
More K8s news, events, jobs → https://kube.today
➜ https://ku.bz/dcDQCrkPn

➜ https://ku.bz/dcDQCrkPn
It supports SSH, HTTP, TCP, Prometheus metrics, Kubernetes deployment, and YAML config
➜ https://ku.bz/5665x_NRr

It supports SSH, HTTP, TCP, Prometheus metrics, Kubernetes deployment, and YAML config
➜ https://ku.bz/5665x_NRr
It integrates eBPF via Aya and manages routing logic via Kube-RS
It supports Gateway API objects like TCPRoute and UDPRoute, with KIND-based local testing only
➤ https://ku.bz/1cZxMK7Ck

It integrates eBPF via Aya and manages routing logic via Kube-RS
It supports Gateway API objects like TCPRoute and UDPRoute, with KIND-based local testing only
➤ https://ku.bz/1cZxMK7Ck
➤ https://ku.bz/ttgXTYdrZ

➤ https://ku.bz/ttgXTYdrZ
➤ https://ku.bz/jtT5DjB6h

➤ https://ku.bz/jtT5DjB6h
➤ https://ku.bz/zFRVy94dl

➤ https://ku.bz/zFRVy94dl
It integrates eBPF via Aya and manages routing logic via Kube-RS
It supports Gateway API objects like TCPRoute and UDPRoute, with KIND-based local testing only
➜ https://ku.bz/1cZxMK7Ck

It integrates eBPF via Aya and manages routing logic via Kube-RS
It supports Gateway API objects like TCPRoute and UDPRoute, with KIND-based local testing only
➜ https://ku.bz/1cZxMK7Ck
➜ https://ku.bz/ttgXTYdrZ

➜ https://ku.bz/ttgXTYdrZ
➜ https://ku.bz/jtT5DjB6h

➜ https://ku.bz/jtT5DjB6h
➤ https://ku.bz/WVcV9HKN7

➤ https://ku.bz/WVcV9HKN7
➤ https://ku.bz/QfzB7zPcf

➤ https://ku.bz/QfzB7zPcf
➜ https://ku.bz/zFRVy94dl

➜ https://ku.bz/zFRVy94dl
Attackers exploit prefix matching to pull images from fake subdomains like `myrepo.io.attacker.com`. Aqua shows real examples, a fixed v2 policy, and Trivy detection
➤ https://ku.bz/fYQfsmHt-

Attackers exploit prefix matching to pull images from fake subdomains like `myrepo.io.attacker.com`. Aqua shows real examples, a fixed v2 policy, and Trivy detection
➤ https://ku.bz/fYQfsmHt-
It fakes real services, captures attacker commands like docker ps or ls, and logs them for analysis via Grafana or fluentd
➤ https://ku.bz/W4M7dx2xy

It fakes real services, captures attacker commands like docker ps or ls, and logs them for analysis via Grafana or fluentd
➤ https://ku.bz/W4M7dx2xy
➜ https://ku.bz/WVcV9HKN7

➜ https://ku.bz/WVcV9HKN7
➜ https://ku.bz/QfzB7zPcf
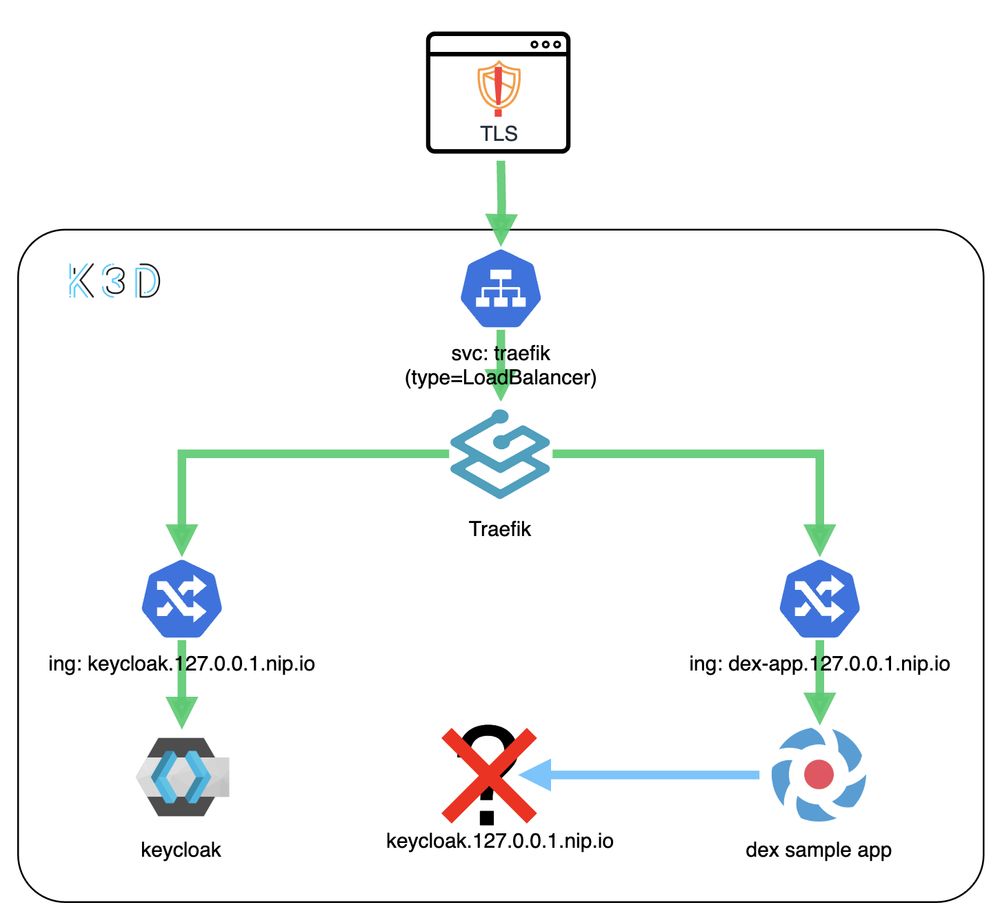
➜ https://ku.bz/QfzB7zPcf
Define specific RBAC rules at cluster and namespace levels, set expiration times, and automatically manage service accounts
➤ https://ku.bz/X5WpY7QD8

Define specific RBAC rules at cluster and namespace levels, set expiration times, and automatically manage service accounts
➤ https://ku.bz/X5WpY7QD8
Built by Telenor for on-prem clusters, it’s ideal for threat modelling or reviews
➤ https://ku.bz/4JP4Yvlmt

Built by Telenor for on-prem clusters, it’s ideal for threat modelling or reviews
➤ https://ku.bz/4JP4Yvlmt
➤ https://ku.bz/zTdnws-Fd

➤ https://ku.bz/zTdnws-Fd
It's built on the `CONFIG_LIVEPATCH` infrastructure and uses `ftrace` to reroute function calls at runtime
➤ https://ku.bz/-mXRJ9kzM

It's built on the `CONFIG_LIVEPATCH` infrastructure and uses `ftrace` to reroute function calls at runtime
➤ https://ku.bz/-mXRJ9kzM
Attackers exploit prefix matching to pull images from fake subdomains like `myrepo.io.attacker.com`. Aqua shows real examples, a fixed v2 policy, and Trivy detection
➜ https://ku.bz/fYQfsmHt-

Attackers exploit prefix matching to pull images from fake subdomains like `myrepo.io.attacker.com`. Aqua shows real examples, a fixed v2 policy, and Trivy detection
➜ https://ku.bz/fYQfsmHt-
It fakes real services, captures attacker commands like docker ps or ls, and logs them for analysis via Grafana or fluentd
➜ https://ku.bz/W4M7dx2xy

It fakes real services, captures attacker commands like docker ps or ls, and logs them for analysis via Grafana or fluentd
➜ https://ku.bz/W4M7dx2xy
It enforces resource compliance before persistence, supporting custom logic and dynamic updates cluster-wide
➤ https://ku.bz/C4jG7w4J6

It enforces resource compliance before persistence, supporting custom logic and dynamic updates cluster-wide
➤ https://ku.bz/C4jG7w4J6
It generates alerts or triggers webhooks on violations, enabling automated, real-time detection of misconfigurations and security issues
➤ https://ku.bz/4fssS2nJP

It generates alerts or triggers webhooks on violations, enabling automated, real-time detection of misconfigurations and security issues
➤ https://ku.bz/4fssS2nJP
➤ https://ku.bz/8hr1BhMf3

➤ https://ku.bz/8hr1BhMf3

