(v0.4.0) are released: github.com/hasherezade/... & github.com/hasherezade/... - A lot has changed in the new version, check it out!
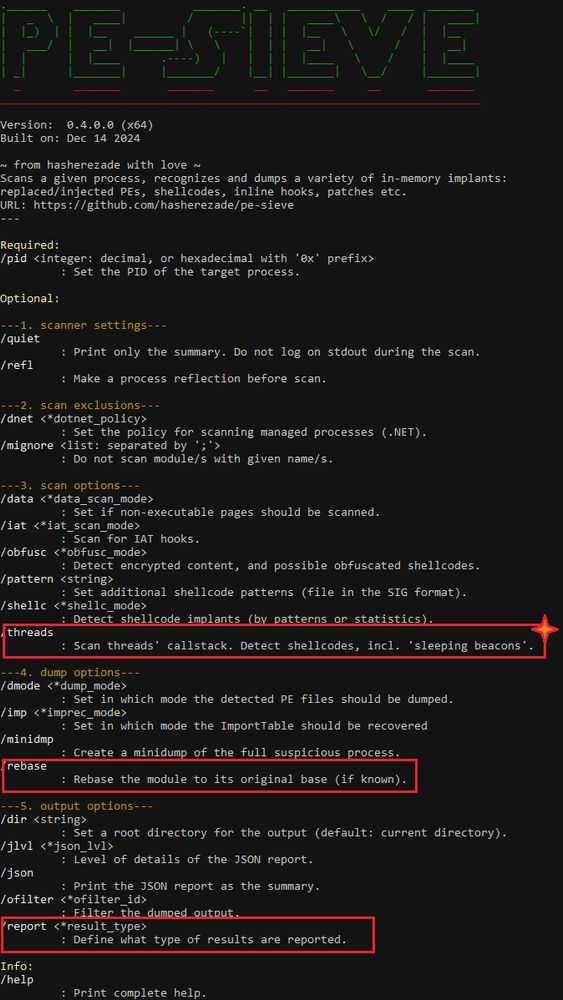
(v0.4.0) are released: github.com/hasherezade/... & github.com/hasherezade/... - A lot has changed in the new version, check it out!
lief.re/blog/2024-12...

lief.re/blog/2024-12...
🌐 urlhaus.abuse.ch/url/3189430/
This is the first major change since... ⬇️

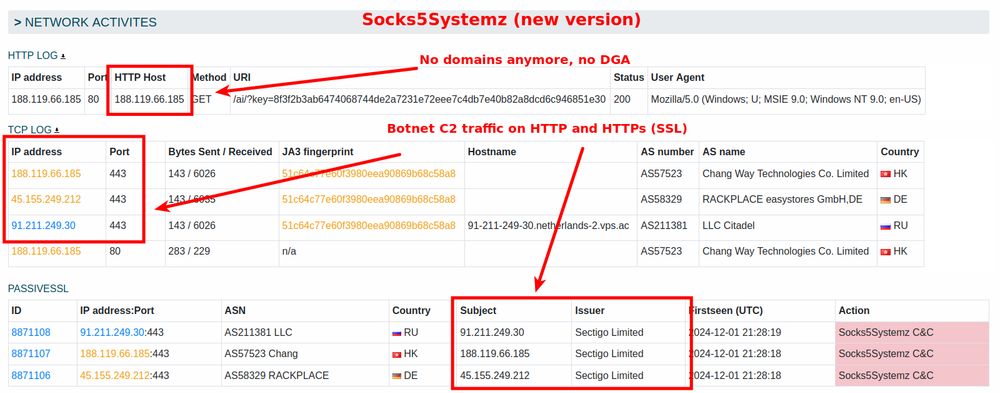
🌐 urlhaus.abuse.ch/url/3189430/
This is the first major change since... ⬇️
❄️🗓️ > radare.org/advent
Starting tomorrow, December 1st we will release every day a new article with general knowledge, tricks, scripts and challenges to solve with radare2 covering topics from #aor24 #reverseengineering

❄️🗓️ > radare.org/advent
Starting tomorrow, December 1st we will release every day a new article with general knowledge, tricks, scripts and challenges to solve with radare2 covering topics from #aor24 #reverseengineering
Code review anyone? :D
github.com/danielstocks...

Code review anyone? :D
github.com/danielstocks...
This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...

This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...
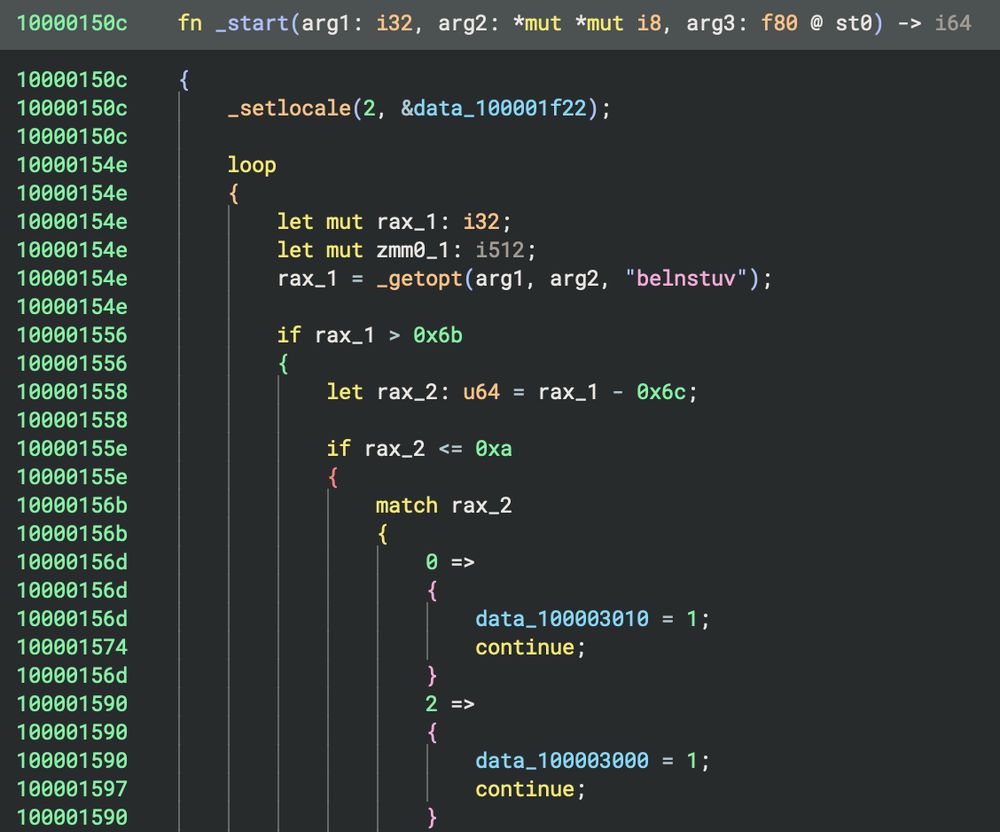
👀 video youtu.be/RsI8hNhsi_U
👉source github.com/ReEng101/Bin...
#radare2 #reverseengineering #BinaryDiffing

👀 video youtu.be/RsI8hNhsi_U
👉source github.com/ReEng101/Bin...
#radare2 #reverseengineering #BinaryDiffing


