

For inputs without a form, that means you can hijack it into your own form with a form= attribute as an exception. From there you could submit your form to leak it.

For inputs without a form, that means you can hijack it into your own form with a form= attribute as an exception. From there you could submit your form to leak it.

* Opening the attacker's website with <a target="_blank">
* Submitting a form for CSRF
* Performing actions on the site to trigger other behavior

* Opening the attacker's website with <a target="_blank">
* Submitting a form for CSRF
* Performing actions on the site to trigger other behavior

![<iframe id="iframe" src="https://target.tld/dangling-object"></iframe>
<script>
iframe.onload = () => {
const object = iframe.contentWindow[0];
object.location = "about:blank"; // Navigate to our same-origin
const interval = setInterval(() => {
object.origin; // When it becomes same-origin
clearInterval(interval);
alert(object.name); // Leak its name (kept after navigation)
})
}
</script>](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:3ffrnqiish5sra3vcmrjox72/bafkreih6xpe7qtncthrcpirpiu3smiyhsixw56kh6vrjkf6p6jtewsjydm@jpeg)


1. Create a same-origin iframe
2. Make the iframe send a message to the target window
3. Instantly remove the iframe from the DOM
There's a few ways to get a reference to the target window from inside the iframe, but I used `opener` as follows:
1. Create a same-origin iframe
2. Make the iframe send a message to the target window
3. Instantly remove the iframe from the DOM
There's a few ways to get a reference to the target window from inside the iframe, but I used `opener` as follows:
groups.google.com/a/chromium.o...
They let an iframe send a message, and the iframe element was removed right after. By the time the receiver handles it the source is gone!
groups.google.com/a/chromium.o...
They let an iframe send a message, and the iframe element was removed right after. By the time the receiver handles it the source is gone!
developer.mozilla.org/en-US/docs/W...
So how could we potentially unset `event.source` for our malicious message?

developer.mozilla.org/en-US/docs/W...
So how could we potentially unset `event.source` for our malicious message?
Loosely comparing to undefined is all that's protecting it now?
Loosely comparing to undefined is all that's protecting it now?
bsky.app/profile/jori...
Don't let that HTML-injection of yours wait!
jorianwoltjer.com/blog/p/resea...
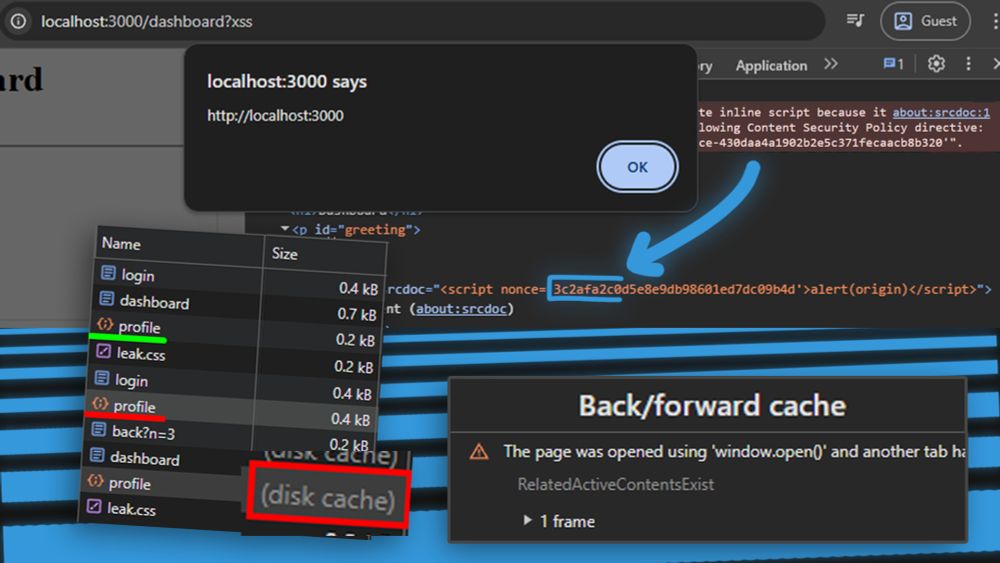
bsky.app/profile/jori...
Source JS:
gist.github.com/JorianWoltje...
URL:
greeting-chall.jorianwoltjer.com
Found a solution? Please DM to avoid spoilers, thanks!


