
VIBE attribution to Handala because of similarities in TTPs and similarities to their HEAVYGRAM malware.
Ref: doublepulsar.com/handala-atte...
I don't need to reverse this shit to know... 🤡

VIBE attribution to Handala because of similarities in TTPs and similarities to their HEAVYGRAM malware.
Ref: doublepulsar.com/handala-atte...
I don't need to reverse this shit to know... 🤡
securityscanner.exe
7f4ded56abaacb2bf4649665ac259c7c
25f27131e8de91f8d6fdf9bfa1901577f992ce33
2afcac3231235b5cea0fc702d705ec76afec424a9cec820749b83b6299d1fe1b
This file is not signed by Check Point... it connects to Telegram and Dropbox for exfiltration and probably more...
securityscanner.exe
7f4ded56abaacb2bf4649665ac259c7c
25f27131e8de91f8d6fdf9bfa1901577f992ce33
2afcac3231235b5cea0fc702d705ec76afec424a9cec820749b83b6299d1fe1b
This file is not signed by Check Point... it connects to Telegram and Dropbox for exfiltration and probably more...
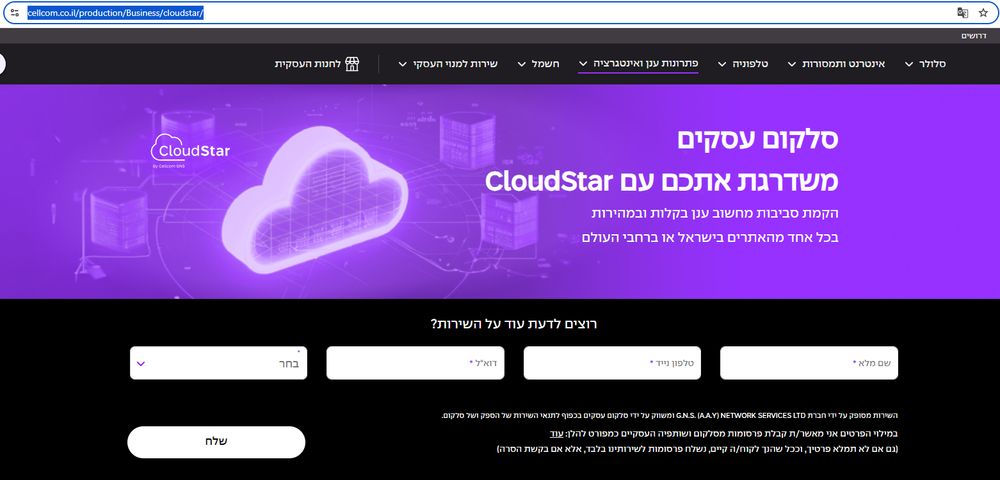
The PDF masquerades the download link to be a Check Point security tool.
The password for the RAR however is related to a cloud provider called cloudstar, but the small print say the service is provided by G.N.S.
cellcom.co.il/production/B...
The PDF masquerades the download link to be a Check Point security tool.
The password for the RAR however is related to a cloud provider called cloudstar, but the small print say the service is provided by G.N.S.
cellcom.co.il/production/B...
This onlyoffice subdomain is also mentioned by Proofpoint, but the shared key and content are different.
Test Projects.zip -> 8e7771ed1126b79c9a6a1093b2598282221cad8524c061943185272fbe58142d
This file is listed in the IOCs of the CP blog and might have been reused

This onlyoffice subdomain is also mentioned by Proofpoint, but the shared key and content are different.
Test Projects.zip -> 8e7771ed1126b79c9a6a1093b2598282221cad8524c061943185272fbe58142d
This file is listed in the IOCs of the CP blog and might have been reused

Part of this activity was reported by Check Point research.checkpoint.com/2025/nimbus-...

Part of this activity was reported by Check Point research.checkpoint.com/2025/nimbus-...
Iranian Kittens go O_o

Iranian Kittens go O_o

www.secureworks.com/blog/abraham...

www.secureworks.com/blog/abraham...
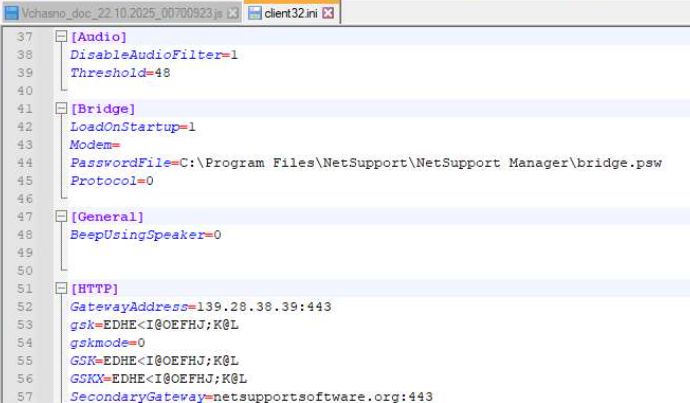
JS downloads NetSupport RAT and drops decoy PDF
Example C2 139.28.38.39


JS downloads NetSupport RAT and drops decoy PDF
Example C2 139.28.38.39
Example zip 0f6f4c1821b71ea73213b3b290b7e23b
Vchasno_doc_22.10.2025_0029.zip
Zip contains either just a JS payload or benign files with additional archives which contains the JS payload


Example zip 0f6f4c1821b71ea73213b3b290b7e23b
Vchasno_doc_22.10.2025_0029.zip
Zip contains either just a JS payload or benign files with additional archives which contains the JS payload
Example PDF ebb7c92f4d38510f8efab00eb8e2d9ad
Платіжне_доручення_22.10.2025_00684096792.pdf
PDF contains link to 2nd payload.
2nd stage payload is distributed among different hosting providers:
Dropbox
MS OneDrive
4sync



Example PDF ebb7c92f4d38510f8efab00eb8e2d9ad
Платіжне_доручення_22.10.2025_00684096792.pdf
PDF contains link to 2nd payload.
2nd stage payload is distributed among different hosting providers:
Dropbox
MS OneDrive
4sync
PDQ downloads ScreenConnect... 🤦♂️
microsoft_update000918u388.exe
0e99bfef05215614aafd6b9ea0e9f21b
9b04dadbb0a50d98d26abdccd27fb1696d78058e
77350a45d7d90766c03d690d7fd5178ba72af442e2ada60d9bdbb011c98189be
ScreenConnect C2: gripsmonga[.]sbs / 144.172.95.60
Hosted at: RouterHosting / Cloudzy 🤢🤮🤢
ScreenConnect C2: gripsmonga[.]sbs / 144.172.95.60
Hosted at: RouterHosting / Cloudzy 🤢🤮🤢



