🧵




kASLR Internals and Evolution : r0keb.github.io/posts/kASLR-... credits @r0keb
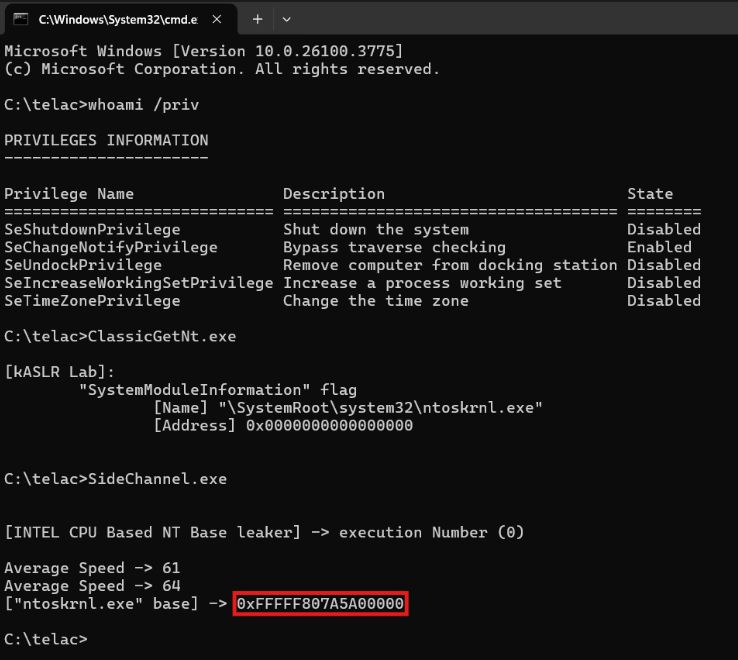
kASLR Internals and Evolution : r0keb.github.io/posts/kASLR-... credits @r0keb
www.youtube.com/watch?v=-3jx...
Great talk by Joe Bialek from MORSE team

www.youtube.com/watch?v=-3jx...
Great talk by Joe Bialek from MORSE team
linaro.atlassian.net/wiki/spaces/...
Boots in under a minute.
linaro.atlassian.net/wiki/spaces/...
Boots in under a minute.

Really appreciate the energy and collaboration with the @msys2org.bsky.social folks!
Really appreciate the energy and collaboration with the @msys2org.bsky.social folks!

