Https://julismail.staff.telkomuniversity.ac.id
cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...
arcticwolf.com/resources/bl...

arcticwolf.com/resources/bl...
Check it out if you're at all interested in some novel Android Malware techniques!
(I also released a tool for some clever auto-decompilation)
Check it out if you're at all interested in some novel Android Malware techniques!
(I also released a tool for some clever auto-decompilation)
According to Russian video, the variants of malware on the Ukrainian drones are "burning out the USB port, preventing reflashing, or hijacking the repurposed FPV and revealing the operator location."
According to Russian video, the variants of malware on the Ukrainian drones are "burning out the USB port, preventing reflashing, or hijacking the repurposed FPV and revealing the operator location."

zw01f.github.io/malware%20an...
Would love to hear your feedback!
#RokRat #APT37 #ScarCruft #malware #APT #MalwareAnalysis #Infosec

zw01f.github.io/malware%20an...
Would love to hear your feedback!
#RokRat #APT37 #ScarCruft #malware #APT #MalwareAnalysis #Infosec
Socket exposes a typosquatting campaign delivering malware to Linux and macOS systems via malicious Go packages. Discover the…
#hackernews #news
Socket exposes a typosquatting campaign delivering malware to Linux and macOS systems via malicious Go packages. Discover the…
#hackernews #news
French security firm Sekoia has found the botnet's malware on Cisco and ASUS routers, and QNAP and Synology NAS devices.
blog.sekoia.io/polaredge-un...
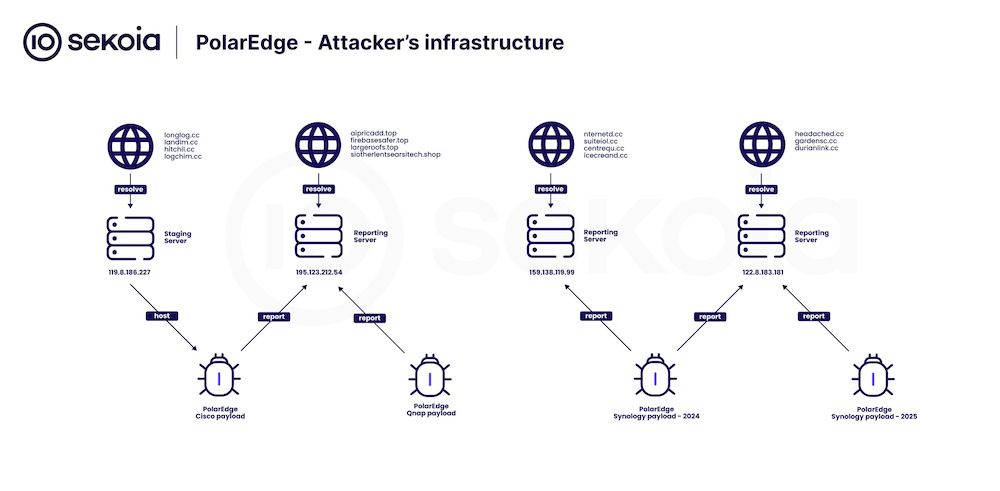
French security firm Sekoia has found the botnet's malware on Cisco and ASUS routers, and QNAP and Synology NAS devices.
blog.sekoia.io/polaredge-un...

Was used to target universities and government offices in North America and Asia, so prolly an APT here
unit42.paloaltonetworks.com/new-linux-ba...

Was used to target universities and government offices in North America and Asia, so prolly an APT here
unit42.paloaltonetworks.com/new-linux-ba...
@springernature.com
in Eurasip Journal
rdcu.be/eaq8k
@springernature.com
in Eurasip Journal
rdcu.be/eaq8k
www.welivesecurity.com/en/eset-rese...
🧵 1/6

www.welivesecurity.com/en/eset-rese...
🧵 1/6
Researchers found that the malware is Vidar, and the game was built on top of a pre-existing video game template.

Researchers found that the malware is Vidar, and the game was built on top of a pre-existing video game template.
Read: hackread.com/fake-poc-exp...
#CyberSecurity #InfoSec #Malware #Scam

Read: hackread.com/fake-poc-exp...
#CyberSecurity #InfoSec #Malware #Scam




www.zscaler.com/blogs/securi...

www.zscaler.com/blogs/securi...
✅ Implement #BYOVD safeguards and deploy expert rules to block vulnerable drivers.
Read: hackread.com/malware-avas...
#CyberSecurity #Malware #Avast

✅ Implement #BYOVD safeguards and deploy expert rules to block vulnerable drivers.
Read: hackread.com/malware-avas...
#CyberSecurity #Malware #Avast


