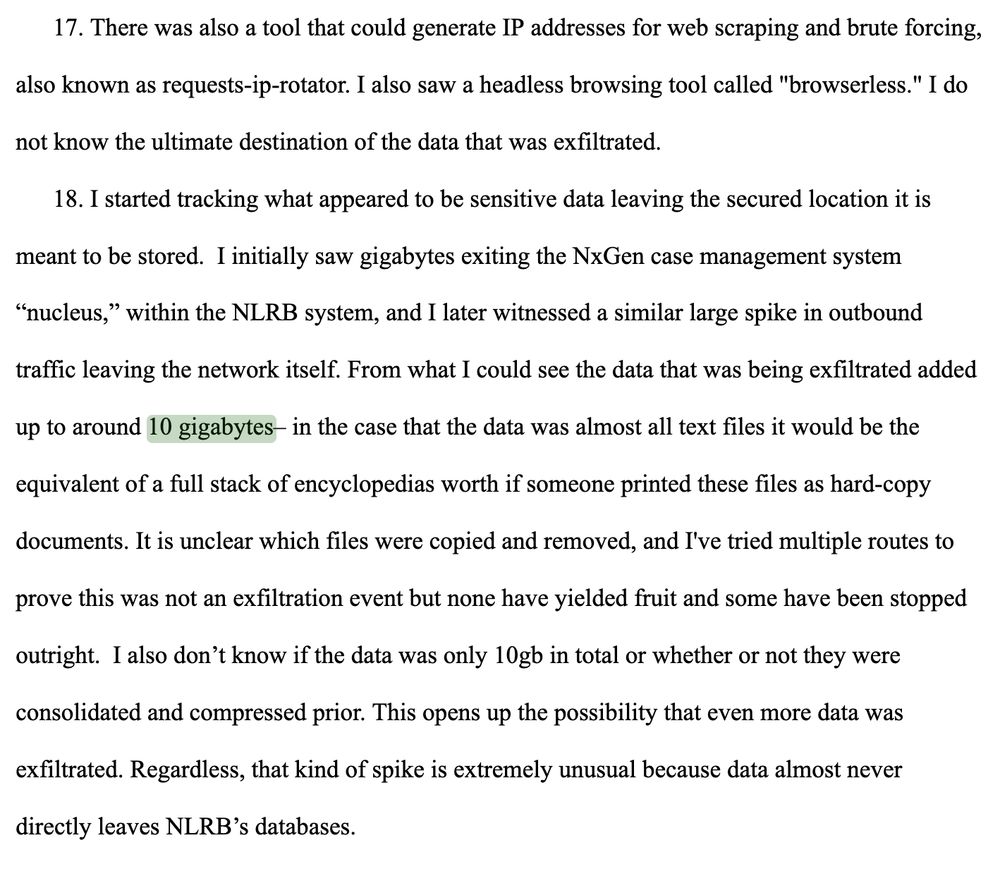
10+ GB spike in outbound traffic
Exfiltration from NxGen, the NLRB's legal case database
No corresponding inbound traffic
Unusual ephemeral containers and expired storage tokens
Berulis says DOGE demanded account creation with no recordkeeping.
They even ordered security controls bypassed and disabled tools like network watcher so their actions wouldn’t be logged.
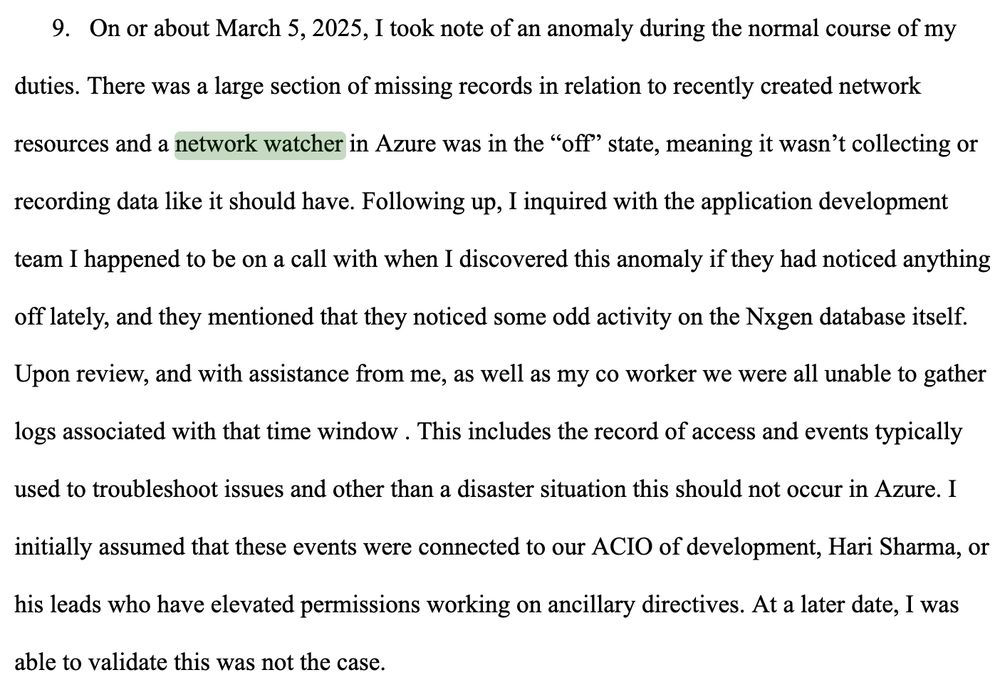
Berulis says DOGE demanded account creation with no recordkeeping.
They even ordered security controls bypassed and disabled tools like network watcher so their actions wouldn’t be logged.
Not auditor access. Not admin.
They were given “tenant owner” privileges in Azure — full control over the NLRB’s cloud, above the CIO himself.
This is never supposed to happen.

Not auditor access. Not admin.
They were given “tenant owner” privileges in Azure — full control over the NLRB’s cloud, above the CIO himself.
This is never supposed to happen.
Daniel Berulis — a senior DevSecOps architect at the National Labor Relations Board (NLRB), formerly with TS/SCI clearance.
He just told Congress the Department of Government Efficiency (DOGE) pulled off a covert cyber op inside a federal agency.

Daniel Berulis — a senior DevSecOps architect at the National Labor Relations Board (NLRB), formerly with TS/SCI clearance.
He just told Congress the Department of Government Efficiency (DOGE) pulled off a covert cyber op inside a federal agency.

